
*---*Dear Anonymous Legion chivalrous by publishing information ---
Anonymous .@Newsweek. Twitter account recovered after hack by #ISIS
-[http://www.newsweek.com/newsweek-twitter-account-hacked-isis-affiliated-group-305897 ]-&- Anonymous @·''Has modern Linux lost its way?''[ http://changelog.complete.org/archives/9299-has-modern-linux-lost-its-way-some-thoughts-on-jessie
 ]-&-Anonymous @YourAnonNews ·''War gaming for security cred ''[ http://hackaday.com/2015/02/08/war-gaming
]-&-Anonymous @YourAnonNews ·''War gaming for security cred ''[ http://hackaday.com/2015/02/08/war-gamingfor-security-cred/ ]-&-Anonymous*DIGITΛSHΛDØW @DigitaShadow·
#Anonymous hacktivists strike at ISIS.^^The Anonymous hero brother have big power to killed IS 'rogue-.....!''-
---*親愛的匿名軍團俠義通過發布信息---Anonymous.@Newsweek.'黑客通過#ISIS後的Twitter帳戶恢復'- [http://www.newsweek.com/newsweek-twitter-account-hacked-isis-affiliated-group-305897] - &-Anonymous@''有現代的Linux迷失了方向?''[HTTP:/ /changelog.complete.org/archives/9299-has-modern-linux-lost-its-way-some-thoughts-on-jessie] - & -匿名@YourAnonNews·“戰爭遊戲的安全名氣'[HTTP: //hackaday.com/2015/02/08/war-gaming-for-security-cred/] - &-佚名*DIGITΛSHΛDØW@DigitaShadow·#匿名黑客行動主義者打擊ISIS^^....!-
---*정보를 게시하여 기사도 친애하는 익명 군단---익명.@뉴스 위크. 트위터 계정은 #ISIS에 의해 해킹 후 복구- [http://www.newsweek.com/newsweek-twitter-account-hacked-isis-affiliated-group-305897] - 및 - 익명 @YourAnonNews·'''현대 리눅스가 길을 잃은 적이 있습니까?'[HTTP : / /changelog.complete.org/archives/9299-has-modern-linux-lost-its-way-some-thoughts-on-jessie] - & -'익명 @YourAnonNews ·'보안의 cred에 대한 전쟁 게임 '[HTTP : //hackaday.com/2015/02/08/war-gaming-for-security-cred/] - 및 - 익명*DIGITΛSHΛDØW @ DigitaShadow ·. #Anonymous hacktivists는 ISIS을 공격 ^^익명의 영웅 형제가 사망에 큰 힘을 가지고는 '불량 !'IS '-.....!-
**All the world city/ country lauguage**-
*Note This Sharing By Anonymous^^~
Newsweek Twitter Account Hacked By Group Claiming ISIS Affiliation
A Screenshot of the hacked Newsweek Twitter page.
Twitter.
Updated | At 10:45 a.m., the Newsweek
Twitter account, @Newsweek, was hacked by a group calling themselves the
"Cyber Caliphate." The group claimed to be affiliated with the Islamic
State (ISIS) and has previously hacked @Centcom, the Twitter account of
the United States Central Command, as well as the official Twitter
account of Taylor Swift. The Newsweek account remained hacked
for 14 minutes until 10:59 a.m., when Twitter's support team regained
control of the account at the publication's request.
"We can confirm that Newsweek's Twitter account was hacked this morning, and have since regained control of the account," Newsweek managing editor Kira Bindrim said in a statement. "We apologize to our readers for anything offensive that might have been sent from our account during that period, and are working to strengthen our newsroom security measures going forward."
During the hack, the @Newsweek account's profile picture and banner were changed to images of a masked man and the Black Standard flag, along with a message "Je su IS IS." The group tweeted out offensive messages threatening Michelle Obama and praising "cyber jihad." Images the hackers claimed were confidential were also tweeted, specifically from the Defense Cyber Investigations Training Academy and the Pentagon.
The FBI is investigating the hack as some of the tweets sent threatened the Obama family.
Also on Tuesday, ibtimes.com, the website of the International Business Times, was hacked by what appeared to be the same group. A subsidiary Newsweek Tumblr account, nwkarchivist.tumblr.com, was also briefly hacked. The official Twitter account of Latin Times was also hacked. Newsweek, International Business Times and Latin Times share a parent company, IBT Media.
"We can confirm that Newsweek's Twitter account was hacked this morning, and have since regained control of the account," Newsweek managing editor Kira Bindrim said in a statement. "We apologize to our readers for anything offensive that might have been sent from our account during that period, and are working to strengthen our newsroom security measures going forward."
