
-Update(4).Shating by My dear Anonymous---China Blocks Reuters Website After DDoS Attack On The Great Firewall of China!! Posted on March 21, 2015 by Waqas ]---更新(4).由偉大俠義匿名軍團發佈---"中國塊路透社網站的DDoS攻擊中國的長城防火牆後 發表於 2015年3月21日 由瓦卡斯] !!**All The World Lauguage**-*---Update(4).Our friendly dear Anonymous legion of chivalry on the mainland Communist devil evil cult sensation Chinaman attack big action! Mainland Communist devil evil cult Chinaman corruption and instructions Hong Kong thief wolf @Leung chun-ying suppress slave 'Scholarism '', ''the Council of '' more absurd extreme of the Communist Party of the General asked the court to
proceedings?! Details see text [reported by Apple Daily] - and this second round sniper devil cult Communist mainland Chinaman did not humanitarian law and justice not to dissidents severely beaten, and even destroyed the lives of big revenge is coming! - we pro Love friendly Anonymous released a chivalrous Legion (1) .NamasteAnonNamaste - # OpChina Hello Government, you have failed as expected: d [-_-] b ^^ Mirror http://dlvr.it/9L44Hd] via Doemela]-

(2).AnonymousAnonymousGlobo - # OpChina: 5000 CC leaked, maybe some needy institution is in need of donations;)
[http://www.portalhmarin.com.br/arquivos/downloads/37/OpChina!.txt ...] #AntiSec #Anonymous]- (3).T10z1nh0 Aka Subkelz @ h4x0s - 28 sites of China hacked ByHagashTeam #OpChina [ http://pastebin.com/H6ew5nwM]-(4).T10z1nh0 Aka Subkelz @ h4x0s - 5000 Credit Card #OpChinaAnonymousGlobo [http://www.portalhmarin.com.br/arquivos/downloads/37/OpChina.txt...]- please enjoy anonymity with great precision posture ~^^-
---更新(4).我們親爱友好的匿名俠義軍團對大陸邪教惡魔共產黨支那人轟動攻擊的大行動!大陸邪教惡魔共產黨支那人貪污和指令香港賊狼@梁振英奴隸打壓''學民思潮'',''學聯聯會'',更有荒謬極的共產黨妖魔律政司要求法庭批准對20名在佔旺區清場時被捕的示威者,展開刑事藐視法庭的法律程序?!詳見內文[由蘋果日報報導]-而這次第二輪狙擊大陸邪教惡魔共產黨支那人沒人道沒公義沒法律和把異見人士打得頭破血流,甚至殘害生命!大報復來臨了-我們親爱友好的匿名俠義軍團發佈出(1).Namaste @AnonNamaste--#OpChina Hello Government, you have failed as expected: d[-_-]b ^^ Mirror http://dlvr.it/9L44Hd] via @Doemela ]-
(2).Anonymous@AnonymousGlobo--#OpChina: 5000 CC leaked, maybe some needy institution is in need of donations! ;)[ http://www.portalhmarin.com.br/arquivos/downloads/37/OpChina.txt…] #AntiSec #Anonymous]- (3).T10z1nh0 Aka Subkelz @h4x0s--28 sites of China hacked By @HagashTeam #OpChina http://pastebin.com/H6ew5nwM]-(4).T10z1nh0 Aka Subkelz@h4x0s-- 5000 Credit Card #OpChina @AnonymousGlobo[ http://www.portalhmarin.com.br/arquivos/downloads/37/OpChina.txt…]-請各位用欣賞匿名偉大的精確姿勢~^^
**All The World Lauguage**-
**Please use the Google god of high-tech
translator to translate your national / local language ah ^^ -
**請各位使用谷歌大神的高科技翻譯器來翻譯你們的國家/地方的語言啊^^-
**지역 / 국가 언어 아 ^^ 번역 하이테크 번역기의 구글 하나님을 사용하십시오 -
**Se il vous plaît utiliser le dieu Google
de traducteur de haute technologie pour traduire votre ah langue nationale /
locale ^^-
**あなたの国内/地域言語ああ^^翻訳するハイテクトランスレータのGoogleの神を使用してください -
**Будь ласка, використовуйте бога Google
високотехнологічного перекладача, щоб перевести свій національним /
регіональним мовою ах ^^-
**กรุณาใช้พระเจ้าของ Google แปลที่มีเทคโนโลยีสูงในการแปล / ชาติภาษาท้องถิ่นของคุณอา ^^-
**Si prega di utilizzare il dio Google
Traduttore di high-tech per tradurre il vostro / ah lingua locale nazionale ^^-
**Fadlan isticmaal ilaah Google ee
turjumaan farsmada heerka sare ah loo turjumi / ka ah luuqada maxaliga ah ee
qaranka ^^-
**Gunakan dewa Google penerjemah
berteknologi tinggi untuk menerjemahkan nasional / ah bahasa lokal ^^-
**Por favor, utilice el dios Google
Traductor de alta tecnología para traducir su / ah nacional idioma local ^^-
**आफ्नो राष्ट्रिय / स्थानीय
भाषा आह ^^ अनुवाद गर्न उच्च-प्रविधी अनुवादक को गुगल देवता प्रयोग गर्नुहोस् -
**Bonvolu uzi la Google dio de alta-tech
tradukisto por traduki vian nacian / lokan lingvon ah ^^-
*Note This Sharing For/ By Anonymous~
https://www.hackread.com/china-great-cannon-blocks-websites/
‘Great Cannon’ of China Blocks Websites Like No One Else Can
China to Use Stronger Weapons to Censor the Web and it is called Great Cannon — It can block websites and interrupt international traffic like no one else.
Lately, China has been bombarding American websites with Internet traffic in a bid to take out such services that let China’s web users to view websites that have been blocked in China.
Initial security reports revealed that the services have been crippled by China via exploitation of its own internet filter that is called the Great Firewall for redirecting a barrage of internet traffic to its target destinations.
The University of California, Berkley and the University of Toronto researchers identified that the Great Firewall hasn’t been used by China at all but instead a very strong new weapon which they have labelled as the Great Cannon.
In a report published this Friday, Citizen Lab researchers explained that the Great Cannon allows China to interrupt international web traffic while it passes through Chinese websites, infect it with malicious code and repurpose the traffic that China deems appropriate.
This method was used to interrupt the advertising and web traffic for Baidu, which is the biggest search engine company in China, and redirect it at a popular site for programmers GitHub and a non-profit site that runs replicas of websites that are blocked in China called GreatFrire.org.
The attacks, researchers say, continued on Thursday but both sites kept operating normally. They suggested that the system can be equipped with many more capabilities since with just few tweaks the Great Cannon can perform surveillance on anyone who somehow manages to fetch content that’s being hosted by a Chinese computer. Spying can also be initiated even when a user visits a non-Chinese website having Chinese marketing content.
In their report the research team described: “The operational deployment of the Great Cannon represents a significant escalation in state-level information control, the normalization of widespread and public use of an attack tool to enforce censorship.”
The team has previously conducted extensive research into spying tools used by the government and identified that although the coding and infrastructure of the attacks is identical to the Great Firewall but the attacks have been launched from a different device. This device is capable of intercepting the internet traffic and also altering and redirecting it at a larger scale to just about any website. This kind of tactic is called a “man in the middle attack.”
The report also reveals that China’s latest weapon is identical to the one that has been developed and used by America’s National Security Agency (NSA) and UK’s GCHQ. The system was exposed in the classified documents that were leaked by former US intelligence contractor Edward J. Snowden. The documents revealed that the American version of this system can deploy a mechanism of programs that is capable of interrupting web traffic on a broader scale to any site of their choice. This system is utilized for performing targeted surveillance whereas China uses the Great Cannon to implement aggressive censorship.
However, the similar nature of both programs, stated researchers, may embarrass American officials. They wrote: “This precedent will make it difficult for Western governments to credibly complain about others utilizing similar techniques,” according to NY Times.
But Chinese program shows the extent to which officials in Beijing are willing to intensify censorship on the internet. James A. Lewis, the Centre for Strategic Studies in Washington security expert, states that “This is just one part of President Xi Jinping’s push to gain tighter control over the Internet and remove any challenges to the party.”
China continually has been expanding its efforts to induce aggressive form of censorship under its State Internet Information office, which has been founded by Mr. Xi to ensure control over the web within China and to suppress online activism.
Via: NY Times
Source: Citizen Lab
----------------
China’s Great Cannon
April 10, 2015Categories: Bill Marczak, John Scott-Railton, Reports and Briefings
This post describes our analysis of China’s “Great Cannon,” our term for an attack tool that we identify as separate from, but co-located with, the Great Firewall of China. The first known usage of the Great Cannon is in the recent large-scale novel DDoS attack on both GitHub and servers used by GreatFire.org.
