---分享著名分析病毒及漏洞,,信息洩露專家"沃伊切赫Dworakowski"先生的分析專案文章-"虛擬銀行劫案 ,,在現實生活中 ![本週波蘭銀行通過其網上銀行的界面突破。據報導,攻擊者竊取了250.000美元,現在使用的80.000客戶的個人信息來要挾銀行。據稱攻擊者利用一個遠程執行代碼漏洞,...]-圖文詳解-(非常仔細及專業的著名專家)-
---Teilen bekannten Viren und Schwachstellen analyse-Experte Offenlegung von Informationen,, Famous "Wojciech Dworakowski" Mr. Analysis Project Artikel - "virtuelle Banküberfall,, im wirklichen Leben!" [Diese Woche hat die polnischen Banken durch ihre Online-Banking! Schnittstelle Durchbruch angeblich Angreifer habe $ 250.000, 80.000 Kunden nutzen heute persönlichen Informationen, um die Bank angeblich erpressen Angreifer mit einem Remotecodeausführung ermöglichen...] - Detaillierte Grafiken - (sehr sorgfältig und professionell der bekannte Experte)-
---株式既知のウイルスや脆弱性分析の専門家の情報開示,,有名な「ヴォイチェフDworakowski "ミスター分析プロジェクトの記事 - 「仮想銀行強盗,,実際の生活の中で!」【今週ポーランドの銀行のオンラインバンキングを介して!詳細なグラフィックス -- (非常に慎重とプロのよく知られた専門家)インタフェースブレークスルーは伝え攻撃者は...] 80.000顧客は、リモートでコードが実行される脆弱性を使用して銀行疑惑攻撃者を脅迫するために個人情報を使用し、250.000ドルを盗みました -
---Partager connu informations virus et la vulnérabilité des analyses d'experts divulgation,, Famous "Wojciech Dworakowski" de l'article de M. Analyse de projets - "vol de banque virtuelle ,, dans la vraie vie!" [Cette semaine, le bancaire polonais à travers sa banque en ligne! Interface percée aurait volé attaquants $ 250,000, 80.000 clients utilisent maintenant des renseignements personnels pour faire chanter la banque présumé agresseur en utilisant une vulnérabilité d'exécution de code à distance...] - Des graphismes détaillés - (très soigneusement et l'expert bien connu professionnelle)-
--- 공유 알려진 바이러스 및 취약성 분석 전문 정보 공개,, 유명한 "요이치 Dworakowski"고 분석 프로젝트의 기사 - "가상 은행 강도,, 현실에서!"[이번 주 폴란드 은행의 온라인 뱅킹을 통해! (매우 신중하고 전문 잘 알려진 전문가) - 자세한 그래픽 - 인터페이스 돌파구는 소문에 공격자는...] $ 250.000, 80.000 고객이 지금은 원격 코드 실행 취약점을 이용하여 은행 주장 공격자를 협박하기 위해 개인 정보를 사용 훔친 -
**All The World Lauguage**-

Wojciech Dworakowski
IT Security Expert, Owner at SecuRing, OWASP Poland Chapter Leader.
2015 年 6 月 12 日
Online banking owned by single attacker

This week Polish internet is buzzing about break-in to online banking
website. This case seems to be extremely interesting and quite
different from most of bank hacking news as the attack vector was not
client-side malware but rather exploitnig vulnerabilities in internet
banking application. All news coverage is in Polish so I decided to
write a short summary for my English speaking friends.
Disclaimer: This article is based on public sources, mostly - local IT security blogs. Attacker has contacted security journalists and provided them details of his actions (probably to raise the stakes in blackmailing the bank).
According to the major Polish IT Security blog - Z3S (http://zaufanatrzeciastrona.pl/post/powazne-wlamanie-do-polskiego-banku-skradzione-dane-i-hasla-klientow/]] - in Polish) - the attacker claims that he took control over the main bank's server, probably through RCE vulnerability in obsolete software. He was able to modify internet banking application and insert server-side webinjects to steal users' credentials. Moreover, thanks to an authorization mechanism vulnerability in adding trusted recipients he stole about 1 million PLN (about 250 000 USD). Bank has confirmed the breach but without any details.
Probably after the breach was detected and the bank cut attacker's access, he started to monetize previously stolen data - credit cards with CVV numbers and other financial data - by blackmailing the bank with a ransom request (200,000 PLN / about 50 000 USD). To prove he possess sensitive data about 80 thousand customers, he presented transaction history of one prominent businessman related to the bank management and few other database fragments like credit card numbers. Moreover - on Tuesday, for a short time bank's corporate web page was redirected to another company page (probably attacker was able to change DNS records). The case is pending, as the ransom deadline ends today. Bank switched off his corporate web page "due to maintenance" (internet banking page is working).
This is typical case of business logic security defect. What is interesting is that this also affects functionality so probably it should be detected by QA test cases.
Further details are not available but, again, it is probably a logic flaw (e.g. parameter sent form browser side which controls which authorization mechanism is used) or some leftover from development phase.
This time it was not the malware, but would an antimalware solution save this bank from attack? My colleagues - Jakub Kałużny and Mateusz Olejarka presented a research on anti-malware solutions at BlackHat Asia 2015 and CONFidence: http://www.slideshare.net/wojdwo/bypassing-malware-detection-mechanisms-in-online-banking-confidence
Disclaimer: This article is based on public sources, mostly - local IT security blogs. Attacker has contacted security journalists and provided them details of his actions (probably to raise the stakes in blackmailing the bank).
Case description
Medium-size Polish bank (about 500 million USD in assets) was hit earlier this year by a single attacker who managed to takeover the internet banking frontend server, steal money and maintain control over it through next few weeks. Now the attacker blackmails the bank and requests a ransom.According to the major Polish IT Security blog - Z3S (http://zaufanatrzeciastrona.pl/post/powazne-wlamanie-do-polskiego-banku-skradzione-dane-i-hasla-klientow/]] - in Polish) - the attacker claims that he took control over the main bank's server, probably through RCE vulnerability in obsolete software. He was able to modify internet banking application and insert server-side webinjects to steal users' credentials. Moreover, thanks to an authorization mechanism vulnerability in adding trusted recipients he stole about 1 million PLN (about 250 000 USD). Bank has confirmed the breach but without any details.
Probably after the breach was detected and the bank cut attacker's access, he started to monetize previously stolen data - credit cards with CVV numbers and other financial data - by blackmailing the bank with a ransom request (200,000 PLN / about 50 000 USD). To prove he possess sensitive data about 80 thousand customers, he presented transaction history of one prominent businessman related to the bank management and few other database fragments like credit card numbers. Moreover - on Tuesday, for a short time bank's corporate web page was redirected to another company page (probably attacker was able to change DNS records). The case is pending, as the ransom deadline ends today. Bank switched off his corporate web page "due to maintenance" (internet banking page is working).
Update (2015-06-16)
The story is still unfolding. Updates from last few days:- Bank of course didn't pay the ransom so attacker released first 500 records of corporate users' data (personal data, account balances, account history) and (alleged) image of bank's server. Attacker publishes information on paid Tor forum.
- Attacker changed his demands. Still he want the bank to pay 200,000 PLN but... to charity. If no, then he threatens that each weekend he will release next batches of bank customers' data.