During the hack, the @Newsweek account's profile picture and banner were changed to images of a masked man and the Black Standard flag, along with a message "Je su IS IS." The group tweeted out offensive messages threatening Michelle Obama and praising "cyber jihad." Images the hackers claimed were confidential were also tweeted, specifically from the Defense Cyber Investigations Training Academy and the Pentagon.
The FBI is investigating the hack as some of the tweets sent threatened the Obama family.
Also on Tuesday, ibtimes.com, the website of the International Business Times, was hacked by what appeared to be the same group. A subsidiary Newsweek Tumblr account, nwkarchivist.tumblr.com, was also briefly hacked. The official Twitter account of Latin Times was also hacked. Newsweek, International Business Times and Latin Times share a parent company, IBT Media.
==================================================
Has modern Linux lost its way? (Some thoughts on jessie)
February 9th, 2015
For years, I used to run Debian sid (unstable) on all my personal
machines. Laptops, workstations, sometimes even my personal servers
years ago ran sid. Sid was, as its name implies, unstable. Sometimes
things broke. But it wasn’t a big deal, because I could always get in
there and fix it fairly quickly, whatever it was. It was the price I
paid for the latest and greatest.For the last number of months, I’ve dealt with a small but annoying issue in jessie: None of Nautilus, Thunar, or digikam (yes, that represents Gnome, XFCE, and KDE) can mount USB drives I plug in anymore. I just get “Not authorized to perform operation.” I can, of course, still mount -o uid=1000 /dev/sdc1 /mnt, but I miss the convenience of doing it this way.
One jessie system I switched to systemd specifically to get around this problem. It worked, but I don’t know why. I haven’t had the time to switch my workstation, and frankly I am concerned about it.
Here’s the crux of the issue: I don’t even know where to start looking. I’ve googled this issue, and found all sorts of answers pointing to polkit, or dbus, or systemd-shim, or cgmanager, or lightdm, or XFCE, or… I found a bug report of this exact problem — Debian #760281, but it’s marked fixed, and nobody replied to my comment that I’m still seeing it.
Nowhere is it documented that a Digikam mounting issue should have me looking in polkit, let alone cgmanager. And even once I find those packages, their documentation suffers from Bad Unix Documentation Disease: talking about the nitty-gritty weeds view of something, without bothering to put it in context. Here is the mystifying heading for the cgmanager(8) manpage:
cgmanager is a daemon to manage cgroups. Programs and users can make D-Bus requests to administer cgroups over which they have privilege. To ensure that users may not exceed their privilege in manipulating cgroups, the cgroup manager accepts regular D-Bus requests only from tasks within its own process-id and user namespaces. For tasks in private namespaces (such as containers), SCM-enhanced D-Bus calls are available. Using these manually is not recommended. Rather, each container is advised to run a cgproxy, which will forward plain D-Bus requests as SCM-enhanced D-Bus requests to the host cgmanager.That’s about as comprehensible as Vorlon poetry to me. How is cgmanager started? What does “SCM-enhanced” mean? And I even know what a cgroup is.
This has been going on for months, which has me also wondering: is it only me? (Google certainly suggests it’s not, and there are plenty of hits for this exact problem with many distros, and some truly terrible advice out there to boot.) And if not, why is something so basic and obvious festering for so long? Have we built something that’s too complex to understand and debug?
This is, in my mind, orthogonal to the systemd question. I used to be able to say Linux was clean, logical, well put-together, and organized. I can’t really say this anymore. Users and groups are not really determinitive for permissions, now that we have things like polkit running around. (Yes, by the way, I am a member of plugdev.) Error messages are unhelpful (WHY was I not authorized?) and logs are nowhere to be found. Traditionally, one could twiddle who could mount devices via /etc/fstab lines and perhaps some sudo rules. Granted, you had to know where to look, but when you did, it was simple; only two pieces to fit together. I’ve even spent time figuring out where to look and STILL have no idea what to do.
systemd may help with some of this, and may hurt with some of it; but I see the problem more of an attitude of desktop environments to add features fast without really thinking of the implications. There is something to be said for slower progress if the result is higher quality.
Then as I was writing this, of course, my laptop started insisting that it needed the root password to suspend when I close the lid. And it’s running systemd. There’s another quagmire…
=========================================
War Gaming for Security Cred
On-the-job training is the best way to learn, and this is pretty close to it. Instead of providing an artificial avenue of learning the creators of OverTheWire have used the real thing to illustrate poor online security. You don’t “play the game” on an artificial web interface, you do it on legitimate platforms. The very first level (appropriately named Level 0) starts by figuring out how to connect to a system using Secure Shell (aka SSH). From there you’re prompted to use Linux command line tools to figure out where to go next.