Authors: Bill Marczak1,2,3 (Lead), Nicholas Weaver2,3 (Lead), Jakub Dalek,1 Roya Ensafi,4 David Fifield,2 Sarah McKune,1 Arn Rey, John Scott-Railton,1 Ronald Deibert,1 Vern Paxson.2,3
Affiliations: (1) Citizen Lab, Munk School of Global Affairs, University of Toronto; (2) International Computer Science Institute; (3) University of California, Berkeley; (4) Princeton University
Section 1: Introduction, Key Findings
On March 16, GreatFire.org observed that servers they had rented to make blocked websites accessible in China were being targeted by a Distributed Denial of Service (DDoS) attack. On March 26, two GitHub pages run by GreatFire.org also came under the same type of attack. Both attacks appear targeted at services designed to circumvent Chinese censorship. A report released by GreatFire.org fingered malicious Javascript returned by Baidu servers as the source of the attack.1 Baidu denied that their servers were compromised.2Several previous technical reports3 have suggested that the Great Firewall of China orchestrated these attacks by injecting malicious Javascript into Baidu connections. This post describes our analysis of the attack, which we were able to observe until April 8, 2015.
We show that, while the attack infrastructure is co-located with the Great Firewall, the attack was carried out by a separate offensive system, with different capabilities and design, that we term the “Great Cannon.” The Great Cannon is not simply an extension of the Great Firewall, but a distinct attack tool that hijacks traffic to (or presumably from) individual IP addresses, and can arbitrarily replace unencrypted content as a man-in-the-middle.
The operational deployment of the Great Cannon represents a significant escalation in state-level information control: the normalization of widespread use of an attack tool to enforce censorship by weaponizing users. Specifically, the Cannon manipulates the traffic of “bystander” systems outside China, silently programming their browsers to create a massive DDoS attack. While employed for a highly visible attack in this case, the Great Cannon clearly has the capability for use in a manner similar to the NSA’s QUANTUM system,4 affording China the opportunity to deliver exploits targeting any foreign computer that communicates with any China-based website not fully utilizing HTTPS.
Report Structure
We organize our Report as follows:Section 2 locates and characterizes the Great Cannon as a separate system;
Section 3 analyzes DDoS logs and characterizes the distribution of affected systems;
Section 4 presents our attribution of the Great Cannon to the Government of China;
Section 5 addresses the policy context and implications;
Section 6 addresses the possibility of using the Great Cannon for targeted exploitation of individual users.
Section 2: The Firewall & The Cannon: Separate Systems, Significant Similarities
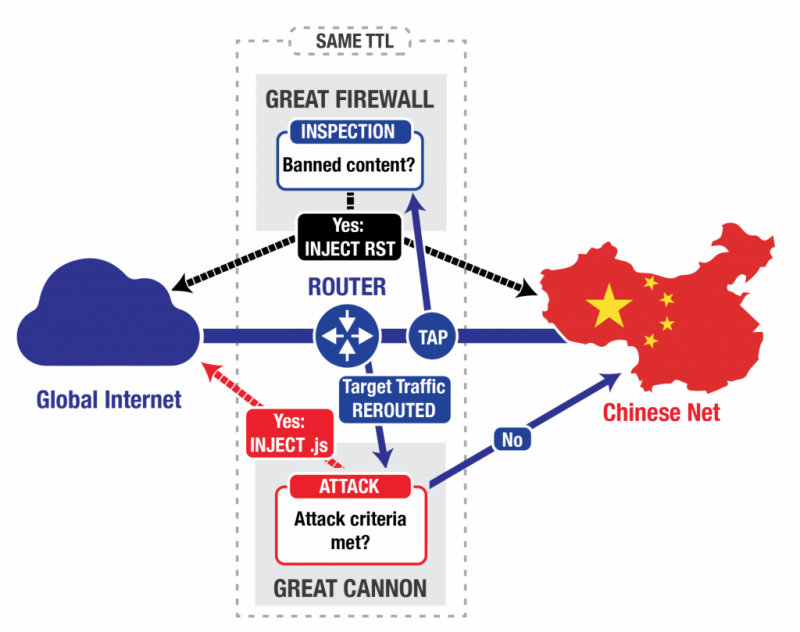
In general, a firewall serves as an in-path barrier between two networks: all traffic between the networks must flow through the firewall. In contrast, an on-path system like the Chinese “Great Firewall” (GFW) sits off to the side: it eavesdrops on traffic between China and the rest of the world (TAP in Figure 1), and terminates requests for banned content (for example, upon seeing a request for “http://www.google.com/?falun”,5 regardless of actual destination server) by injecting a series of forged TCP Reset (RST) packets that tell both the requester and the destination to stop communicating (INJECT RST in Figure 1).6 On-path systems have architectural advantages for censorship, but are less flexible and stealthy than in-path systems as attack tools, because while they can inject additional packets, they cannot prevent in-flight packets (packets that have already been sent) from reaching their destination.7 Thus, one generally can identify the presence of an on-path system by observing anomalies resulting from the presence of both injected and legitimate traffic.8The GFW keeps track of connections and reassembles the packets (“TCP bytestream reassembly”) to determine if it should block traffic. This reassembly process requires additional computational resources, as opposed to considering each packet in isolation, but allows better accuracy in blocking. While a web request often fits within a single packet, web replies may be split across several packets, and the GFW needs to reassemble these packets to understand whether a web reply contains banned content.
On any given physical link (e.g., a fiber optic cable), the GFW runs its reassembly and censorship logic in multiple parallel processes9 (perhaps running on a cluster of many different computers). Each process handles a subset of the link’s connections, with all packets on a connection going to the same process. This load-balanced architecture reflects a common design decision when a physical link carries more traffic than a single computer can track. Each GFW process also exhibits a highly distinctive side-channel — it maintains a counter, and numbers the forged TCP Reset packets it injects (via the value of the IP TTL field).
The Great Cannon (GC) differs from the GFW: as we will show, the GC is an in-path system, capable of not only injecting traffic but also directly suppressing traffic, acting as a full “man-in-the-middle” for targeted flows. The GC does not actively examine all traffic on the link, but only intercepts traffic to (or presumably from) a set of targeted addresses. It is plausible that this reduction of the full traffic stream to just a (likely small) set of addresses significantly aids with enabling the system to keep up with the very high volume of traffic: the GC’s full processing pipeline only has to operate on the much smaller stream of traffic to or from the targeted addresses. In addition, in contrast to the GFW, the GC only examines individual packets in determining whether to take action, which avoids the computational costs of TCP bytestream reassembly. The GC also maintains a flow cache of connections that it uses to ignore recent connections it has deemed no longer requiring examination.
The GC however also shares several features with the GFW. Like the GFW, the GC is also a multi-process cluster, with different source IP addresses handled by distinct processes. The packets injected by the GC also have the same peculiar TTL side-channel as those injected by the GFW, suggesting that both the GFW and the GC likely share some common code. Taken together, this suggests that although the GC and GFW are independent systems with different functionality, there are significant structural relationships between the two.
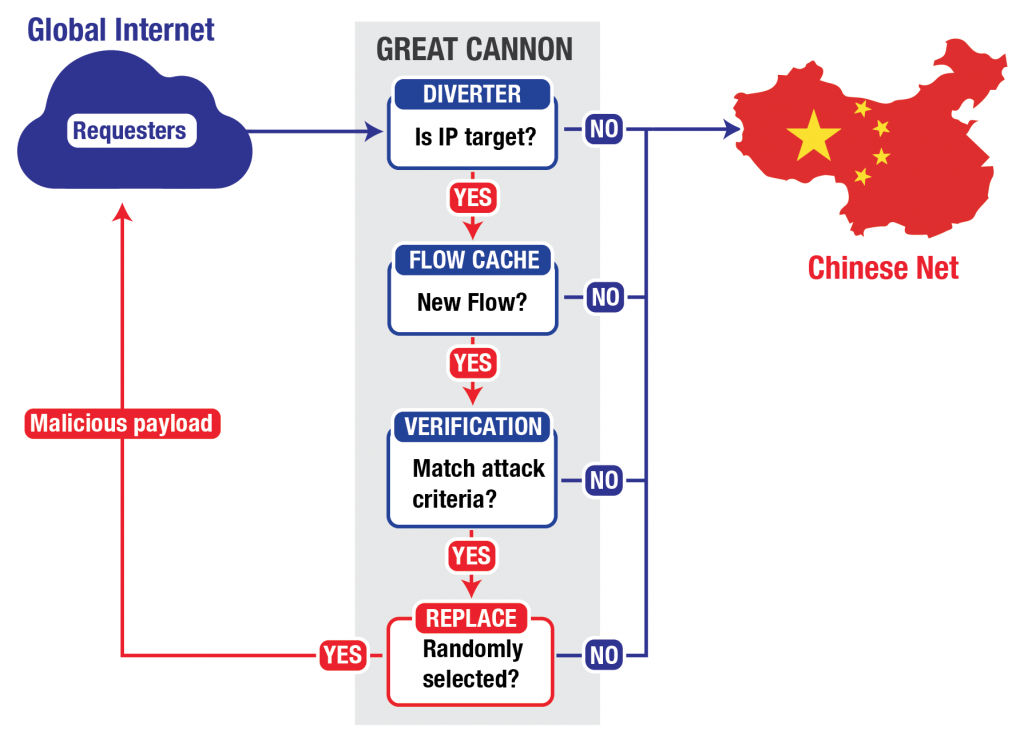
In the attack on GitHub and GreatFire.org, the GC intercepted traffic sent to Baidu infrastructure servers that host commonly used analytics, social, or advertising scripts. If the GC saw a request for certain Javascript files on one of these servers, it appeared to probabilistically take one of two actions: it either passed the request onto Baidu’s servers unmolested (roughly 98.25% of the time), or it dropped the request before it reached Baidu and instead sent a malicious script back to the requesting user (roughly 1.75% of the time). In this case, the requesting user is an individual outside China browsing a website making use of a Baidu infrastructure server (e.g., a website with ads served by Baidu’s ad network). The malicious script enlisted the requesting user as an unwitting participant in the DDoS attack against GreatFire.org and GitHub.