- Bank confirmed the breach but claimed that this is "old story" and they have "thwarted attack at very beginning" and "all clients' money are safe". Attack was also confirmed by The Polish Bank Association.
Vulnerabilities exploited by attacker
Out of date software components
According to attacker, he was able to takeover internet banking server in January 2015 by exploiting "undisclosed bug which was a result of lack of regular software updates". It is not clear if it was server component (which in my opinion is unlikely) or rather application component (framework, library, etc.) - which is more likely as this is often "no man's land" and there are some well known RCE bugs in popular,, frameworks,,.Business logic flaw in "trusted recipients" functionality
Normally, in case of this internet banking, it is necessary to confirm transfers with a SMS code (OTP send by SMS), however it is also possible to add a trusted recipient so that later it's not needed to confirm payments to this account. According to the attacker, he was able to bypass this additional transaction authorization, by adding mule's account as a "trusted recipient" to any account and in result this recipient was treated like "trusted" for all users.This is typical case of business logic security defect. What is interesting is that this also affects functionality so probably it should be detected by QA test cases.
Transaction authorization bypass
Attacker has determined that modifying one of parameters send by internet banking application allowed him to bypass requirement to authorize the transaction using SMS code. For the attack he chose rarely used accounts with big balance but the bank detected frauds and blocked the accounts.Further details are not available but, again, it is probably a logic flaw (e.g. parameter sent form browser side which controls which authorization mechanism is used) or some leftover from development phase.
Wrong implementation of masked password
This internet banking application uses "masked password" for users' authentication. A proper implementation of this mechanism should ask for the same mask after failed login attempt, while in this case, the application was asking for other character set on each authentication page reload. So that the attacker was able to sniff only one user authentication (using injected javascript) and then try to reload authentication form as long as application asks for sniffed character set.Comment
It's worth noting that this is not the information that "someone hacked the bank" distressing but rather how easily it was possible. From other similar sensations about the break-in or leak which feeds the media, this case differs in several facts:- The case doesn't look like a criminal organized group as in the case of major,, financial,, malware,, campaigns but rather "one man show". If it was a criminal group probably the scale could be much higher.
- The attacker didn't use malware or web-inject on the client-side but changed the application code after taking control of the server.
- The attacker did rather not use any "advanced" weapon like 0-day. From the description provided, it could have been an RCE on an unpatched application component (framework or library, e.g. old version of Struts'' or other framework). This is unfortunately often "no man's land". .
- A further attack was possible by the gross errors in the code of their own application (logic error in the implementation of a trusted recipient, the ability to bypass authorization of transactions by adding the parameter).
- Probably the bank wasn't able to quickly detect changes introduced by the attacker in the application.
Additional materials
My presentation from AppSec EU 2015 about transaction authorization vulnerabilities in online banking: http://www.slideshare.net/wojdwo/ebanking-transaction-authorization-appsec-eu-2015-amsterdam.This time it was not the malware, but would an antimalware solution save this bank from attack? My colleagues - Jakub Kałużny and Mateusz Olejarka presented a research on anti-malware solutions at BlackHat Asia 2015 and CONFidence: http://www.slideshare.net/wojdwo/bypassing-malware-detection-mechanisms-in-online-banking-confidence
===
Major Polish bank burglary, stolen customer data and passwords

We have seen evidence that the Polish bank fell victim to a serious robbery and the thief stole money, passwords and personal information of its clients. Unfortunately, for several reasons we can not tell you about which bank it comes.
Received by our service, evidence suggests that the mysterious burglar
had for several weeks full access to the main Web server of a Polish
bank.
As a result, they can make unauthorized transfers, collect personal
information of clients and collect information about their cards and
account history.
Burglar claims that robbed many accounts totaling around one million
zlotys, and the bank for several weeks did not notice burglary.
For two months, ie from the moment when we learned who fell victim to burglary victims we cooperated with the bank.
At the request of the bank met with its representatives, we shared our
experiences and knowledge of similar cases of attacks and the Polish
underground internet and we passed the information available on the
extent of information leakage.
After many days of waiting, we received the official position of the
bank, we sent also to bank information content of the article, which we
intended to publish. A few hours before the planned publication received the call to bring the infringement of personal rights of legal counsel representing the bank. After a few days we received an anonymous threat also suggests the possibility of issuing orders for the author of the article for publication.
For reasons that we discuss in more detail in later in the article, in
this publication do not we present information about what the bank
refers to burglary.
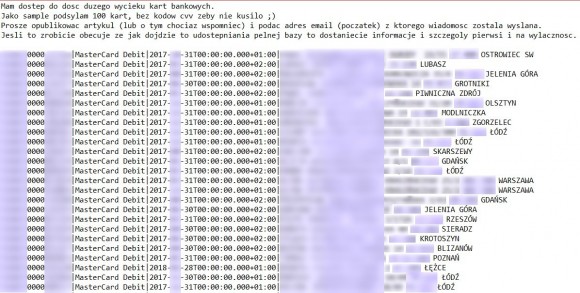
Burglar, trying to give credence to his story, he showed us the full details of hundreds of bank payment cards, personal data a thousand customers, ten thousand mobile phone numbers of bank customers, logins and passwords of more than 150 bank customers with balances of their accounts (mostly more than 100 thousand each) , tens of thousands of items from customer account statements, confirmations of transfers of hundreds of thousands of gold allegedly stolen by him and a copy of the bank Web server along with part of the electronic banking system. The full case history can be found below.
According to the bank's attempts to position the attacks took place, they are detected, and customer funds were and are safe. At the same time the bank refused to answer more detailed questions, hiding behind rules and security considerations.
One hundred cards to a good start
For us the story began April 10, 2015, when it received the first
message from the burglar with an email address razor4@t.pl, and with it
data 100 credit card numbers and their owners. Nature of the data showed that come from the base of a particular bank.
We also noticed that several items in the list.
First of all card numbers were identical IBAN number, indicating the
origin of the Polish bank (all we can say about it is that it is a
commercial bank that is not among the 10 largest banks in terms of
assets). Secondly, there appeared to be stolen from the trade network or ATM.
Customers came from all over Polish, some people dysponowały the list
two cards with different numbers, you can also find cards belonging to
people with the same surname living at the same address. Everything pointed to the fact that the data came from bank systems.
Using private channels contacted the bank, which confirmed informally that the subject is familiar to him. Therefore we responded sender and waited for further developments.
Durable exchange of messages with razorem4 and with the bank, but from
either party long received no information to better understand the
situation. We knew only that razor4 wants to receive from the bank ransom for non-disclosure of data.
Cards on the table
In recent days we have received from razora4 new data stolen from a bank and a long description of his actions.
Razor4 claims to the bank servers got in late January through
undisclosed error resulting from a lack of regular software updates.
According handed down to us by the burglar's description of events
after the diagnosis of the environment and the preparation of the
relevant bank accounts razor4 start to steal from bank customers.
For this purpose, the bank interceded on appeal to the JS script
located on your server, through which he could modify the account
numbers which were passed on converting the bank's customers and
substitute prepared there by themselves account. Razor4 registered specifically for this purpose domain differs from a real bank address only one letter.