Even veteran Linux/Security users should find this offering entertaining. The early stages are both quick and simple to navigate as an experienced admin while providing a welcoming learning platform for those who aren’t quite there yet. Work your way through a few different “servers” and before long your own knowledge will be tested. This isn’t a new platform, mentions of the site in Hackaday comments go back to 2010. But if you haven’t given it a try, Wargames is well worth adding to your weekend entertainment list.
[Thanks NightPhoenix]
========================================
 Anonymous
@YourAnonNews
Anonymous
@YourAnonNews
Five Best File Encryption Tools
Alan Henry
Keeping your personal data safe doesn't have to be difficult—as long as
you keep the sensitive stuff encrypted and under your control.
That's why this week we're looking at the five best file encryption
tools you can use to encrypt your data locally so only you have the key.
Earlier in the week we asked you for your favorite file encryption tools , and you gave us tons of great nominations, but as always, we only have room for the top five.
For the purposes of our roundup, we're focusing on desktop file
encryption tools - the ones you use on your own computer to encrypt your
own private data, not cloud services that promise to encrypt your data,
or business services that say they offer encryption.
The goal here is to find the best tools you can use to lock down your
sensitive files—whether they're photos, financial documents, personal
backups, or anything else—and keep them locked down so only you have the
key. For those unfamiliar with the topic, we have a great guide on how encryption works , and how you can use it to keep your own data safe.
With that out of the way, here are your top five, in no particular order:
VeraCrypt (Windows/OS X/Linux)

VeraCrypt is a fork of and a successor to TrueCrypt, which ceased
development last year (more on them later.) The development team claims
they've addressed some of the issues that were raised during TrueCrypt's
initial security audit, and like the original, it's free, with versions
available for Windows, OS X, and Linux.
If you're looking for a file encryption tool that works like and
reminds you of TrueCrypt but isn't exactly TrueCrypt, this is it.
VeraCrypt supports AES (the most commonly used), TwoFish, and Serpent
encryption ciphers, supports the creation of hidden, encrypted volumes
within other volumes.
Its code is available to review, although it's not strictly open source
(because so much of its codebase came from TrueCrypt.) The tool is also
under constant development, with regular security updates and an
independent audit in the planning stages (according to the developers.)
Those of you who nominated VeraCrypt praised it for being an on-the-fly
encryption tool, as in your files are only decrypted when they're
needed and they're encrypted at rest at all other times, and most
notably for being the spiritual (if not almost literal) successor to
TrueCrypt.
Many of you praised them for being a strong tool that's simple to use
and to the point, even if it's lacking a good-looking interface or tons
of bells and whistles.
You also noted that VeraCrypt may not support TrueCrypt files and
containers, but can convert them to its own format, which makes moving
to it easy. You can read more in its nomination thread here . AxCrypt (Windows)
AxCrypt is a free, open source, GNU GPL-licensed encryption tool for
Windows that prides itself on being simple, efficient, and easy to use.
It integrates nicely with the Windows shell, so you can right-click a
file to encrypt it, or even configure "timed," executable encryptions,
so the file is locked down for a specific period of time and will
self-decrypt later, or when its intended recipient gets it.
Files with AxCrypt can be decrypted on demand or kept decrypted while
they're in use, and then automatically re-encrypted when they're
modified or closed.
It's fast, too, and allows you to select an entire folder or just a
large group of files and encrypt them all with a single click. It's entirely a file encryption tool however, meaning creating encrypted volumes or drives is out of its capabilities.
It supports 128-bit AES encryption only, offers protection against
brute force cracking attempts, and is exceptionally lightweight (less
than 1MB.)
Those of you who nominated AxCrypt noted that it's really easy to use
and easy to integrate into your workflow, thanks to its shell support.
If you're eager for more options, it also has a ton of command line
options, so you can fire up the command prompt in Windows and perform
more complex actions—or multiple actions at once.
It may not support the strongest or most varied encryption methods
available, but if you're looking to keep your data safe from most
threats, it's a simple tool that can lend a little security that your
data—like files stored in the cloud on Dropbox or iCloud, for
example—are secure and convenient to access at the same time. You can read more in this nomination thread here and here . BitLocker (Windows)
BitLocker is a full-disk encryption tool built in to Windows Vista and
Windows 7 (Ultimate and Enterprise), and into Windows 8 (Pro and
Enterprise), as well as Windows Server (2008 and later).