Localizing the Cannon
The GFW continues to operate as normal: on-path and statefully
We began our investigation by confirming the continued normal operation of the GFW’s censorship features. We did so employing measurements between our test system outside of China and a Baidu server that we observed returning the malicious Javascript. We sent the Baidu server a request that the GFW would process as a query for “http://www.google.com/?falun”, a URL long known10 to trigger the GFW to inject forged TCP Resets to terminate the connection. This packet capture shows the results of our experiment, which confirmed that the normal, well-understood operation of the GFW continues. Note that the capture includes both the injected TCP Reset and, later, the legitimate response (an HTTP 403 reply) from the Baidu server. This occurs because the GFW operates as an on-path system, and, as discussed earlier, on-path systems cannot prevent in-flight packets from reaching their destination.Localizing the GFW
We then localized where (with respect to our measurement system) in the network topology the GFW operates, as follows. For a given measurement packet, we can control how far into the network it transits from our measurement system to its destination by controlling the packet’s TTL value. The TTL value determines after how many intermediate hops a packet will be discarded by the Internet’s internal routers. We sent the “Falun” queries from our test system to the Baidu server with TTL values increasing from 1 on up. We observed that the GFW’s TCP Reset injection only occurred when we sent packets with TTL values >= 18, suggesting that the GFW acts on traffic flowing between the 17th and 18th hop along the path from our test system to the Baidu server (which was itself 24 hops away from our test system). This packet capture shows our localization results.11The GC operates as a separate, in-path system
As noted previously, our traces of GFW operation showed both the injected TCP Reset, as well as the legitimate server reply. In contrast, no legitimate server reply accompanied the injected malicious reply from the GC. We ran further testing, where we retransmitted our request to Baidu over the same connection, and with the same sequence numbers, after we received a malicious response. We observed Baidu responding as normal to the retransmitted request. Thus, we conclude12 that the GC dropped our request before it reached Baidu, a capability not present in the GFW.13We also checked whether the GFW and GC might share the same injector device,14 but found no evidence that they do. In particular, from a given TCP source port, we sent one request designed to trigger GC injection, followed by a request designed to trigger GFW injection. We repeated the experiment from a number of source ports. While packets injected by both the GFW and GC exhibited a similar (peculiar) TTL side-channel indicative of shared code between the two systems, we found no apparent correlation between the GFW and GC TTL values themselves.
The GC appears to be co-located with the GFW
We used the same TTL technique to localize the GC on the path between our test system and the Baidu server. We found that for our path, the GC acted on traffic between hop 17 and hop 18, the same link we observed as responsible for the GFW. We also observed that unlike the GFW, we could trigger the GC using “naked” requests (i.e., requests sent in isolation, with no previous TCP SYN as required for standard communication). Acting on “naked” requests implies that the GC’s content analysis is more primitive (and easily manipulated), but does offer significant performance advantages, as the GC no longer needs to maintain complex state concerning connection status and TCP bytestream reassembly.We also checked two separate servers in China whose traffic the GC targets to observe whether the GC existed along with the Great Firewall on multiple network paths. From our measurement system outside of China, we examined the path to both 115.239.210.141 and 123.125.65.120. For 115.239.210.141, the GFW and the GC both exist between hop 12 and 13, on the link between 144.232.12.211 and 202.97.33.37, as the traffic enters China Telecom. For 123.125.65.120, the GFW and GC both exist between hop 17 and 18, on the link between 219.158.101.61 and 219.158.101.49, belonging to China Unicom. A previous report by Robert Graham used the same TTL technique to conclude that on one link, the GC was located “inside China Unicom infrastructure.”15
The GC is currently aimed only at specific destination IP addresses
When we probed an IP address adjacent to the Baidu server (123.125.65.121), the GC ignored the requests completely, although the GFW acted on censorable requests to this host.Unlike the GFW, the GC only acts on the first data packet of a connection
For a given source IP address and port, the GC only examines the first data packet sent when deciding whether to inject a reply. To avoid examining subsequent packets requires remembering which connections it has examined in a flow cache. Unlike the GFW, the GC does not reassemble packets, a significant implementation difference. In addition, the GC will process invalid HTTP requests, while the GFW will not, also indicating differing implementations.We confirmed these behaviors by sending a number of probes to the Baidu server, requesting resources that trigger the GC’s injection. Each probe had a different source port. We sent 500 probes, each with the request split across three packets (so 1,500 packets total). The GC ignored each probe. We then sent 500 probes where the first packet’s data is an invalid HTTP request, and the second packet’s data is a complete, valid request for a targeted resource. The GC ignored each probe. We then sent a final 500 single-packet probes, each containing a complete, valid request for a targeted resource, to confirm normal GC operation. As expected, the GC injected malicious content in some cases, seemingly based on its probabilistic decision-making process.
How big is the GC flow cache?
We attempted to completely fill the GC flow cache by sending packets to the Baidu server with different source IP addresses and ports, while probing to see whether the entries that we previously added had now expired. Our attempt suggests that at least in some cases, the GC flow cache between our test system and the Baidu server supports up to around 16,000 entries for a single sending IP address.Unlike the GFW, the GC appears to act probabilistically
Censorship systems generally operate in a deterministic fashion: they aim to block all content that matches the target criteria. The GC, on the other hand — at least for this particular attack — appears to act probabilistically, and ignores most of the traffic it could act on. In one test, it completely ignored all traffic from one of four measurement IP addresses, and on the three other measurement IP addresses it only responded to 526 requests out of an initial 30,000 from the three (1.75%).The cache capacity test also provides evidence that the GC’s probabilistic choice occurs on the decision to act on a particular flow, and not as some sort of pre-filter for reducing analysis load. When we succeeded in completely filling the flow cache, subsequently injected packets occurred for different source ports than in the initial test. If the GC only intercepted a subset of flows to the target IP address, we would expect subsequent injections to appear for the same flows, since most schemes to probabilistically select flows for interception (such as hashing the connection 4-tuple) would select the same set of flows the second time around.
Does the GC have a load-balanced architecture?
We determined that the GC uses a separate flow cache for different source IP addresses, and that packets injected from different source IP addresses have distinct TTL side-channels. This finding suggests a load-balanced architecture similar to the GFW, where packets are routed to GC nodes based on source IP address. We then sent traffic alternating from four measurement IP addresses in an attempt to fill a 16,000 entry cache. This attempt did not manage to fill the cache, suggesting that the GC not only processed the different source IP addresses with different injection elements, but did so using different flow caches. As stated before, one of the four source IP addresses never received any injected replies.Section 3: Analysis of the DDoS Logs from the attack against GreatFire
The staff of GreatFire.org provided the authors with server logs covering the period of March 18 to 28.16 (A report previously published by Great Fire uses a different sample.17) This period appears to capture the end of the DDoS attack on GreatFire.org’s services, as shown by the size of server log files over this period:To keep our analysis tractable, we examined a sample of the data from March 18th 11:00 GMT to March 19th 7:00 GMT, as seen from two of the three most commonly seen backend servers. For each hour, we selected 30MB of compressed logs for each server.18 The total sample includes 16,611,840 web requests, with 13,183 unique source IP addresses. We used the MaxMind GeoIP2 Lite database19 from March 3rd, 2015 to assign a country of origin to each source IP address. For any IP address that did not result in a definite geolocation using this tool (31 addresses), we looked up the address manually using the iplocation.net service.
The figure below summarizes the top countries of origin, with China added for comparison.