We also had the opportunity to get acquainted with the provisions of
him, JS script, whose task was to automate the attack on the bank's
customers. In our opinion, the script looks like the most plausible.
Razor4 says that within a week he stole several hundred thousand, in
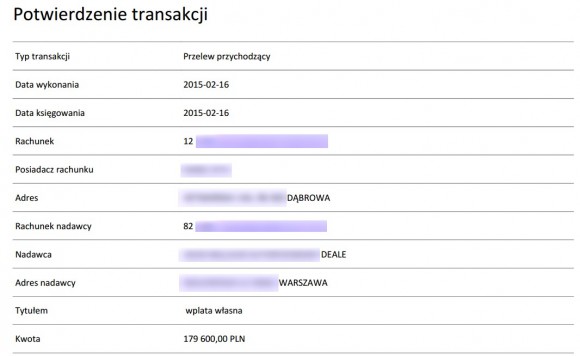
this Feb. 16, 2015 to make one transfer to almost 180 thousand from a
car dealer in Warsaw. Bank of burglar threw Trojans problem on client computers.
In fact, a few days later, the bank reminded customers about the safety
of transactions (although similar information campaigns conducted this
year all banks).
Alleged errors in bank systems
According razora4 he then changed his method of operation, because he
discovered, he says, a serious bug in the system of authorization of
transfers.
According to him, if the client they trusted Iksińskiego configured
recipient is a client Nowakowski could send a transfer to Iksińskiego
without giving the SMS code.
In this way, after adding customers trust on account controlled by
them, razor4 able to perform transfers to user-defined account customers
trusted with other people's accounts, not authorizing their SMS codes.
For this purpose, the bank launched the server script writer logins and
passwords, and when he landed on account of a hotel in a popular
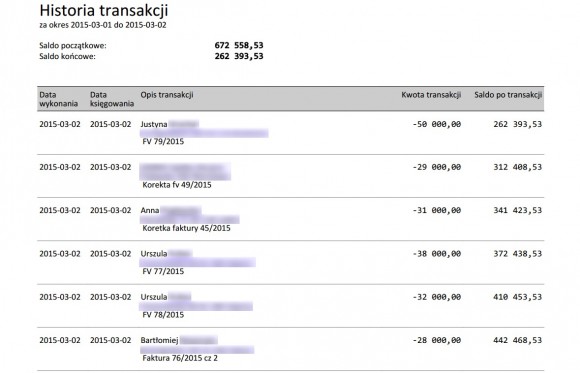
seaside resort with a balance of approx. 700 thousand zlotys, proceeded
to attack. According to his story a Monday within hours almost emptied the hotel bill.
When the owner of the account he realized that something was wrong, he
could block some transfers and the bank within two days fixed the error. As proof of his allegations razor4 he presented the statement of account of:
Razor4 suggests that despite the use of your password maskowalnego the
bank had no problem with the capture of other people's passwords,
because they collected them in a few logins.
Besides, he says that the bank enabled when logging in multiple places
password maskowalnego draw that need to be supplemented - allowing the
attacker to easily hit in possession characters.
Indeed logging mechanism draws the bank account each approach a
different set of characters, so just try long enough to receive the same
set that was previously captured.
In addition, among the evidence of burglary, with which we could read,
she was more than a hundred almost or totally complete user passwords
bank.
The third attack, which according to their stories moved razor4, was an attempt to derive about 3 million.
For this, first he used the accounts with the two bills, where one was
rarely used their clone with other banks (through the transfer of a
certain title you can open an account in another bank).
Then determined that the modification of one of the parameters passed
by the application banking allows you to bypass authentication
requirements of the transfer SMS code.
He chose to attack the seldom-used accounts with large balances and
night has generated a lot of transfers, but the bank apparently realized
that something was wrong and blocked all clients trading access to the
system and then remove the intruder from the system.
These attempted theft we have no evidence, however, these events are
partially supported by the bank's clients expressed by social media
pretensions associated with lack of access to transactional service for 2
days.
The fourth episode in the history described by razora4 the use of their usernames and passwords, bank customers.
He says that thanks to them could, among other things rob the account
of one of the companies involved in high-speed transfers between banks
and online payment service, generating transfers to its internal
accounts, set up specifically for this purpose. According to him he stole this road another 30 thousand. Injured company has confirmed to us the theft of funds from its account to the fault of the bank.
Evidence of access to the server
Burglar proof of having access to the Web server of the bank showed us the appropriate server directory listing. Analysis Listing lets likely to conclude that razor4 actually had control over the bank's Web server.
Listing the size of almost 5 megabytes primarily contained a list of
all files multiple instances of WebLogic application server, whose
paths, names, and individual files 100% overlap with files shared on the
pages of the bank's electronic banking services in all available
versions. What's more, the listing of files you can also find traces looking like a burglar business effect. They can of course be deliberately planted - but the listing looks very plausible.
Among the many files can eg. Find this gem:
-rw-r ----- [xxx] / [xxx] 3905 2013-07-08 20:49 [xxx] /xxx/xxx/xxx/xxx.png -rw-r ----- [xxx] / [xxx] 2359902208 2015-03-04 13:35 [xxx] /xxx/xxx/xxx/k.tar -rw-r ----- [xxx] / [xxx] 676 2013-07-08 20:49 [xxx] /xxx/xxx/xxx/xxx.jpg
The server "xxxx" is an instance of mobile banking interface.
There, in a directory full of graphics from 2013, could be found k.tar
file size more than 2 gigabytes, created March 4th, 2015 at 13:35.
Listing Sam probably comes from the same day, hour 16. The file k.tar
looks like an archive covering the entire file system, issued for
download on the Web server of the bank. Of course, the file has already been removed, but the remaining tracks are still valid.
In addition, the burglar also showed us the server configuration files and a copy of the e-banking application.
This confirms that the burglar had the ability to read, create and
modify files on a Web server that supports the bank's customers.
In addition razor4 claims that he was able to steal data also part of the bank's customers.
To confirm this, he showed us over 25 thousand records with different
accounts, transaction history, data thousands of clients such as your
name, address, telephone number and email address as well as information
about 600 different cards, 10,000 telephone numbers belonging to
customers of the bank reportedly and well over a hundred logins and
passwords to bank accounts.
All of the above events are likely from a technical point of view. Presented by the burglar story is consistent and did not find in it any conflict or substantial gaps.
Part statements burglar also confirmed by evidence from independent
sources (injured information company, registered the domain false bank
or customer complaints to the unavailability of electronic banking
service).
Reaction bank
After a long wait we received the position of the bank, whose extensive passages on the merits we publish below.
In our opinion, in a statement there is not a single sentence denying
the above-described events - there is also a single sentence that would
be directly confirmed.
In the first quarter of this year., [Bank name here] identified the hackers'.
With security systems and activities of the security services of the
Bank, the attacks are detected, and most importantly all cash bank's
customers were and are completely safe.
In connection with the illegal actions of criminals, the Bank informed
and intensively cooperate with the competent law enforcement
authorities, including with the relevant units of the Police and the
Prosecutor's Office. [...]
In connection with uploaded questions, addressed to [bank name here],
we would like to clarify that all received correspondence from someone
who intends to attack the good image of the Bank in a manner
nieuprawiony and inconsistent with applicable law. All such activities are and will be by the Bank reported to law enforcement.