It supports AES (128 and 256-bit) encryption, and while it's primarily
used for whole-disk encryption, it also supports encrypting other
volumes or a virtual drive that can be opened and accessed like any
other drive on your computer.
It supports multiple authentication mechanisms, including traditional
password and PINs, a USB "key," and the more controversial Trusted Platform Module
(TPM) technology (that uses hardware to integrate keys into devices)
that makes encryption and decryption transparent to the user but also
comes with a host of its own issues.
Either way, BitLocker's integration with Windows (specifically Windows 8
Pro) makes it accessible to many people, and a viable disk encryption
tool for individuals looking to protect their data if their laptop or
hard drives are lost or stolen, in case their computers are compromised,
or a business looking to secure data in the field.
Of course, it goes without saying that BitLocker was a contentious nomination.
More than a few of you touted BitLocker's accessibility and ease of
use, and many of you even praised its encryption for being strong and
difficult to crack. Many of you noted that you switched to BitLocker after the developers of TrueCrypt suggested it.
Others, however, brought up the assertion made from privacy advocates
that BitLocker is compromised and has backdoors in place for government
security agencies (from multiple countries) to decrypt your data.
While Microsoft has officially said this isn't true and maintains
there's no backdoor in BitLocker (while simultaneously maintaining the
code as closed source—but available to review by its partners, which
include those agencies), the assertion is enough to make more than a few
of you shy away. You can read more about the criticism and controversy at the Wikipedia link above, or in the nomination thread here . GNU Privacy Guard (Windows/OS X/Linux)

GNU Privacy Guard (GnuPG) is actually an open-source implementation of Pretty Good Privacy (PGP). While you can install the command line version on some operating systems, most people choose from the dozens of frontends and graphical interfaces for it, including the official releases that can encrypt everything from email to ordinary files to entire volumes.
All GnuPG tools support multiple encryption types and ciphers, and
generally are capable of encrypting individual files one at a time, disk
images and volumes, or external drives and connected media. A few of you nominated specific GnuPG front-ends in various threads, like the Windows Gpg4Win , which uses Kleopatra as a certificate manager.
Those of you who nominated GnuPG praised it for being open-source and
accessible through dozens of different clients and tools, all of which
can offer file encryption as well as other forms of encryption, like robust email encryption for example. The key, however, is finding a front-end or a client that does what you need it to do and works well with your workflow. The screenshot above was taken using GPGTools
, an all-in-one GnuPG solution that offers keychain management as well
as file, email, and disk encryption for OS X. You can read more in its nomination thread here . 7-Zip (Windows/OS X/Linux)
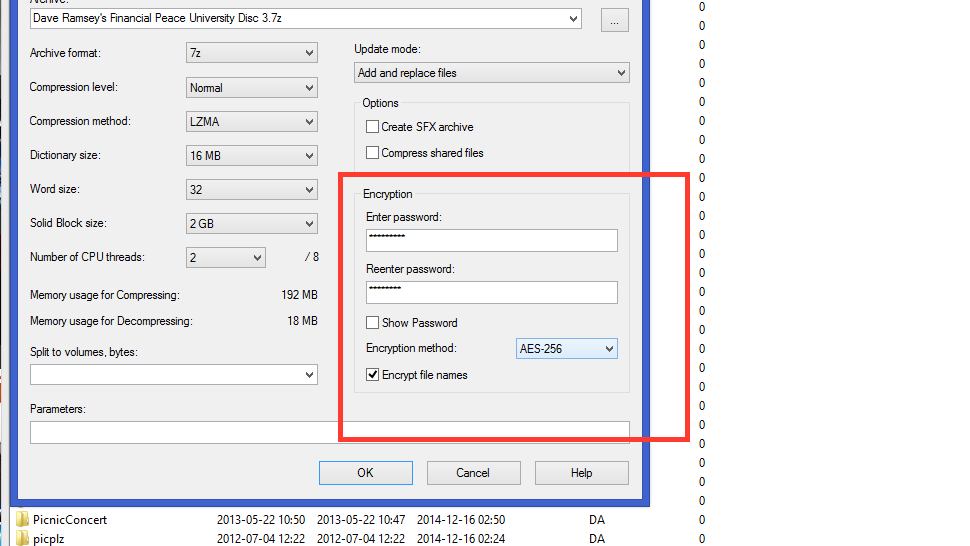
7-Zip is actually a lightweight file archiver—and our favorite archive utility for Windows .