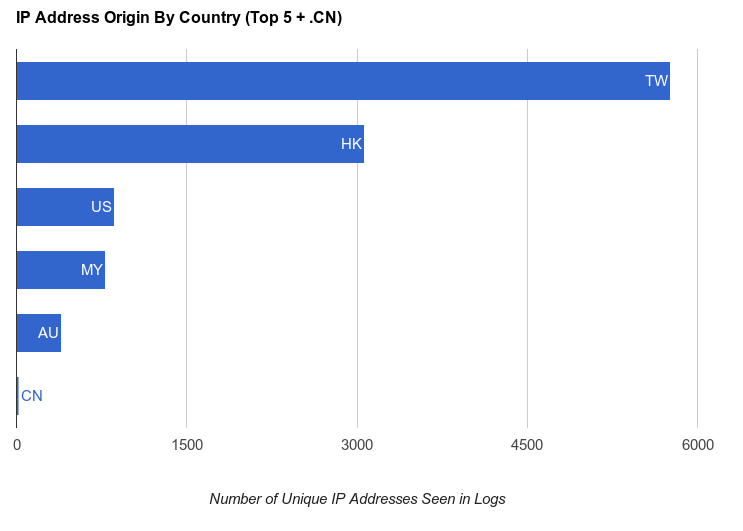
Figure 3. Number
of Unique IP addresses seen in DDoS log sample showing the top 5
countries/regions, with Chinese traffic included for comparison.
To determine which websites have their responses altered by the injection of malicious code, we extracted the domain names of the 25 most frequently seen referrers in our dataset,20 finding that these domains account for 55% of the total requests in the sample.
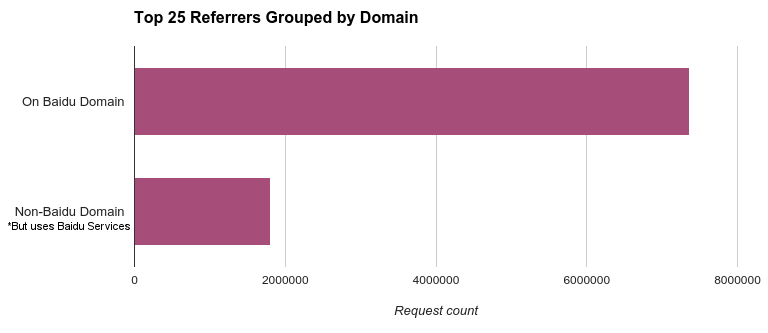
Figure 4. Top
25 referrers found in the DDoS logs, grouped by domain. The top bar
reflects domains directly in the baidu.com DNS space. Manual
verification confirms that all top 25 referrers use Baidu services such
as advertising or analytics.
We examined the top 25 domains, and linked each one to Baidu: in each case, the site is either a Baidu property or uses Baidu analytics, advertisements, or static resources.22 This finding indicates that Baidu was a major injection target for this attack. According to Alexa statistics, Baidu itself is the fourth-most visited site globally, the highest ranking China-based site on the global list,23 and has received an estimated 4.99 million unique visitors from the US alone in the past 30 days.24
We speculate that Baidu was chosen as an injection target because it is a simple way to target many users.
Section 4: Attributing the Great Cannon to the Chinese Government
We believe there is compelling evidence that the Chinese government operates the GC. In recent public statements, China has deflected questions regarding whether they are behind the attack, instead emphasizing that China is often itself a victim of cyber attacks.25Where is the GC Located?
We tested two international Internet links into China belonging to two different Chinese ISPs, and found that in both cases the GC was co-located with the GFW. This co-location across different ISPs strongly suggests a governmental actor.Who built the Great Cannon?
That the GFW and GC have the same type of TTL side-channel suggests that they share some source code. We are unaware of any public software library for crafting packets that introduces this type of TTL side-channel.What is the Great Cannon’s Function?
Our observations indicate that the GC’s design does not reflect technology well-suited for performing traffic censorship. Its operation only examines the first data packet of a given connection, which provides a weak censorship mechanism compared to the GFW. More generally, the GC’s design does not, in practice, enable it to censor any traffic not already censorable by the GFW. Thus, the evidence indicates that the GC’s role is to inject traffic under specific targeted circumstances, not to censor traffic.Who is the Great Cannon attacking?
The DDoS attack launched by the GC using “bystander” machines directly aligns with known political concerns of the Chinese government. The Cyberspace Administration of China has previously referred to GreatFire as a “foreign anti-Chinese organization” (境外反华组).26 The particular GreatFire service targeted in this attack provides proxies to bypass the GFW using encrypted connections to Amazon’s CloudFront cloud service.GreatFire also hosts two GitHub repositories, https://gitub.com/greatfire and https://github.com/cn-nytimes, that provide technology for users who wish to circumvent Chinese government censorship. The attack on GitHub specifically targeted these repositories, possibly in an attempt to compel GitHub to remove these resources. GitHub encrypts all traffic using TLS, preventing a censor from only blocking access to specific GitHub pages. In the past, China attempted to block Github, but the block was lifted within two days, following significant negative reaction from local programmers.27
Section 5: Policy Context and Implications
This section describes some policy implications of deploying the Great Cannon, addresses the impact of targeting Baidu traffic specifically, and discusses the Chinese authorities that may be involved in operation of the GC.Implications of the GC for Chinese Policy
Deploying the Great Cannon is a major shift in tactics, and has a highly visible impact. It is likely that this attack, with its potential for political backlash,28 would require the approval of high-level authorities within the Chinese government. These authorities may include the State Internet Information Office (SIIO),29 which is responsible for Internet censorship. It is also possible that the top body for cybersecurity coordination in China, the Cybersecurity and Informatization Leading Group (CILG),30 would have been involved. The CILG is chaired by Xi Jinping and includes as members senior leaders from across the government; its administrative office is housed within the SIIO.31The government’s reasoning for deploying the GC here is unclear, but it may wish to confront the threat presented to the Communist Party of China’s (CPC) ideological control by the “collateral freedom” strategy advanced by GreatFire.org32 and others. The attack was exceptionally costly to GreatFire, according to their public statements,33 as well as disruptive to the companies that hosted GreatFire content. Such a disruption could be both an attempt to block the operations of an undesirable resource, and a signal sent to other organizations of the potential price tag for this kind of activity. Deployment of the GC may also reflect a desire to counter what the Chinese government perceives as US hegemony in cyberspace.
This approach would be consistent with the CPC’s paramount focus on protecting “domestic stability” (and its own authority) against entities it has identified as “foreign hostile forces,” including not only governments but also Western media outlets (such as the New York Times) and NGOs or other civil society actors (such as GreatFire.org).34 According to such a world view, the collateral freedom strategy is a provocative, hostile act that threatens China’s security.
Implications of Using Traffic to Baidu Services
The incorporation of Baidu in this attack suggests that the Chinese authorities are willing to pursue domestic stability and security aims at the expense of other goals, including fostering economic growth in the tech sector. Selecting Baidu’s international traffic may appear counterproductive given the importance of Baidu to the Chinese economy: the company enjoys stature as one of China’s “big three” Internet firms, alongside Alibaba and Tencent,35 and currently ranks as the top site in China.36 While its shares came under pressure after the February release of its Q4 and fiscal year 2014 reports,37 its total revenue in 2014 was USD $7.906 billion, with online marketing revenues for that period valued at USD $7.816 billion.38“Service interruptions could reduce our revenues and profits and damage our brand if our systems are perceived to be unreliable.”39Baidu has denied involvement in the attack and asserted its internal security was not compromised.40 Yet the targeting of international visitors trying to reach sites that are Baidu properties, or that use Baidu analytics, advertisements, or static resources, could undermine the company’s reputation and its appeal to overseas users and advertisers.
Baidu writes in its SEC filings that it was the target of legal action in the United States in 201141 for complying with Chinese censorship. Baidu explicitly notes that cooperation and coordination with Chinese censorship authorities could be costly in terms of brand image, profit, and stockholder confidence.
“our compliance with PRC regulations governing internet access and distribution of news and other information over the internet may subject us to negative publicity or even legal actions outside of China.”42Moreover, exploiting Baidu’s international reach as a means for conducting digital attacks belies the government’s recent commitment to enhance the global presence of Internet companies. At the meeting of the National People’s Congress on March 5, 2015, Premier Li Keqiang (who is also Vice-Chair of the CILG) announced:
We will develop the “Internet Plus” action plan to integrate the mobile Internet, cloud computing, big data, and the Internet of Things with modern manufacturing, to encourage the healthy development of e-commerce, industrial networks, and Internet banking, and to guide Internet-based companies to increase their presence in the international market.43This goal – which closely echoes that contained in a draft declaration presented (but not passed) at the November 2014 Wuzhen World Internet Conference44 – may not come to fruition if Chinese domestic companies appear unreliable, their business objectives secondary to other objectives of the Chinese Government.
Chinese authorities may, however, be betting that their use of Baidu traffic to mount this DDoS attack will ultimately be perceived as an isolated occurrence, a sort of “force majeure,” with limited impact on Baidu’s long-term economic prospects – particularly given Baidu’s apparent status as unwitting victim and its strong market position.