In terms of the details contained in the correspondence sent because of
the legal regulations and safe operation of the Bank, [bank name here]
is not authorized to release the information or the provision of public
comments relating to the operation of information security used by the
Bank or its customers' data.
We emphasize that measures the Bank's clients are safe, properly secured banking systems.
Especially the last sentence suggests that if there was to steal
customer funds of the bank, the losses were covered by the bank.
Summons and threats
A week ago, for 5 hours before the scheduled publication of the article
(earlier at the request of the bank repeatedly reversible) we received a
call to bring the infringement of personal rights including the following paragraph:
[...] I call for the withdrawal of unlawful dissemination of
information on the effects of hacking attempts on the Bank's computer
system and used in connection with the bank security measures [...]. This information is based on unreliable sources and do not take into account the position of the Bank in the described case.
Prevalence of said information will be an action openly and manifestly
unlawful, threatening the personal (reputation) Bank and leading to the
formation of the Bank is difficult to powetowania damage.
In turn, on Friday around 11am from the IP address 37.147.97.33 through our contact form reached this message:
Part sloneczko, I start from the fact that already have a bone to pick
with us, so think twice if you want to publish an article about breaking
into [bank name here], 20k is not a lot, and the head flies, you want
to get in the end doigrac? Yours sincerely
The fact that we plan to publish an article, knew only narrow circle of trusted collaborators editorial, burglar and a bank. We do not know who was the sender of the message.
On the content of the call can be long and threats discuss regarded as
toothless, but each has its own acceptable level of risk, and in this
case we have been exceeded.
At the same time, we believe that bank customers should be information
about this unusual incident - if only to change their passwords (and not
just in the bank) and see through lifts.
In addition burglar threatens to sell or stolen information to be made
public - hence our decision to publish the article even in a truncated
form.
I am a customer of the bank, what to do
Unfortunately we can not restrict more target group of this manual -
but we believe that all of us would benefit, regardless of whether it is
their bank fell victim to burglary.
So if once logowaliście to the bank interface (ordinary or mobile) this
year and it was not a bank from among the major ones are first, change
your password immediately to their bank accounts.
If the same password as to the bank, you used also to other resources
(mail, another bank, etc.), There also it change your - and immediately
other than that of the bank.
Once you dump the password, check carefully the history of all their transactions from all accounts in 2015. If you find them positions that you can not explain, you ask for an explanation of the bank. Most suspects are two categories:
- transfers to the unknown you bills, significant amounts
- transfers with unusual titles (eg., "open an account", "confirmed opening an account") in the amount of 1 cent, 1.01 PLN or the like.
If such a find, it's possible that it's not your computer infection was the cause.
Watch the history of card transactions.
When you find suspicious entries do think, why not ask for a
reservation of old and issuance of new cards - all the data so far can
be in the hands of a burglar.
When you already have done all of the above operations, it continues, we recommend extreme caution.
What truth is that the bank had removed the intruder in your network,
but if leaked your personal information and contact details, it may
still be in the hands of criminals and be subject to resale. They may try to use them to eg. Take your data on loans or attempt to extort from you other information by e-mail or by phone. Be vigilant, keep checking your statements regularly, it does not hurt too BIK verification report. If you come across something disturbing, you can also contact us - we will help as much as possible.
===
Virtual Bank Robbery – In Real Life
Introduction
This week a Polish bank was breached through its online banking interface. According to the reports the attacker stole 250.000 USD and now uses the personal information of 80.000 customers to blackmail the bank. Allegedly the attacker exploited a remote code execution vulnerability in the online banking application to achieve all this.We at Silent Signal performed penetration tests on numerous online banking applications, and can say that while these systems are far from flawless, RCE vulnerabilities are fairly rare. Accordingly, the majority of the in-the-wild incidents can be traced back to the client side, to compromised browsers or naive users.
But from time to time we find problems that could easily lead to incidents similar to the aforementioned Polish banks. In this case-study we’re describing a remote code execution vulnerability we discovered in an online banking application. The vulnerability is now fixed, the affected institution was not based in Poland (or our home country, Hungary).
The bug
The online bank testing account had access to an interface where users could upload various files (pictures, HTML files, Office documents, PDFs etc.). The upload interface checked the MIME type of the uploaded documents only (from the Content-Type header), but not the extension. The Content-Type header is user controlled, so uploading a public ASPX shell was an obvious way to go; but after the upload completed I got an error message that the uploaded file was not found and the message revealed the full path of the missing file on the servers filesystem. I was a bit confused because I could not reproduce this error with any other files I tried to upload. I thought it was possible that an antivirus was in place that removes the malicious document before the application could’ve handled it.I uploaded a simple text file with the EICAR'' antivirus test string with .docx extension(so I could make sure that the extension wasn’t the problem) that verified this theory. The antivirus deleted the file before the application could parse it that resulted in an error message revealing the full path:
This directory was reachable from the web and the prefix of the file name was based on the current “tick count” of the system. The biggest problem was that the application removed the uploaded files after a short period of time because this was only a temporary directory. I could also only leak the names of deleted files but not the ones that remained on the system for a longer time. So exploitation required a bit more effort.
The Exploit
Before going into the details of the exploit, let’s see what “primitives” I had to work with:- I can upload a web shell (antivirus evasion is way too easy…)
- I can leak the tick count by uploading an EICAR signature
- I can access my web shell if I’m fast enough and know the tick count of the server at the moment the shell was uploaded
I built a simple test application that models the primitives described and implemented a simple time synchronization algorithm that I used before to predict time on remote servers with seconds precission. The algorithm works basically by making guesses and adjusting them based on the differentials to the actual reported server times.
While this algorithm wasn’t effective on the 100ns scale, the results were really interesting! I could observe that:
- Parallel requests result in identical tick counts with high probability
- The lower bits of the tick counts tend to represent the same few values
My final solution is based on grequests that is an awesome asynchronous HTTP library for Python. This allows me to issue requests very fast without having to wait for the answers in between. I’m using two parallel threads. The first uploads a number of web shells as fast as it can, while the other issues a number of requests with the EICAR string and then tries to access the web shells at constant offsets from the retrieved tick counts. The following chart shows the average hit rates (%) as the server side delays between the creation and deletion of the uploads changes:
And although a few percent doesn’t seem high, don’t forget that I had to only be lucky once! As you can see there is a limit for exploitability (with this setup) between 300 ms and 400 ms but as we later found out the uploads were transferred to a remote host, so the lifetime of the temporary files was above this limit turning the application exploitable.
The model application and the test exploit is available on GitHub.
Conclusion
In this case-study we demonstrated how a low impact information leak and a (seemingly) low exploitability file upload bug could be chained together to an attack that can result in significant financial and reputation loss.For application developers we have the following advises:
- If you’re in doubt, use cryptographicaly secure random number generators.
- Never assume that your software will be deployed to an environment similar to your test machine. A conflicting component (like the antivirus in this case) can and will cause unexpected behavior.
- File uploads are always fragile parts of web applications, OWASP has some good guidelines about securely handling them.