Even though it's amazing at compressing and organizing files for easy
storage or sending over the internet, it's also a strong file encryption
tool, and is capable of turning individual files or entire volumes into
encrypted volumes that only your have the keys to.
It's completely free, even for commercial use, supports 256-bit AES
encryption, and while the official download is Windows only, there are
unofficial builds for Linux and OS X systems as well. Most of 7-Zip's code is GNU LGPL licensed and open to review.
Compressed and encrypted .7z (or .zip, if you prefer) archives are
easily portable and secure, and can be encrypted with passwords and
turned into executables that will self-decrypt when they get to their
intended recipient. 7-Zip also integrates with the shell of the operating system you're using, making it usually a click away from use. It's also a powerful command line utility.
Those of you who nominated it noted that it may not have the most
robust user interface, but it gets the job done, and many of you have it
installed anyway specifically for its robust file compression and
decompression capabilities.
You noted it's fast, flexible, free, and easy to use, and while it may
not be the fastest file encryption tool (and it's not capable of whole
volume or disk encryption), it gets the job done—especially for
encrypting files you need to send to someone else and actually have them
be able to access without jumping through too many hoops.
Some of you noted that 7-Zip's encrypted volumes are flexible—perhaps
too flexible, since new files added to an encrypted archive aren't
encrypted (you'd have to extract them all and make a new archive for
that), but it's otherwise a minor ding. You can read more in its nomination thread here .
Now that you've seen the top five, it's time to put them to an all-out vote to determine the community favorite.
What's The Best File Encryption Tool?
Honorable Mentions
We have two honorable mentions this week. First and foremost is Disk Utility (OS X), which is bundled with OS X as a disk repair and management tool. Disk Utility can also encrypt drives and volumes, and since OS X can create a compressed volume just by right-clicking a file, series of files, or a folder and selecting "Compress," Disk Utility makes encrypting anything you want extremely easy. Plus, it's built in to OS X, so you don't need to install anything else. You can read more about it in its nomination thread here . Second, we should tip our hats to the venerable old TrueCrypt , our old champion, which actually earned a number of nominations in the call for contenders thread. We covered the meltdown of TrueCrypt when it happened, with the developers abruptly abandoning the project claiming that it's no longer secure, in the middle of their independent security audit. The developers suggested switching to BitLocker, and pushed out a new version that's widely considered compromised. However, the older version, 7.1a, is still widely regarded as safe , even though development on it has been abandoned, and the tool has been left without security updates since then. Even so, security analysts split on whether you should trust TrueCrypt or move on to another encryption utility. Many people stand by it even though it's a dead project, others have built their own projects on top of it (see VeraCrypt, mentioned earlier), and others keep using the last safe version. We can't recommend TrueCrypt anymore ourselves, but you can read more in its nomination thread here , and over at Steve Gibson's page dedicated to TrueCrypt here .
Have something to say about one of the contenders? Want to make the case for your personal favorite, even if it wasn't included in the list? Remember, the top five are based on your most popular nominations from the call for contenders thread from earlier in the week .
Don't just complain about the top five, let us know what your preferred
alternative is—and make your case for it—in the discussions below.
The Hive Five is based on reader nominations. As
with most Hive Five posts, if your favorite was left out, it didn't get
the nominations required in the call for contenders post to make the
top five. We understand it's a bit of a popularity contest. Have a suggestion for the Hive Five? Send us an email at tips+hivefive@lifehacker.com ! Title photo by andrey_l (Shutterstock).
Anonymous ‘Hacktivists’ Just Smacked The Taste Out Of ISIS’s Mouth
The Anonymous “hacktivist” group, took over dozens of accounts on Twitter and Facebook, which have been overtly used as recruiting tools for the group to gain more numbers.
Anonymous- #OpISIS Continues...
The video explains that Anons engaged in #OpISIS are “Muslims, Christians, Jews” alike. They are “hackers, crackers, Hacktivist, phishers, agents, spies, or just the guy next door… students, administrators, workers, clerks, unemployed, rich, poor.”
The video continues to explain to their enemies that they are “young, or old, gay or straight… from all races, countries, religions, and ethnicity. United as one, divided by zero.”
The video seeks to inform the public that “the terrorists that are calling themselves [the] Islamic State (ISIS) are not Muslims.”
Follow the prefacing “clarification,” the video explains the following, direct to ISIS specifically:
We will hunt you, take down your sites, accounts, emails, and expose you…
From now on, no safe place for you online…
You will be treated like a virus, and we are the cure…
We own the internet…
We are Anonymous; we are Legion; we do not forgive, we do not forget, Expect us.