Additionally, Baidu’s CEO Robin Li is a member of the Chinese People’s Political Consultative Conference45 and well-positioned for lucrative government contracts going forward — such as his artificial intelligence project “China Brain,” for which he has sought military support.46 He may have little personal incentive (let alone opportunity, given the existing legal and regulatory framework applicable to Internet companies in China47) to challenge this action by the government.
Thinking About Authorities Who May Be Responsible for Implementing The Great Cannon
Even for the GFW, it is difficult to pinpoint the precise authorities behind its deployment, or its operators and origins. This makes understanding the origins of the GC equally challenging. However, some clues are available. For example, the shared source code and co-location between the GFW and GC suggest that the GC could have been developed within the same institutional framework as the GFW. We might therefore draw further insight into the GC by assessing what we know about the GFW.Some reports characterize the GFW as an element of China’s “Golden Shield” project,48 under the authority of the Ministry of Public Security. However, unverified insider information ‘leaked’ online suggests that the GFW was developed within a separate entity: the “National Computer Network and Information Security Management Center” (国家计算机网络与信息安全管理中心) (hereafter, “the Center”).49 Little is publicly known about the Center. It appears to bear close relationship50 to the National Computer Network Emergency Response Technical Team/Coordination Center of China (CNCERT/CC) run by the Ministry of Industry and Information Technology (MIIT) — indeed, the listed address for CNCERT/CC is the same as that of the Center as indicated on its patent applications — and the former National Network and Information Security Coordination Team,51 a subcommittee of the State Informatization Leading Group subsumed by the CILG in 2014.52 Notably, “MIIT also regulates China’s six Internet service providers (ISPs), which in turn are expected to monitor and filter content on their networks according to censorship guidelines established by the State Council Information Office and the SIIO.”53 Those ISPs include China Telecom and China Unicom, on the links of which we co-located the GFW and GC (see above).
It is unknown whether the GFW and/or the GC are in fact maintained (or may have been developed in whole or in part) by the National Computer Network and Information Security Management Center. However, patent applications filed by this entity, taken together, appear to indicate a mandate for large scale network surveillance, filtering, and defense. The Center has filed nearly 100 patent applications,54 for designs such as “Method for detecting unexpected hot topics in Chinese microblogs;” “Method and system for recognizing Tibetan dialects;” “Website classifying method;” “Method and system for intelligent monitoring and analyzing under cloud computing;” “Method and device for managing global indexes of mass structured log data;” “Method, device and system for traffic monitoring and switching;” “Image searching/matching method and system for the same;” and “Internet basic information management system” (this last “comprises a national-level management sub-system, a provincial management sub-system and an enterprise management sub-system” that “can perform effective supervision on the Internet basic information throughout the country”). Moreover, according to state media, during the time of the GFW’s development the so-called “father of the Great Firewall,” Fang Binxing, was employed at CNCERT/CC,55 an entity that appears closely tied to the Center.56 Fang is likewise listed as an inventor on a 2008 patent application by the Center, indicating some collaboration with the Center prior to that point.
While we cannot determine the exact role played by the Center, the patent documentation and the Center itself require further research and analysis to determine whether they are relevant to operation of the GC, or present other human rights-related concerns.
Section 6: Concluding Remarks: The Capability for Targeted Exploitation by China
We conclude with some remarks about the precedent set by China in the use of the GC and outline further implications for targeted exploitation.The attack launched by the Great Cannon appears relatively obvious and coarse: a denial-of-service attack on services objectionable to the Chinese government. Yet the attack itself indicates a far more significant capability: an ability to “exploit by IP address”. This possibility, not yet observed but a feature of its architecture, represents a potent cyberattack capability.
A technically simple change in the Great Cannon’s configuration, switching to operating on traffic from a specific IP address rather than to a specific address, would allow its operator to deliver malware to targeted individuals who communicates with any Chinese server not employing cryptographic protections. The GC operator first needs to discover the target’s IP address and identify a suitable exploit. The operator then tasks the GC to intercept traffic from the target’s IP address, and replace certain responses with malicious content. If the target ever made a single request to a server inside China not employing encryption (e.g., Baidu’s ad network), the GC could deliver a malicious payload to the target. A target might not necessarily realize that their computer was communicating with a Chinese server, as a non-Chinese website located outside China could (for example) serve ads ultimately sourced from Chinese servers.
Since the GC operates as a full man-in-the-middle, it would also be straightforward to have it intercept unencrypted email to or from a target IP address and undetectably replace any legitimate attachments with malicious payloads, manipulating email sent from China to outside destinations. Even email transmission protected by standard encryption (STARTTLS) can be undermined because the GC is in a position to launch a “downgrade” attack, steering the transmission to only use legacy, unencrypted communication.
Our findings in China add another documented case to at least two other known instances of governments tampering with unencrypted Internet traffic to control information or launch attacks — the other two being the use of QUANTUM by the US NSA and UK’s GCHQ. In addition, product literature from two companies, FinFisher and Hacking Team, indicate that they sell similar “attack from the Internet” tools to governments around the world.57 These latest findings emphasize the urgency of replacing legacy web protocols, like HTTP, with their cryptographically strong versions, like HTTPS.
We remain puzzled as to why the GC’s operator chose to first employ its capabilities in such a publicly visible fashion. Conducting such a widespread attack clearly demonstrates the weaponization of the Chinese Internet to co-opt arbitrary computers across the web and outside of China to achieve China’s policy ends. The repurposing of the devices of unwitting users in foreign jurisdictions for covert attacks in the interests of one country’s national priorities is a dangerous precedent — contrary to international norms and in violation of widespread domestic laws prohibiting the unauthorized use of computing and networked systems.
Acknowledgements
Special thanks to: Adam Senft (Citizen Lab) and Paul Pearce (UC Berkeley, ICSI).We wish to acknowledge GreatFire for making their logs available to us for analysis.
We also express our deep gratitude to several individuals, anonymous or pseudonymous at their request, including “Jack B,” who aided us in understanding elements of the attack in the early days, and others who helped us formulate and develop this report.
Footnotes
1 Using Baidu 百度 to steer millions of computers to launch denial of service attacks,” Anonymous author, March 25, 2015 (https://drive.google.com/file/d/0ByrxblDXR_yqeUNZYU5WcjFCbXM/view?pli=1)2 http://www.theverge.com/2015/3/27/8299555/github-china-ddos-censorship-great-firewall
3 Appendix C: Related Technical Reports
4 http://www.wired.com/2014/03/quantum/
5 As discussed further below, this specific URL consistently triggers GFW responses, even though if actually sent to www.google.com it simply returns the Google home page.
6 See https://www.cs.unm.edu/~crandall/concept_doppler_ccs07.pdf for a description of the GFW’s general operation using injected Reset packets.
7 Although, the GFW does send injected RSTs to both the requester and destination, these RSTs may arrive too late to suppress transmission of some subsequent packets.
8 See http://www.icsi.berkeley.edu/pubs/networking/ndss09-resets.pdf for a description of how to detect injected RST packets. The same techniques apply to detecting injected data packets.
9 For information on both the parallel nature and the TTL sidechannel present in the GFW, see https://www.usenix.org/system/files/conference/foci14/foci14-anonymous.pdf
10 https://www.cs.unm.edu/~crandall/concept_doppler_ccs07.pdf
11 The packet capture also confirms the stateful nature of the GFW’s content analysis: it does not inject a TCP Reset unless it first observes a TCP SYN and an ACK for the SYN/ACK for the connection.
12 If the GC did not drop requests sent to Baidu, then Baidu would have received our first request (which the GC responded to), and would have ignored our subsequent, duplicate request, as dictated by the TCP protocol. We verified that when the GC did not inject a response, Baidu did indeed ignore the duplicate request.
13 Technically complex situations exist in which an on-path system like the GFW could conceivably prevent the appearance of a response from Baidu by disrupting session initiation. We conducted extensive measurements assessing this possibility. We omit those results from this report because the “retransmission” measurement discussed above definitively rules out that possibility, rendering the measurements moot.
14 Analogous systems to the GC, like QUANTUM, make the architectural decision of having the injector as a distinct device from the rest of the system.
15 http://blog.erratasec.com/2015/04/pin-pointing-chinas-attack-against.html
16 1.1TB, compressed. Note that the logs include both malicious and non-malicious traffic
17 https://drive.google.com/file/d/0ByrxblDXR_yqeUNZYU5WcjFCbXM/view?pli=1
18 Files were randomly selected amongst a list of files that were near 30MB. This size was selected because it was largest file size that was present in all timestamp hours we focused on.
19 http://dev.maxmind.com/geoip/legacy/geolite/
20 Note that the malicious requests are being generated by Javascript. When a script makes a web request, the web browser sets the “Referer” header on the request to the URL of the page that loaded the script.
21 It is typical for web advertisements to be displayed in iframes. This causes the “Referer” header to report the advertisement service, not the hosting page.