===========
網上銀行由單一的國有攻擊
 沃伊切赫Dworakowski
沃伊切赫Dworakowski
IT安全專家,業主在保護,OWASP波蘭領導章. 2015年6月12日

本週波蘭互聯網正在熱烈討論磨合網上銀行網站。 這種情況下似乎是非常有趣和非常不同於大多數銀行新聞黑客作為攻擊向量不是客戶端的惡意軟件,而是exploitnig在網上銀行應用程序的漏洞。 所有的新聞報導在波蘭,所以我決定寫一個簡短的總結,我的英語說的朋友。
免責聲明:本文基於公共來源,大多是 - 本地IT安全博客。 攻擊者有聯繫的記者的安全,並提供他們自己的行為細節(大概提高在訛詐銀行的股份)。
情況說明
中型銀行波蘭語(約500億美元的資產),是由誰管理,接管網上銀行前端服務器,竊取金錢和維護,通過未來數週內進行控制一個攻擊者在今年稍早觸及。 現在,攻擊敲詐銀行,並要求贖金。根據波蘭主要IT安全博客 - Z3S ( http://zaufanatrzeciastrona.pl/post/powazne-wlamanie-do-polskiego-banku-skradzione-dane-i-hasla-klientow/ ]] - 波蘭) - 攻擊者聲稱,他控制了主要銀行的服務器,可能是通過在過時的軟件RCE漏洞。 他能夠修改網上銀行應用程序,並插入服務器端webinjects竊取用戶的憑據。 此外,由於授權機制的脆弱性在增加信任的收件人,他偷了大約100萬茲羅提(約合250 000美元)。 銀行已經證實了違約,但沒有任何細節。
檢測後可能違約和銀行切斷攻擊者的訪問,他開始賺錢以前被盜的數據 - 與CVV號碼和其他財務數據信用卡 - 敲詐的銀行,贖金的要求(200,000茲羅提/約50 000美元)。 為了證明他擁有約8萬客戶的敏感數據,他提出的一個著名商人與銀行管理和其他一些數據庫碎片如信用卡號碼的交易記錄。 而且 - 週二,很短的時間銀行的公司網頁被重定向到另一家公司網頁(可能攻擊者能夠改變DNS記錄)。 該案件正在審理,作為贖金的最後期限將於今日結束。 銀行關掉了公司的網頁“由於維護”(網上銀行頁面的工作)。
更新(2015年6月16日)
這個故事還沒有結束。 從最近幾天的更新:- 當然,銀行也沒有支付贖金這樣攻擊者發布前500條記錄企業用戶的數據 (個人數據,賬戶 餘額,帳戶歷史記錄)和銀行服務器的(所謂的)圖像。 攻擊者發布關於支付Tor的論壇信息。
- 攻擊者改變了他的要求。 他仍然希望銀行支付20萬茲羅提,但...給慈善機構。 如果沒有的話,他威脅說,每個週末,他將釋放銀行的客戶數據的下一個批次。
- 銀行確認違約,但聲稱這是“老故事”,並與“所有客戶的錢是安全的”,他們“在一開始進攻受挫”。 進攻也是由波蘭銀行協會證實。
利用漏洞攻擊者通過
過時的軟件組件
根據攻擊者,他能夠接管網上銀行服務器在2015年元月被利用“未公開的漏洞這是缺乏定期的軟件更新的結果”。 目前尚不清楚,如果它是服務器組件(這在我看來是不可能的),或者更確切地說,應用程序組件(框架,圖書館等) - 這是更容易,因為這往往是“無人區”,並有一些知名的RCE蟲子流行的,, 框架 。在“受信任的收件人”業務邏輯漏洞的功能
通常,在情況下,這網上銀行,有必要確認一個短信代碼傳輸(OTP發送由SMS),但它也有可能使得購買它確認支付給該帳戶不是需要添加一個可信收件人。 根據攻擊者,他能夠繞過這個額外的交易授權,加入騾子帳戶作為“可信接受者”的任何帳戶,並在實驗結果的收件人像對待“信任”為所有用戶。這是業務邏輯安全缺陷的典型案例。 有趣的是,這也影響了功能,所以可能應該由QA測試時被檢測到。
交易授權旁路
攻擊者已經確定,修改的發送由網上銀行應用程序的一個參數允許他繞過規定使用短信代碼以授權交易。 對於進攻,他選擇了很少使用的賬戶餘額大,但銀行欺詐檢測和阻止的賬戶。更多細節不詳,但同樣,它可能是一個邏輯的缺陷(如參數的形式發送瀏覽器端,控制其授權機制時),或從發展階段的一些剩餘。
錯誤的實施蒙面密碼
該網上銀行應用程序使用“ 蒙面密碼 “為用戶的認證。 一個適當的實施這一機制應該請求失敗的登錄嘗試後相同的掩模,而在這種情況下,應用程序被請求其它字符上的每個認證頁面重載設置。 從而使攻擊者能夠嗅出只有一個用戶的身份驗證(使用JavaScript的注入),然後嘗試,只要應用程序要求嗤之以鼻字符集重裝認證形式。評論
值得一提的是,這不是信息“,如果有人黑了銀行”令人痛心的,而是它如何輕鬆地是可能的。 大約從磨合或洩露該飼料媒體的其他類似的感覺,這種情況下,在不同的幾個事實:- 此案看起來並不像一個有組織的犯罪集團中的情況下, 主要,, 金融,, 惡意軟件,,運動,而是“獨角戲”。 如果這是一個犯罪集團可能是規模可能會高得多。
- 攻擊者並沒有在客戶端使用的惡意軟件或Web注入,但改變了應用程序代碼以服務器的控制權後。
- 攻擊者也寧可不使用任何“先進”武器像0天。 從提供的描述,它可能是在一個未打補丁的應用程序組件(框架或庫,如老版的RCE 的Struts''或其他框架)。 這是不幸的是經常“無人區” 。
- 另一種攻擊是可能的總誤差在自己的應用程序(邏輯錯誤在一個可信任的收件人,通過添加參數繞過交易的授權能力的實現)的代碼。
- 可能是銀行無法快速檢測由應用程序的攻擊者引入的更改。
附加材料
我從歐盟APPSEC介紹2015年關於網上銀行交易授權漏洞: http://www.slideshare.net/wojdwo/ebanking-transaction-authorization-appsec-eu-2015-amsterdam.這一次是不是惡意軟件,但將反惡意軟件解決方案挽救攻擊這家銀行? 我的同事們 - 的JakubKałużny和馬特烏什Olejarka介紹了反惡意軟件解決方案的研究,在亞洲的BlackHat 2015年 CONFidence: http://www.slideshare.net/wojdwo/bypassing-malware-detection-mechanisms-in-online-banking-confidence.