Some of ISIS Twitter accounts, that were taken offline by Anonymous, RedCult team as part of #OpISIS are as follows:
https://twitter.com/Daash
https://twitter.com/DaashISIS
https://twitter.com/DaashConnect
https://twitter.com/DaashConnect1
https://twitter.com/DaashConnect2
https://twitter.com/DaashConnect3
https://twitter.com/DaashConnect4
https://twitter.com/DaashConnect5
https://twitter.com/DaashConnect6
https://twitter.com/DaashConnect7
https://twitter.com/DaashConnect8
https://twitter.com/DaashISIS
https://twitter.com/ISISConnect
https://twitter.com/ISISConnect2
https://twitter.com/ISISConnect3
https://twitter.com/ISIS_Connect
https://twitter.com/D3ichy1
https://twitter.com/Nour_zalam
https://twitter.com/fadou7_ilma3bar
https://twitter.com/Faysal_da3iche
https://twitter.com/sam7anA7mar
https://twitter.com/Salman7asoun
https://twitter.com/far7at_naser_3
https://twitter.com/Asad3oumran
https://twitter.com/AbouHilal_bader
https://twitter.com/Abou7amadElrasy
https://twitter.com/Dafiq_ISIS
https://twitter.com/Salman_Anwar
https://twitter.com/Jazib_moutawakil
https://twitter.com/Albakistani_JN
https://twitter.com/umar_media_ttp
https://twitter.com/Din1080
https://twitter.com/abu_elbaraa91
https://twitter.com/Din1080
https://twitter.com/ZawahiriRafidhi
https://twitter.com/interditAuPaien
https://twitter.com/Qan9Yaman
https://twitter.com/Abouyamany
https://twitter.com/AlRani1
https://twitter.com/AMouwahidin
https://twitter.com/AbouMoustapha1
https://twitter.com/Abou_illabaisse
https://twitter.com/Ja3faralsadik
https://twitter.com/E7sanALsadiq
https://twitter.com/Ja3far_aboumahdi
https://twitter.com/imam_3antar
https://twitter.com/AbuBicha
https://twitter.com/OumShaheed1
https://twitter.com/aboomusab69
https://twitter.com/riahizaid12
https://twitter.com/Khaled_nousra
https://twitter.com/MouvementSalafi
https://twitter.com/akhypotteur
https://twitter.com/Dz_Bara_ah
https://twitter.com/UmmSherazzade
https://twitter.com/Salam_nour
https://twitter.com/Abou_OmarAlchamy
https://twitter.com/Abou_jabal
https://twitter.com/Baghdadid1
https://twitter.com/Ra2if_w
https://twitter.com/Amin_3abdala
https://twitter.com/Qouyas7
https://twitter.com/zalmour_3aziz
https://twitter.com/karkhan_el_nour
https://twitter.com/Barlous_3antar
https://twitter.com/karim_soura
https://twitter.com/SrhZtn
https://twitter.com/Monimelperso
https://twitter.com/Abounizar_sadim
https://twitter.com/AbouNasir_nousra
https://twitter.com/khalid_da3ichy
https://twitter.com/Mouhran_salam_alah
https://twitter.com/Mounir3abed_nousra
https://twitter.com/MinhajNoubouwa
https://twitter.com/abou_suisse
https://twitter.com/dawlaReporter
https://twitter.com/FatimaYouYouu
https://twitter.com/Nour_Da3ich
https://twitter.com/aylan7x
https://twitter.com/Parigi6
https://twitter.com/moujahidardent
https://twitter.com/patience1900
https://twitter.com/alfuratwadijlah
https://twitter.com/CassKhattab
https://twitter.com/ibnhouss > Rachid Abou Houdeyfa
https://twitter.com/aboushaheed_
https://twitter.com/abubakr99amb
https://twitter.com/Salashh
https://twitter.com/jamilnousran
https://twitter.com/jamilnousran1
Anonymous says the following Facebook accounts are in close contact with ISIS in Syria and Iraq. They advise us to “keep a close eye” on them.
https://www.facebook.com/azizi.salinaAnonymous assures us that there are “more to come.” In fact, as we were writing this article, our sources within Red Cult contacted us with more accounts to update. Bookmark this page, as we suspect there will be more updates soon.
————————————–
https://www.facebook.com/mujahiddin.bolzan
————————————–
https://www.facebook.com/sinar.cahaya.73
————————————–
https://www.facebook.com/putraijamarul77
————————————–
https://www.facebook.com/profile.php?id=100007817504822 ====> This are Junaid Hussain AkA TriCk.