22 See Appendix A.
23 Alexa, “The top 500 sites on the web,” http://www.alexa.com/topsites (accessed April 8, 2015).
24 Alexa, “Site overview: baidu.com,” http://www.alexa.com/siteinfo/baidu.com (accessed April 8, 2015).
25 Ministry of Foreign Affairs of the People’s Republic of China, “Foreign Ministry Spokesperson Hua Chunying’s Regular Press Conference,” March 30, 2015, http://www.fmprc.gov.cn/mfa_eng/xwfw_665399/s2510_665401/2511_665403/t1250354.shtml.
26 http://www.cac.gov.cn/2015-01/22/c_1114097853.htm
27 http://www.computerworld.com/article/2493478/internet/github-unblocked-in-china-after-former-google-head-slams-its-censorship.html
28 Particularly after the Snowden disclosures, and the public / state outcry associated with the NSA’s QUANTUM system and other programs, the Chinese government would presumably be aware of the significant international political ramifications of a decision to use the GC to target overseas entities, and escalate the matter accordingly.
29 Note: also referred to as the Cyberspace Administration of China. “China sets up State Internet information office,” Xinhua, May 4, 2011, at http://www.chinadaily.com.cn/china/2011-05/04/content_12440782.htm.
30 See Jon R. Lindsay, “Introduction–China and Cybersecurity: Controversy and Context,” in China and Cybersecurity: Espionage, Strategy, and Politics in the Digital Domain, ed. Jon R. Lindsay et al. [New York: Oxford University Press, 2015], 13-14; Adam Segal, “China’s New Small Leading Group on Cybersecurity and Internet Management,” Council on Foreign Relations: Asia Unbound, February 27, 2014, http://blogs.cfr.org/asia/2014/02/27/chinas-new-small-leading-group-on-cybersecurity-and-internet-management/.
31 For discussion and a diagram of institutions involved in China’s national cybersecurity system, see Jon R. Lindsay, “Introduction–China and Cybersecurity: Controversy and Context,” in China and Cybersecurity: Espionage, Strategy, and Politics in the Digital Domain, ed. Jon R. Lindsay et al. [New York: Oxford University Press, 2015], 6-15.
32 Charlie, “Collateral Freedom and the not-so-Great Firewall,” GreatFire.org, March 12, 2015, https://en.greatfire.org/blog/2015/mar/collateral-freedom-and-not-so-great-firewall.
33 Charlie, “We Are Under Attack,” GreatFire.org, March 19, 2015, https://en.greatfire.org/blog/2015/mar/we-are-under-attack.
34 For further discussion see Sarah McKune, “’Foreign Hostile Forces’: The Human Rights Dimension of China’s Cyber Campaigns,” in China and Cybersecurity: Espionage, Strategy, and Politics in the Digital Domain, ed. Jon R. Lindsay et al. [New York: Oxford University Press, 2015], 260-293. See also Wang Chen, “Concerning the Development and Administration of Our Country’s Internet,” translation by Human Rights in China, China Rights Forum: “China’s Internet”: Staking Digital Ground, no. 2 (2010), http://www.hrichina.org/en/content/3241, at para. III.6 (“We will perfect our system to monitor harmful information on the Internet, and strengthen the blocking of harmful information from outside China, to effectively prevent it from being disseminated in China through the Internet, and to withstand infiltration of the Internet by overseas hostile forces.”); Central Committee of the Communist Party of China’s General Office, “Communiqué on the Current State of the Ideological Sphere,” April 22, 2013, English translation by ChinaFile available at https://www.chinafile.com/document-9-chinafile-translation; Chris Buckley, “China’s New Leadership Takes Hard Line in Secret Memo,” New York Times, August 20, 2013, http://cn.nytimes.com/china/20130820/c20document/dual/.
35 Shuli Ren, “China Internet: Alibaba, Tencent, Baidu To Continue Buying Spree, R&D,” Barron’s Asia, January 7, 2015, http://blogs.barrons.com/asiastocks/2015/01/07/china-internet-alibaba-tencent-baidu-to-continue-buying-spree-rd/.
36 Alexa, “Top Sites in China,” http://www.alexa.com/topsites/countries/CN (accessed April 8, 2015).
37 Doug Young, “Investors Burn Out On Baidu Mobile Story,” Forbes Asia, February 12, 2015, http://www.forbes.com/sites/dougyoung/2015/02/12/investors-burn-out-on-baidu-mobile-story/.
==============
https://www.hackread.com/china-great-cannon-blocks-websites/

對中國阻止網站的大炮“一樣,沒有人能
中國使用更強的武器,以御史網絡,它被稱為偉大的大砲-它可以阻止網站和中斷的國際通信一樣,沒有其他人。最近,中國已經轟擊的美國網站與互聯網流量,力圖拿出可以讓中國的互聯網用戶查看網站這樣的服務已經被封鎖在中國 。
初步安全報告顯示,該服務已通過開發自己的互聯網過濾器調用的長城防火牆重定向互聯網流量的攻勢,以它的目標目的地被削弱了中國。
加州伯克利大學和加拿大多倫多大學的研究人員確定了長城防火牆還沒有使用過中國所有,而是他們已經打成大炮一個非常強大的新武器。

在發表這篇週五的報告顯示, 公民實驗室研究人員解釋說 ,偉大的大砲允許中國中斷的國際網絡流量,同時它通過中國的網站,它感染了惡意代碼,並重新調整,中國認為合適的流量。
這種方法被用來打斷廣告和網絡流量的百度,這是最大的搜索引擎公司,在中國,並在一個受歡迎的網站程序員GitHub上和運行的網站在中國被阻擋副本非營利性網站重定向所謂GreatFrire.org。
的攻擊,研究人員說,繼續在週四,但兩個網站一直運行正常。 他們建議,該系統可以配備更多的功能,因為只有一些調整的大炮可以對任何人誰不知何故設法獲取該公司正在舉辦由中國計算機中的內容進行監控。 即使當用戶訪問其中國營銷內容的非中國從事間諜活動的網站也可以啟動。
在他們的報告中,研究小組描述:“大炮的作戰部署代表的國家級信息控制,廣泛和公眾使用的攻擊工具正常化執行審查一個顯著的升級。”
該小組此前曾進行了廣泛的研究,由政府使用,並確定了,雖然攻擊的編碼和基礎設施是相同的長城防火牆,但攻擊已經啟動,從不同的設備從事間諜活動的工具。 該設備能夠攔截互聯網流量,也改變和調整它在更大的規模,幾乎所有的網站。 這種戰術被稱為“中間人攻擊”。
該報告還顯示,中國的最新武器是相同的已開發和使用的美國國家安全局(即一個NSA )和英國的GCHQ 。 該系統被暴露在由美國前情報承包商被洩露的機密文件愛德華·斯諾登J. 。 該文件透露 ,美國版本的系統可以部署的方案,能夠阻斷網絡流量在更大範圍內,以自己選擇的任何站點的機制。 該系統被用於進行有針對性的監控,而中國用大炮實施攻擊性審查。