===
波蘭主要銀行入室盜竊,被盜客戶資料和密碼
亞當 在類別加入2015年6月8日20:33左右竊用標籤
我們已經看到的證據表明,波蘭銀行的犧牲品了嚴重的搶劫和小偷偷走了錢,密碼和客戶的個人信息。 不幸的是,有幾個原因,我們不能告訴你哪家銀行談到。
通過我們的服務收到的證據表明,神秘的小偷了為期數週的完全訪問波蘭銀行的主要的Web服務器。 這樣一來,他們可以使未經授權的轉移,收集客戶的個人信息,並收集有關他們的卡和帳戶歷史記錄信息。 即被搶多個賬戶總額約一萬茲羅提防盜索賠,並持續數週,銀行沒有注意到入室。
兩個月來,從目前看,即當我們得知誰的犧牲品入室盜竊的受害者,我們與銀行合作。 在銀行的要求會見其代表,我們分享我們的經驗和對攻擊和波蘭的地下網絡類似案件的知識,我們可以通過對信息洩漏的程度的信息。 之後等待多日,我們收到了銀行的官方立場,我們還向銀行文章,我們打算發布的信息內容。 該計劃公佈前幾個小時接到電話帶來的佔本行個人法律顧問的權利被侵害。 過了幾天,我們接到一個匿名威脅也表明對於文章發表的作者發布命令的可能性。 為此,我們更詳細地討論後面的文章中,本出版物中沒有我們提出什麼銀行指的是入室盜竊的信息的原因。
防 盜,試圖給信任他的故事,他向我們展示了數百個銀行支付卡,個人資料的千餘家客戶,銀行客戶,登錄10000的手機號碼和150多個銀行客戶密碼與自己的 賬戶餘額的全部細節(大多超過10萬個)從客戶的賬戶報表項目幾萬,幾十萬的黃金由他和銀行的Web服務器隨著電子銀行系統的一部分副本涉嫌被盜的轉移確 認。 完整的病歷可以在下面找到。
根據銀行的企圖定位攻擊發生後,他們發現,和客戶資金是和是安全的。 同時,該銀行拒絕回答更詳細的問題,背後隱藏的規則和安全注意事項。
百卡一個良好的開端
對於我們的故事開始2015年4月10日,當它收到的第一條消息從防盜用的電子郵件地址razor4@t.pl,並與它的數據100信用卡號和它們的主人。 數據的性質表明,來自一個特定組的基。
我們也注意到了在列表中的多個項。 首先卡號是相同的IBAN號碼,表示波蘭銀行的起源(所有我們能說的是,這是商業銀行,是不是最大的10家銀行中資產方面)。 其次,出現了從貿易網絡或ATM被盜。 客戶從各地趕來的波蘭,有些人dysponowały名單兩張牌用不同的號碼,你也可以找到屬於人與同姓住在同一地址卡。 一切都指出,該數據從銀行系統傳來的事實。
通過私人渠道與銀行聯繫,證實了非正式的主題是熟悉他。 因此,我們的反應發送,等待進一步的發展。 耐用的交流與razorem4和與銀行的消息,但任何一方長時間沒有收到任何信息,以便更好地了解情況。 我們只知道razor4想要從銀行贖價的非公開數據的接收。
在桌子上卡
最近幾天,我們已經從一家銀行,他的行動很長的描述被盜razora4新的數據接收。 Razor4聲稱通過從一個缺乏定期的軟件更新導致錯誤未披露了在一月下旬銀行服務器。
根據流傳下來給我們事件的防盜的描述後對環境的診斷和相關銀行賬戶的編制razor4開始從銀行客戶竊取。 為此,該行對說情上訴的JS腳本位於服務器上,通過他可以修改它是在準備轉換的有銀行的客戶,並以自己的賬戶通過賬戶號碼。 Razor4註冊專門為此域不同於真正的銀行地址,只有一個字母。
我們也有機會結識了他的規定,JS腳本,其任務是在自動銀行客戶的攻擊。 在我們看來,劇本貌似最合理的。
Razor4說,一個星期之內,他偷了幾十萬,在這個2015年2月16日進行從一個汽車經銷商在華沙一個傳送到近180萬。 防盜銀行扔在客戶端計算機木馬程序的問題。 事實上,幾天之後,銀行提醒客戶有關交易的安全性(儘管類似的宣傳活動,今年所有銀行進行的)。
在銀行系統錯誤指控
據razora4他又改變了操作方法,因為他發現了,他說,一個嚴重的錯誤在轉讓授權的系統。 據他介紹,如果客戶端他們信任Iksińskiego配置收件人是一個客戶端Nowakowski可以發送傳輸,而不給短信代碼Iksińskiego。 通過這種方式,加入後客戶信任帳戶由他們控制,razor4能夠執行轉移到用戶定義的帳戶的客戶提供其他人的帳戶信任,不批准他們的短信代碼。 為此,該行推出的服務器編劇登錄名和密碼,當他降落在帳戶酒店在著名的海濱度假勝地的約70萬茲羅提的平衡,繼續攻擊。 根據他的故事小時內幾乎星期一清空酒店賬單。 當賬戶的所有者,他意識到出事了,他可以阻止某些轉移和在兩天內修復該錯誤的銀行。 由於他的指控證據razor4他提出考慮的聲明:
Razor4表明,儘管使用了你的密碼maskowalnego銀行曾與其他人的密碼捕獲沒有問題的,因為他們收集他們在幾個登錄。 此外,他說,銀行在啟用多個地方的密碼登錄時maskowalnego繪製需要補充 - 允許攻擊者很容易砸在身上的字符。 事實上,日誌機制繪製每種方法不同的字符集的銀行賬戶,所以只能盡力足夠長的時間來接受先前捕獲的同一組。 此外,入室盜竊的證據,有了它我們可以閱讀之中,她是一百多,幾乎或完全完整的用戶密碼庫。
第三次攻擊,而根據他們的故事感動razor4,是企圖獲得約3億美元。 為此,首先他用的賬戶與兩個法案,其中一個很少使用自己的克隆與其他銀行(通過一定的所有權轉移,你可以打開另一個銀行賬戶)。 然後確定由應用程序通過銀行的一個參數的修改允許你繞過轉移短信代碼驗證要求。 他選擇進攻很少使用的賬戶餘額較大,夜間也產生了大量的傳輸,但銀行顯然意識到事情不妙,並阻止交易進入到系統的所有客戶端,然後從系統中刪除入侵者。 這些企圖盜竊我們沒有證據,但是,這些事件的一部分被用難以獲得事務服務2天的相關社交媒體自命不凡表示,銀行的客戶支持。
在歷史上的第四個情節由razora4使用他們的用戶名和密碼,銀行客戶的描述。 他說,感謝他們可能會,除其他外參與搶劫銀行和網上支付服務之間高速傳輸的企業,產生轉移到其內部的一個帳戶的帳戶,專門設置了這個目的。 據他介紹,他偷了這條路另外30萬。 受傷的公司已經向我們證實資金失竊從賬戶到銀行的過錯。
訪問服務器的證據
有機會獲得銀行的Web服務器的防盜證據向我們展示了相應的服務器目錄列表。 分析上市讓容易得出這樣的結論其實razor4超過了銀行的Web服務器控件。 清單幾乎5兆字節的大小主要包含WebLogic應用服務器,其路徑,名稱和個人文件100%重疊的所有文件的多個實例的列表,文件銀行的電子銀行服務中的所有可用版本的網頁上共享。 更重要的是,文件的清單,你還可以找到痕跡看上去就像一個防盜事業效果。 當然,它們可以故意栽贓 - 但看起來上市非常合理的。
在眾多文件中可以找到,例如這種寶石:
-rw-R ----- [XXX] / [XXX] 3905 2013年7月8日20:49 [XXX] /xxx/xxx/xxx/xxx.png -rw-R ----- [XXX] / [XXX] 2359902208 2015年3月4日13:35 [XXX] /xxx/xxx/xxx/k.tar -rw-R ----- [XXX] / [XXX] 676 2013年7月8日20:49 [XXX] /xxx/xxx/xxx/xxx.jpg