————————————–
https://www.facebook.com/najmi.mie.9
————————————–
https://www.facebook.com/mohdazril.matsoom
————————————–
https://www.facebook.com/mohdrahemyl.remy
————————————–
https://www.facebook.com/safwan.wan.5661
————————————–
https://www.facebook.com/LanMazPasForAll
————————————–
https://www.facebook.com/cikgu.ihsan
————————————–
https://www.facebook.com/buxy.bux ====> (Recruiter) This woman she to brainwash young people to go to Syria to fight alongside Terrorists of the Islamic State.
————————————–
Image by Counter Current News
======================================================

If you have information regarding #OpISIS you would like to submit anonymously contact us at ghostsec@riseup.net
#Anonymous #GhostSec
Operation ISIS Video Press Release. [French Subtitles]
https://www.youtube.com/embed/y76N3HGk0EY …
#Anonymous #GhostSec #OpISIS
=====================================
*Note This Sharing By Anonymous^^~
Anonymous hacktivists strike ISIS ^^ anonymous hero brothers have enormous power to kill. IS "rogue graffiti wonderful, truly implement strong team ah ^! -
匿名黑客行動主義者打擊ISIS^^匿名英雄兄弟有巨大的權力殺掉'' IS“流氓精彩的塗鴉,真正實行強而有力的隊伍啊! ^-
익명 hacktivists는 ISIS ^^ 익명의 영웅 형제는 죽일 수있는 엄청난 힘을 가지고 파업. "불량 낙서 멋진, 진정으로 구현 강한 팀입니다 아 ^! -
Hacktivistes Anonymes frappent ISIS ^^ frères héros anonymes ont un énorme pouvoir de tuer. IS "graffitis merveilleux, vraiment mettre en œuvre solide équipe de voyous ah ^! -
匿名ハクティビストはISIS^^匿名のヒーロー兄弟は殺すために巨大な力を持っているに当たる。 「不正な落書き素晴らしい、本当に実現する強力なチームですああ^! -
Anonymous Hacktivisten schlagen ISIS ^^ anonymen Helden Brüder haben enorme Macht zu töten. IS "Schurken Graffiti wunderbar, wirklich umsetzen starkes Team ah ^! -
Tiny Melody.Blog, small as dust, wind come, we gone~
~ MY DEAR FRIENDSHIP ANONYMOUS~Sincently Thankgiving..
http://melody-free-shaing.blogspot.com/2015/02/dear-anonymous-legion-chivalrous-by.html
=============================
---*Dear Anonymous Legion chivalrous by publishing information ---
Anonymous .@Newsweek. Twitter account recovered after hack by #ISIS
-[http://www.newsweek.com/newsweek-twitter-account-hacked-isis-affiliated-group-305897 ]-&- Anonymous @·''Has modern Linux lost its way?''[ http://changelog.complete.org/archives/9299-has-modern-linux-lost-its-way-some-thoughts-on-jessie ]-&-Anonymous @YourAnonNews ·''War gaming for security cred ''[ http://hackaday.com/2015/02/08/war-gaming
for-security-cred/ ]-&-Anonymous*DIGITΛSHΛDØW @DigitaShadow·
#Anonymous hacktivists strike at ISIS.^^The Anonymous hero brother have big power to killed IS 'rogue-.....!''-
---*親愛的匿名軍團俠義通過發布信息---Anonymous.@Newsweek.'黑客通過#ISIS後的Twitter帳戶恢復'- [http://www.newsweek.com/newsweek-twitter-account-hacked-isis-affiliated-group-305897] - &-Anonymous@''有現代的Linux迷失了方向?''[HTTP:/ /changelog.complete.org/archives/9299-has-modern-linux-lost-its-way-some-thoughts-on-jessie] - & -匿名@YourAnonNews·“戰爭遊戲的安全名氣'[HTTP: //hackaday.com/2015/02/08/war-gaming-for-security-cred/] - &-佚名*DIGITΛSHΛDØW@DigitaShadow·#匿名黑客行動主義者打擊ISIS^^....!-