但是,這兩個項目的性質相似,研究人員表示,可能會尷尬的美國官員。 他們寫道:“這一先例將很難讓西方政府令人信服地抱怨別人利用類似的技術,”根據紐約時報 。
但中國計劃顯示了其在北京的官員都願意加強互聯網審查制度的程度。 詹姆斯·A·劉易斯,該中心在華盛頓的安全專家戰略研究,指出“這是習近平的推動來獲得更嚴格的控制互聯網和刪除任何挑戰,黨的只是其中的一部分。”
中國不斷地一直在擴大其努力在其國家互聯網信息辦公室,這已被習近平成立以確保在中國境內的網絡控制和打壓網上維權行動促使審查的侵略性。
通過: 紐約時報
來源: 公民實驗室
-------------
中國的大炮
2015年4月10日分類: 比爾Marczak , 約翰·斯科特-萊爾頓 , 報告和簡報 這篇文章描述了我們中國的分析“大炮,”我們長期的攻擊工具,我們確定為單獨的,但同一地點有,中國的長城防火牆。 大炮的第一個已知的使用是在GitHub上兩者並用GreatFire.org服務器的最近一次大規模的小說DDoS攻擊。
作者:比爾Marczak 1,2,3(鉛),尼古拉斯·韋弗2,3(鉛)的Jakub的Dalek,1 Roya的Ensafi,4戴維·費菲爾德,2莎拉McKune,1阿恩雷伊,約翰·斯科特-萊爾頓,1羅納德·德貝特, 1韋恩帕克森2,3
所屬機構:(1)公民實驗室,全球事務的芒克學院,多倫多大學; (2)國際計算機科學研究所; (3)美國加州大學伯克利分校; (4)普林斯頓大學
第1部分:前言,主要調查結果
3月16日,GreatFire.org觀察到的服務器,他們已經租下,使中國的訪問封鎖的網站成為攻擊目標由分佈式拒絕服務(DDoS)攻擊。 3月26日,由GreatFire.org運行兩個GitHub的網頁也遭到同樣類型的攻擊。 這兩起襲擊出現針對設計來規避中國的審查服務。 通過GreatFire.org發布的報告手指惡意的Javascript通過百度的服務器作為攻擊源返回。 1百度否認他們的服務器被洩露。 2一些以前的技 術報告3表明,中國的長城防火牆被注入惡意的Javascript到百度連接策劃這些襲擊。 這篇文章描述了我們的進攻,我們能夠觀察,直到2015年4月8日的分析。
我們表明,雖然攻擊基礎設施共同位於長城防火牆, 該襲擊是由一個單獨的進攻體系,具有不同的功能和設計,我們稱之為“偉大的大砲。”大炮不是一個單純的擴展長城防火牆,而是一個獨特的攻擊工具,劫持流量(或可能來自)單個IP地址,並且可以隨意更換未加密的內容作為一個男人,在這方面的中間人 。
大炮的作戰部署表示顯著升級國家級信息控制:廣泛使用的攻擊工具,由用戶武器化實施審查制度的正常化。 具體而言,操縱大砲中國以外“旁觀者”系統的流量,默默編程他們的瀏覽器來創建一個大規模的DDoS攻擊。 而用於在這種情況下,一個非常明顯的攻擊,大炮顯然使用的方式類似美國國家安全局的量子系統,能力4 ,得到中國的機會,提供針對與任何中國的網站通信的任何外國的計算機漏洞沒有充分利用HTTPS。
報告結構
我們組織我們報告如下:第2節定位和特點的偉大的大砲作為一個單獨的系統;
第3節分析了DDoS攻擊日誌和特點受影響的系統的分佈;
第4節我們偉大的大砲到中國政府的歸屬;
第5節涉及的政策背景和意義;
第6節地址使用大炮為個人用戶有針對性的開發的可能性。
第2節:防火牆和大砲:獨立的系統,顯著的相似性
在一般情況下, 防火牆用作兩個網絡之間的路徑中障礙:在網絡之間的所有通信必須流經防火牆。 相反, 在路徑系統就像中國“防火長城”(GFW)坐在一旁:它竊聽中國和世界其他地區(TAP 圖1)之間的流量,並終止了禁止內容的請求(例如,在看見的請求“http://www.google.com/?falun”, 5無論實際目標服務器)通過注射一系列的偽造TCP重置(RST),告訴兩個請求者和目的地的數據包停止( 圖1中的進樣RST)的通信。 6 導通路徑的系統具有檢查建築的優點,但不太靈活,隱身比路徑系統作為攻擊工具,因為雖然它們可以注入額外的分組,它們不能防止IN-飛行數據包到達其目的地(即已經發送的數據包)。 7因此,人們通常可以識別一路徑系統的觀察,從兩個注入和合法流量的存在而產生的異常的存在。 8在GFW跟踪連接和重組的數據包(“TCP字節流重組”),以確定它是否應該阻止通信。 此重組過程需要附加的計算資源,而不是考慮隔離每個分組,但是允許更高的精度在阻斷。 而一個網頁請求常常適合單個分組內,捲筒紙答复可以被分割在多個數據包,並且GFW需要重新組裝這些包理解網頁答复是否包含禁止的內容。
在任何給定的物理鏈路(例如,光纖電纜),則GFW運行其重新組裝和檢查的邏輯在多個並行的進程9 (可能許多不同的計算機集群上運行)。 每個進程處理鏈路的連接的一個子集,以將相同的處理的連接上的所有數據包。 這種負載平衡架構體現在物理鏈路承載更多的流量比一台計算機可以跟踪一個共同的設計決策。 每個GFW過程也表現出非常獨特的側通道 -它保持的計數器,和數字它注入偽造TCP重置分組(經由IP TTL字段的值)。
偉大的大砲(GC)不同於GFW:我們將顯示,該GC是一個在路系統,不僅能注入流量,但也直接抑制流量,作為一個完整的“人在這方面的中間人”有針對性的流量。 在GC不主動檢查鏈路上的所有流量,但只攔截流量(或可能來自)一套有針對性的地址。 可以肯定的是,這減少了全業務流的只是一個(可能小)組地址與使系統顯著有助於跟上了非常高的交通量:GC的全處理管道只需要對多操作流量小的流,或從目標地址。 另外,與此相反的GFW,由GC僅在確定是否採取行動,從而避免TCP字節流重新組裝的計算成本檢查各個分組。 在GC還保持連接,它使用忽視最近連接它認為不再需要檢查流量緩存 。
在GC但是也可以共享一些功能與GFW。 像GFW的GC也是一個多進程集群,通過不同的工藝處理不同的源IP地址。 通過GC注入的分組也具有相同的特有的TTL副信道為那些由GFW注入,這表明,無論是GFW和GC可能具有一些共同的代碼。 兩者合計,這表明,雖然在GC和GFW是具有不同功能的獨立系統中,有在兩者之間顯著結構關係。
在GitHub上和GreatFire.org進攻,GC截獲的流量發送到主機常用的分析,社會,或廣告腳本百度基礎架構服務器。 如果GC看到某些JavaScript文件的要求在這些服務器之一,它出現概率採取兩種措施之一:它要么通過請求到百度的服務器上不受干擾(時間約98.25%),或前下降請求它達到百度,而是發送惡意腳本返回給發出請求的用戶(時間大致1.75%)。 在這種情況下,請求用戶是在中國境外個人瀏覽網站製作使用百度基礎架構服務器(例如,用廣告的網站通過百度的廣告網絡服務)。 該惡意腳本入伍請求用戶在對GreatFire.org和GitHub上的DDoS攻擊的不知情的參與者。
本地化炮
在GFW繼續運行正常:在路徑和有狀態
我們通過確認的GFW的審查功能持續正常運行開始了我們的調查。 我們也因此採用中國和百度的服務器,我們觀察到返回惡意的JavaScript之外我們的測試系統之間的測量。 我們發送的百度服務器的GFW會處理的查詢“http://www.google.com/?falun”的要求,久負盛名的URL 10觸發GFW注入偽造的TCP重置終止連接。 此數據包捕獲顯示了我們的實驗,證實GFW的正常,充分理解操作繼續的結果。 需要注意的是捕捉包括注入的TCP重置,以及後來從百度服務器的合法響應(一個HTTP 403回复)。 出現這種情況是因為GFW操作為接通路系統,並且,如前面所討論的,在路徑的系統不能防止在飛行數據包到達其目的地。本地化GFW
然後我們本地化其中(相對於我們的測量系統)在網絡拓撲中的GFW操作,如下所述。 對於給定的測量分組,我們可以控制它從我們的測量系統多遠到網絡轉變到它的目的地,通過控制分組的TTL值 。 經過多少個中間跳一個數據包將通過互聯網的內部路由器被丟棄的TTL值確定。 我們發送的“法輪功”的查詢,從我們的測試系統到百度服務器TTL值從1加重了。 我們觀察到GFW的TCP重置注射,只有當我們發送數據包的TTL值> = 18,這表明GFW作用於交通沿線,從我們的測試系統的路徑百度服務器的17和18跳之間流動(這本身發生24跳遠離我們的測試系統)。 此數據包捕獲顯示了我們的定位效果。 11由GC作為一個獨立的,在路徑系統
如前面所指出的,我們的GFW操作的痕跡顯示兩個注入TCP重置,以及合法服務器的答复。 相比之下,沒有合法的服務器響應陪同從GC注入惡意回复。 我們跑了進一步的測試,我們重新發送我們的要求,百度通過相同的連接,並使用相同的序列號,之後我們收到惡意響應。 我們觀察到百度響應為正常的重發的請求, 因此,我們的結論 12 ,該氣相色譜丟棄我們請求之前它到達百度,一個不存在於GFW能力。 13我們也檢查了GFW和GC是否會共享相同的注射裝置, 14但沒有發現任何證據,他們這樣做。 特別是,從一個給定的TCP源端口,我們發送一個請求旨在觸發GC注射,接著設計為觸發GFW注入的請求 。 我們反复實驗從數量的源端口。 同時通過兩個GFW和GC注入分組表現出類似的(特有)的TTL副信道指示在兩個系統之間共享的代碼,我們發現GFW和GC的TTL之間沒有明顯的相關性值本身。
由GC似乎協同定位與GFW
我們使用相同的TTL技術本地化GC我們的測試系統和百度服務器之間的路徑上。 我們發現,我們的道路,在GC作用於交通之間跳17跳18 , 我們觀察到作為負責的GFW相同的鏈接 。 我們也觀察到,不同的是GFW,我們可以用“裸體”的要求(即在孤立發送請求按要求標準通信,沒有以前的TCP SYN)觸發GC。 作用在“裸”請求意味著GC的含量分析是更原始(和易於操作),但是確實提供顯著的性能優勢,因為在GC不再需要維護有關連接狀態和TCP字節流重新組裝複雜的狀態。我們在中國的交通GC目標,以觀察是否GC存在隨著長城防火牆上的多個網絡路徑檢查兩個單獨的服務器。 從我們的測量中國以外的系統, 我們研究的路徑,既115.239.210.141和123.125.65.120 。 為115.239.210.141的GFW和GC既跳12和13之間存在144.232.12.211和202.97.33.37之間的聯繫,作為流量進入中國電信。 為123.125.65.120,在GFW和GC既跳17和18之間存在219.158.101.61和219.158.101.49之間的聯繫,屬於中國聯通。 由羅伯特·格雷厄姆先前的報告中使用的相同的TTL技術來斷定一個環節,GC位於“中國聯通的基礎設施中。” 15
只在特定的目標IP地址GC正在瞄準
當我們探討一個IP地址,毗鄰百度服務器 (123.125.65.121),氣相色譜完全忽略了請求,雖然GFW採取行動censorable請求到該主機。不像GFW,由GC僅作用於一個連接的第一個數據分組
對於給定的源IP地址和端口,由GC僅檢查確定是否注入的答复時發送的第一個數據分組。 為了避免檢查後續數據包需要記住哪個連接有否研究在流緩存 。 不像GFW,GC沒有重組的工作,一個顯著實施差別。另外,在GC將處理無效的HTTP請求,而GFW不會,還表示不同的實施方式。我們以證實這些行為發送的探測器到百度的服務器 ,要求觸發GC的注入資源。 每個探頭都有不同的源端口。 我們派出500探頭,每一個橫跨三個數據包(這樣的包1500個)的請求分割。 在GC忽略每個探頭。 我們再發送500的探針,其中第一分組的數據是無效的HTTP請求,而第二個數據包的數據是用於一個目標資源的完整,有效的請求。 在GC忽略每個探頭。 然後,我們發出了最後的500單包探頭,每個都包含了有針對性的資源一個完整的,有效的請求,確認正常GC操作。 正如所料,在GC注入惡意內容在某些情況下,似乎是根據它的概率的決策過程。
有多大GC流緩存?