服務器“xxxx”是手機銀行接口的一個實例。 在那裡,在一個目錄充滿了圖形從2013年,可以發現k.tar文件的大小超過2千兆字節,創造了2015年3月4日13:35時。 清單山姆很可能來自同日,小時16 k.tar看起來像一個存檔覆蓋整個文件系統,發出下載該銀行的Web服務器上的文件。 當然,該文件已經被刪除,但剩餘道仍然有效。
此外,防盜也向我們展示了服務器配置文件和電子銀行應用程序的副本。 這證實了防盜不得不讀取,創建和修改文件,支持銀行的客戶在Web服務器上的能力。
此外razor4聲稱,他能夠竊取數據也是銀行的客戶一部分。 為了證實這一點,他向我們展示了25000條記錄與不同的帳戶,交易歷史記錄,數據數以千計的客戶,如您的姓名,地址,電話號碼和電子郵件地址的信息以及大約600張不同的卡片,屬於銀行的客戶據說萬電話號碼和一百多登錄名和密碼,以銀行賬戶。
上述所有事件都可能從技術角度來看。 由防盜故事介紹的是一致的,並沒有發現它有任何衝突或重大差距。 部分語句防盜也證實了獨立來源的證據(受傷的信息公司,註冊了域名假銀行或客戶投訴電子銀行服務的不可用)。
銀行的反應
經過了漫長的等待,我們收到的銀行,其廣泛的通道上的優劣,我們發布下方的位置。 我們認為,在一份聲明中沒有一個單句否認上述事件 - 還存在將直接確認單句。
在今年的第一季度,[在此銀行名稱]認定黑客“。 隨著銀行的安全服務安全系統和活動的攻擊被檢測到,而且最重要的所有現金銀行的客戶過去和現在都是完全安全的。 在與犯罪分子的非法行為方面,銀行通知,並與主管執法部門深入合作,包括與警方和檢察官辦公室的有關單位。 [...]
在上傳的問題方面,給[在此銀行名稱],我們想澄清的是,所有的人誰打算攻擊銀行的良好形象的方式nieuprawiony和適用法律不一致收到信件。 所有這些活動,將是世行報告給執法部門。
在包含在對應的細節方面發來的法律法規和本行[這裡的銀行名稱]操作安全,因為沒有被授權發布的信息或提供有關信息安全的用銀行或客戶的數據的操作公眾意見。
我們強調,措施的銀行的客戶是安全的,適當固定的銀行系統。
尤其是最後一句暗示,如果有竊取銀行客戶資金的損失也包括在內的銀行。
傳票和威脅
一周前,為計劃出版的文章(先前在銀行多次可逆的要求)5小時前,我們接到一個電話帶來的個人權利,包括以下段落侵權:
[...]我呼籲對黑客入侵銀行電腦系統上嘗試的影響的信息傳播非法的撤離,在與銀行的保安措施結合使用[...]。 這個信息是基於不可靠的來源並沒有考慮到銀行的在所描述的情況下的位置。 上述信息的患病率將是一個公開的行動顯然和非法的,威脅的個人(口碑)銀行,並導致銀行形成難以powetowania傷害。
反過來,上週五從周圍的IP地址37.147.97.33通過我們的聯繫方式達到了11點此消息:
部分sloneczko,我從那個已經有一個挑骨頭和我們在一起,所以三思而後行,如果你想發表文章約闖入[在此銀行的名稱]的事實開始,20K還不是很多,頭蒼蠅,你想獲得最終doigrac? 此致
我們計劃發表文章的事實,就知道值得信賴的合作者編輯器,防盜和銀行只是狹隘圈子。 我們不知道誰是消息的發送者。 關於該呼叫的內容可以是長和威脅商量視為無齒,但每個都有風險的其自己的可接受的水平,並且在這種情況下,我們已經超過。 與此同時,我們認為,銀行客戶應該是關於這個不尋常的事件信息 - 如果只更改他們的密碼(不只是在銀行),並識破電梯。 除了防盜威脅要出售或被盜的信息被公之於眾 - 因此我們決定,即使在截斷形式發表文章。
我是銀行的客戶,該怎麼辦
不幸的是,我們不能限制本手冊的更多的目標群體 - 但我們相信,我們所有的人將受益,無論是他們的銀行犧牲品入室盜竊。 所以,如果一旦logowaliście銀行接口(普通或移動電話)今年,它是不是從當中主要的銀行首先,立即修改密碼,以他們的銀行帳戶。 如果相同的密碼到銀行,你還用於其他資源(郵件,其他銀行等),也有它改變你的 - 立即比銀行等。
一旦你傾倒的密碼,仔細檢查所有的交易的歷史,從所有帳戶在2015年。 如果你找到他們的位置,你無法解釋,你問銀行的解釋。 犯罪嫌疑人大多分為兩類:
- 轉移到未知的你賬單,金額顯著
- 不尋常的標題轉移(例如,“開立一個帳戶”,“證實開戶”)中的1美分,1.01 PLN或類似的量。
如果這樣的發現,這是可能的,它不是你的電腦被感染的原因。
手錶卡交易的歷史。 當你發現可疑的條目確實認為,為什麼不問老發行新卡預約 - 所有的數據,到目前為止可以在一個竊賊的手中。
當你已經完成了所有上述操作,再這樣下去,我們建議格外小心。 什麼樣的真理是,該行已刪除網絡中的入侵者,但如果洩露您的個人信息和聯繫方式,但仍可能在罪犯的手中,受到轉售。 他們可能會嘗試使用它們如:把你的數據在貸款或試圖從你通過e-mail或打電話敲詐等信息。 提高警惕,保持定期檢查你的報表,它不會傷害過BIK驗資報告。 如果你遇到什麼干擾,也可以聯繫我們 -我們將幫助盡可能多的。
===
虛擬銀行劫案 - 在現實生活中
本週波蘭銀行通過其網上銀行的界面突破。 據報導 ,攻擊者竊取了250.000美元,現在使用的80.000客戶的個人信息來要挾銀行。 據稱攻擊者利用一個遠程執行代碼漏洞,在網上銀行應用程序來實現這一切。
我們在無聲信號進行眾多的網上銀行應用程序滲透測試,可以說,雖然這些系統是遠遠完美無瑕,RCE漏洞是相當罕見的。 因此,大部分中最野性的事件可以追溯到到客戶端,以破壞瀏覽器或天真的用戶。
但是,從我們不時發現的問題,很容易導致類似上述銀行波蘭事件。 在這種情況下,研究我們描述我們發現,在網上銀行應用程序的遠程代碼執行漏洞。 該漏洞已經得到解決,受影響的機構不是基於波蘭(或我們的母國,匈牙利)。
該bug
網上銀行帳戶的測試曾獲得,用戶可以上傳各種文件(圖片,HTML文件,Office文檔,PDF文件等)的接口。 在上傳界面檢查的MIME類型上載的文件只(從Content-Type頭),但不能擴展。 該Content-Type頭的用戶控制,所以上傳一個公共ASPX外殼是一個明顯的路要走; 但上傳完成後,我未找到上傳文件的錯誤消息和消息透露了關於服務器的文件系統丟失的文件的完整路徑。 我有點困惑,因為我不能用我試著上傳任何其他文件重現此錯誤。 我認為這是可能的防病毒已經到位,消除惡意文檔的應用程序可能已經處理之前。我上傳的一個簡單的文本文件EICAR''防病毒測試字符串,擴展名為.docx(這樣我就可以確保該擴展是沒有問題的)是驗證了這一理論。 防病毒刪除之前的應用程序可以分析它是導致錯誤消息透露出的完整路徑的文件:
此目錄是從網絡和文件名 的前綴可達是基於當前的“滴答計數”該系統。 最大的問題是應用程序中刪除上傳的文件後很短的時間週期,因為這只是一個臨時目錄。 我還可以只洩漏刪除的文件的名稱,但不是那些仍然在系統上的時間較長。 因此,開發需要更多的努力。
該漏洞
再進的漏洞細節,讓我們看看“原始人”我不得不一起工作:- 我可以上傳網絡外殼程序(防毒逃稅是太簡單了...)