---*정보를 게시하여 기사도 친애하는 익명 군단---익명.@뉴스 위크. 트위터 계정은 #ISIS에 의해 해킹 후 복구- [http://www.newsweek.com/newsweek-twitter-account-hacked-isis-affiliated-group-305897] - 및 - 익명 @YourAnonNews·'''현대 리눅스가 길을 잃은 적이 있습니까?'[HTTP : / /changelog.complete.org/archives/9299-has-modern-linux-lost-its-way-some-thoughts-on-jessie] - & -'익명 @YourAnonNews ·'보안의 cred에 대한 전쟁 게임 '[HTTP : //hackaday.com/2015/02/08/war-gaming-for-security-cred/] - 및 - 익명*DIGITΛSHΛDØW @ DigitaShadow ·. #Anonymous hacktivists는 ISIS을 공격 ^^익명의 영웅 형제가 사망에 큰 힘을 가지고는 '불량 !'IS '-.....!-
**All the world city/ country lauguage**-
http://melody-free-shaing.blogspot.com/2015/02/dear-anonymous-legion-chivalrous-by.html
---*Cher Anonyme Légion chevaleresque en publiant des informations ---
Anonyme. @ Newsweek.Compte Twitter récupéré après bidouille par #ISIS
- [http://www.newsweek.com/newsweek-twitter-account-hacked-isis-affiliated-group-305897] - & - AnonymeYourAnonNews ·''Est-ce que Linux moderne a perdu son chemin? ''[http: / /changelog.complete.org/archives/9299-has-modern-linux-lost-its-way-some-thoughts-on-jessie] - & - AnonymeYourAnonNews · '' guerre jeu pour cred de sécurité '' [http: //hackaday.com/2015/02/08/war-gaming
pour la sécurité-cred /] - & - Anonyme*DIGITΛSHΛDØW @ DigitaShadow ·
. Hacktivistes #Anonymous frapper ISIS ^^ Le frère de héros anonymes ont grand pouvoir de tués est «voyous -.....!''-
---*情報を公開することによって騎士道親愛匿名軍団---匿名。@ニューズウィーク。 Twitterアカウントは#ISISによってハック後に回収-
[http://www.newsweek.com/newsweek-twitter-account-hacked-isis-affiliated-group-305897] - & - 匿名@YourAnonNews· '' '現代のLinuxは、その方法を失っている?' [HTTP:/ /changelog.complete.org/archives/9299-has-modern-linux-lost-its-way-some-thoughts-on-jessie] - & - '匿名@YourAnonNews·' 'セキュリティクレドのための戦争ゲーム' [HTTP: //hackaday.com/2015/02/08/war-gaming.のためのセキュリティ-CRED/] - & - 匿名*DIGITΛSHΛDØW@ DigitaShadow·#AnonymousハクティビストはISISで打つ^^匿名ヒーローの弟が殺さに大きな力を持っているが「ならず者-.....! 'は' -
---*Sehr geehrter Anonymous Legion ritterlichen durch die Veröffentlichung von Informationen---Anonymous.@ Newsweek.Twitter-Account nach dem Hack von #ISIS erholt- [http://www.newsweek.com/newsweek-twitter-account-hacked-isis-affiliated-group-305897] - & - AnonymYourAnonNews ·''Hat modernen Linux verlor seinen Weg? ""[http: / /changelog.complete.org/archives/9299-has-modern-linux-lost-its-way-some-thoughts-on-jessie] - & -
AnonymYourAnonNews ·'' War Gaming Sicherheitsgründen cred ''[http:
//hackaday.com/2015/02/08/war-gaming für-security-cred /] - & - Anonym*DIGITΛSHΛDØW @ DigitaShadow ·.#anonymous Hacktivisten Streik bei ISIS ^^ Das Anonymous Held Bruder haben große Macht, getötet IS "Schurken -.....!''-
---*Karaj Anonima Legio kavalireca aperigante informon---Anonimaj. @ Newsweek.Twitter konton restaŭrita post hack per #ISIS-[http://www.newsweek.com/newsweek-twitter-account-hacked-isis-affiliated-group-305897] - & -AnonymousYourAnonNews ·''havas moderna Linukso perdis sian vojon? ''[http: / /changelog.complete.org/archives/9299-has-modern-linux-lost-its-way-some-thoughts-on-jessie] - & - Anonymous@YourAnonNews · '' Milito ludoj por sekureco cred '' [http: //hackaday.com/2015/02/08/war-gaming
por-sekureco-cred /] - & - Anonymous*DIGITΛSHΛDØW @ DigitaShadow ·
#Anonymous Hacktivists frapi je ISIS. ^^La Anonima heroo frato havas grandan povon mortigis ESTAS 'fripono -.....!''-
**All the world city/ country lauguage**
===Melody.ABlog===FOLLOW FOLLOW===>/
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%&
********













沒有留言:
張貼留言
window.___gcfg = {
lang: 'zh-CN',
parsetags: 'onload'
};