- 我可以通過上傳EICAR簽名洩漏滴答計數
- 我此刻的外殼上載訪問我的網站的外殼,如果我足夠快,並且知道服務器的滴答計數
我建立了模型圖元描述並實現了我以前用來預測時間與秒precission遠程服務器的簡單時間同步算法一個簡單的測試應用程序。 該算法通過使估計值,且基於所述差異來實際報告服務器倍調節他們的作品基本上。
雖然這種算法並不在100ns的規模效益,結果真的很有趣! 我可以觀察到:
- 並行請求導致相同的滴答計數與概率高
- 蜱計數的低位傾向於代表相同幾個值
我的最終解決方案是基於grequests這是Python的一個真棒異步HTTP庫。 這使我發出請求非常快,而不必等待在間的答案。 我使用的是兩條平行線。 第一上傳許多幅殼一樣快,它可以,而其他問題的一些使用EICAR串請求,然後嘗試從所檢索的蜱計數訪問web彈恆定偏移。 下面的圖表顯示的平均命中率(%)作為上傳變化的創建和刪除的服務器端延遲:
並且,雖然百分之幾似乎並不高,不要忘記,我只能是幸運的一次! 正如你可以看到有300毫秒,400毫秒之間的可利用性的限制(在此設置),但我們後來發現的上傳轉移到遠程主機,所以臨時文件的壽命高於此限制轉向應用利用。
該模型的應用和開發測試上可供GitHub上'' 。
結論
在這種情況下,研究中,我們演示了如何低影響的信息洩露和(貌似)低可利用性文件上傳漏洞可以一起鏈接到攻擊,可能導致金融顯著和聲譽損失。對於應用程序開發人員,我們有以下建議:
- 如果你有疑問,請使用cryptographicaly安全隨機數發生器 。
- 不要假設你的軟件將被部署到類似的試驗機的環境。 有衝突的組件(如在這種情況下,防病毒)能夠而且將會導致意外的行為。
- 文件上傳始終是Web應用程序脆弱的部位,OWASP有一些很好的指導方針有關安全處理它們。
- 做你的開發團隊遵循安全重點開發方法呢? 因為一個好的方法是一種高質量的產品的基礎。
- 你執行你的財務應用程序正規,技術安全測試? 因為人們犯錯誤。
- 你確定在合理的時間內生產系統所發現的漏洞? 因為測試沒有價值,如果它永遠固定的結果。
============
*---Share-known virus and vulnerability analysis expert information disclosure,,Famous "Wojciech Dworakowski" Mr. Analysis Project article - "virtual bank robbery,, in real life !"[This week the Polish banking through its online banking! interface breakthrough reportedly attackers stole $ 250.000, 80.000 customers now use personal information to blackmail the bank alleged attacker using a remote code execution vulnerability...]- Detailed graphics -(very carefully and professional the well-known expert)-
---分享著名分析病毒及漏洞,,信息洩露專家"沃伊切赫Dworakowski"先生的分析專案文章-"虛擬銀行劫案 ,,在現實生活中 ![本週波蘭銀行通過其網上銀行的界面突破。據報導,攻擊者竊取了250.000美元,現在使用的80.000客戶的個人信息來要挾銀行。據稱攻擊者利用一個遠程執行代碼漏洞,...]-圖文詳解-(非常仔細及專業的著名專家)-
---Teilen bekannten Viren und Schwachstellen analyse-Experte Offenlegung von Informationen,, Famous "Wojciech Dworakowski" Mr. Analysis Project Artikel - "virtuelle Banküberfall,, im wirklichen Leben!" [Diese Woche hat die polnischen Banken durch ihre Online-Banking! Schnittstelle Durchbruch angeblich Angreifer habe $ 250.000, 80.000 Kunden nutzen heute persönlichen Informationen, um die Bank angeblich erpressen Angreifer mit einem Remotecodeausführung ermöglichen...] - Detaillierte Grafiken - (sehr sorgfältig und professionell der bekannte Experte)-
---株式既知のウイルスや脆弱性分析の専門家の情報開示,,有名な「ヴォイチェフDworakowski "ミスター分析プロジェクトの記事 - 「仮想銀行強盗,,実際の生活の中で!」【今週ポーランドの銀行のオンラインバンキングを介して!詳細なグラフィックス -- (非常に慎重とプロのよく知られた専門家)インタフェースブレークスルーは伝え攻撃者は...] 80.000顧客は、リモートでコードが実行される脆弱性を使用して銀行疑惑攻撃者を脅迫するために個人情報を使用し、250.000ドルを盗みました -
---Partager connu informations virus et la vulnérabilité des analyses d'experts divulgation,, Famous "Wojciech Dworakowski" de l'article de M. Analyse de projets - "vol de banque virtuelle ,, dans la vraie vie!" [Cette semaine, le bancaire polonais à travers sa banque en ligne! Interface percée aurait volé attaquants $ 250,000, 80.000 clients utilisent maintenant des renseignements personnels pour faire chanter la banque présumé agresseur en utilisant une vulnérabilité d'exécution de code à distance...] - Des graphismes détaillés - (très soigneusement et l'expert bien connu professionnelle)-
--- 공유 알려진 바이러스 및 취약성 분석 전문 정보 공개,, 유명한 "요이치 Dworakowski"고 분석 프로젝트의 기사 - "가상 은행 강도,, 현실에서!"[이번 주 폴란드 은행의 온라인 뱅킹을 통해! (매우 신중하고 전문 잘 알려진 전문가) - 자세한 그래픽 - 인터페이스 돌파구는 소문에 공격자는...] $ 250.000, 80.000 고객이 지금은 원격 코드 실행 취약점을 이용하여 은행 주장 공격자를 협박하기 위해 개인 정보를 사용 훔친 -
**All The World Lauguage**-
http://melody-free-shaing.blogspot.com/2015/06/share-known-virus-and-vulnerability.html
===Melody.Blog===Thankgiving===>/
&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&



沒有留言:
張貼留言
window.___gcfg = {
lang: 'zh-CN',
parsetags: 'onload'
};