我們試圖通過發送數據包到百度服務器不同的源IP地址和端口完全填滿GC流緩存,同時探測地看到,我們先前添加的條目是否現在過期。 我們嘗試表明,至少在某些情況 下,我們的測試系統和百度服務器之間的GC流緩存支持高達約16000項對於單個發送IP地址。不像GFW,在GC出現行動概率
檢查系統一般工作在一個確定的方式:他們的目標是阻止所有匹配目標的標準內容。 在GC,另一方面-至少對於這個特定的攻擊-出現行動概率,並忽略最它可以作用於流量。 在一個試驗中 ,它完全忽略所有業務從一個4測量的IP地址,並在其他三個測量IP地址,它只能從三(1.75%)回應526請求出的初始30000。緩存容量測試還提供證據表明,GC的概率選擇發生在作用於特定流的決定,而不是減少分析負載某種預過濾器。 當我們成功地完全填充所述流高速緩衝存儲器,隨後注入的分組發生了比在最初的測試不同的源端口。 如果GC只攔截流的一個子集到目標IP地址,我們希望隨後的注射,以顯示對於相同的流動,因為大多數計劃,以概率選擇流攔截(如散列連接4元組)將選擇相同的集流過的第二次左右。
請問GC有一個負載均衡的架構?
我們確定的GC使用為不同的源IP地址的單獨流高速緩衝存儲器,以及從不同的源IP地址的數據包注入具有不同的TTL側通道。 這一發現表明類似於GFW,在那裡分組被路由到基於源IP地址的GC節點的負載平衡的結構。 然後,我們發送交通交替從四個測量的IP地址 ,以試圖填補16000項緩存。 這種嘗試沒有設法填充緩存,這表明在GC不僅處理與不同的注射元件不同的源的IP地址,但是並使用不同的流緩存等等。 如前所述,四源IP地址中的一個從來沒有收到任何回复注入。第3節: 從對GreatFire攻擊分析的DDoS攻擊日誌中
GreatFire.org的工作人員提供了與作者服務器日誌佔地3月18日的期限至28。 16 (此前公佈的大火災的報告使用了不同的樣本。 17 )這一時期出現捕捉對GreatFire DDoS攻擊結束.ORG的服務,如通過服務器日誌文件在此期間的大小:為了使我們的分析易於處理,我們研究的數據的樣本,從3月18日11:00 GMT至3月19日格林尼治時間7:00,從兩個三個最常見的後端服務器所看到。 對於每一個時刻,我們選擇的壓縮日誌30MB每個服務器。 18 ,總樣本包括16611840 Web請求,以13183獨特的源IP地址。 我們使用的MaxMind GeoIP2精簡版數據庫19 ,從2015年3月3日到原籍國分配到每一個源IP地址。 對於那些沒有導致使用此工具(31地址)確定的地理定位的任何IP地址時,我們看到了地址手動使用iplocation.net服務。
下圖總結了原產地的頂級國家,與中國增加了比較。
需要注意的是IP地址的8827(66.9%),來自台灣和香港兩個地區,其中中國為官方語言起源。 然而,中國僅佔18請求。 這是在中國互聯網界注入中國主辦的網站惡意代碼一致。
以確定哪些網站有他們的反應由注射的惡意代碼改變,我們提取在我們的數據集中的25個最常見引薦的域名, 20發現這些結構域佔樣品中的總的要求的55%。
最常見的域名pos.baidu.com(樣品中請求總數37.7%),百度的廣告網絡的一部分。 許多非百度的網站上顯示廣告服務,通過百度的廣告網絡,這表明遊客對非百度的網站上顯示廣告也成為目標。 21
我們研究了前25名的域,並連接每一個到百度:在每種情況下,該網站要么是百度屬性或使用百度分析,廣告,或靜態資源。 22這一發現表明,百度是一個重大的注入目標的這種攻擊。 根據Alexa統計,百度本身是第四訪問量最大的網站在全球的排名最高的中國的網站在全球名單上, 23並已收到來自美國估計有499萬獨立訪客僅在過去的30天。 24
我們推測百度被選為注入目標,因為它是一種簡單的方法為目標的許多用戶。
第4節:歸因於大大砲向中國政府
我們相信,有令人信服的證據表明中國政府的運行GC。 在最近的公開聲明中,中國已經對偏轉無論是背後偷襲,而是強調中國往往是自身的網絡攻擊的受害者的問題。 25哪裡GC坐落?
我們測試了兩個國際互聯網的鏈接進入中國屬於兩個不同的中國互聯網服務供應商,並發現,在這兩種情況下,GC是同一地點的GFW。 在不同的互聯網服務供應商這種合作的位置極有可能是政府的演員。誰建的大炮?
該GFW和GC具有相同類型的TTL副信道的顯示,它們共享一些源代碼。 我們不知道任何公開的軟件庫的起草包,介紹這種類型的TTL側通道。什麼是偉大的大砲的功能?
我們的觀察表明,GC的設計不能反映技術非常適合於執行交通檢查。 其操作僅檢查給定的連接,它提供了比GFW一個審查機構弱的第一數據分組。 更一般地,GC的設計不,在實踐中,使之能夠屏蔽任何交通尚未censorable由GFW。 因此,有證據表明,GC的作用是在特定情況下有針對性的流量注入,沒有審查的流量。誰是大炮的攻擊?
通過使用“旁觀者”的機器的GC發起DDoS攻擊,直接對準了中國政府的政治已知的擔憂。 中國的網絡空間政府此前稱GreatFire為“國外反中國組織”(境外反華組), 26的特定GreatFire目標鎖定在這次攻擊中的服務提供代理繞過使用加密連接到亞馬遜的CloudFront的雲服務的GFW。GreatFire還舉辦2 GitHub的倉庫, https://gitub.com/greatfire和https://github.com/cn-nytimes ,提供技術,誰希望規避中國政府的審查用戶。 在GitHub上的攻擊專門針對這些存儲庫,可能是企圖迫使GitHub上刪除這些資源。 GitHub上使用加密TLS的所有流量,防止檢查員僅阻止訪問特定頁面的GitHub。 在過去,中國試圖阻止Github上,但塊兩天內,繼當地程序員顯著負面反應解除。 27
第5節:政策背景及啟示
本節介紹部署大炮的一些政策的影響,解決了針對百度的流量特別的影響,並討論可能涉及的GC運行的中國政府。在GC的中國政策含義
部署大炮是在戰術上的重大轉變,具有非常明顯的影響。 這可能是這次襲擊,其潛在的政治反彈, 28將需要高層當局中國政府內部的批准。 這些機構包括國家互聯網信息辦公室(SIIO), 29負責網絡審查。 這也有可能是機身頂部在中國,網絡安全和信息化網絡安全協調領導小組(CILG), 30就已經介入。 該CILG由習近平主持並包括來自全國各地的政府成員高層領導; 其辦事機構設在SIIO內。 31政府的理由在這裡部署的GC還不清楚,但它可能希望面對的“抵押品自由”戰略,通過先進GreatFire.org呈現給中國共產黨的(CPC)意識形態控制的威脅, 32等。 這次襲擊是極其昂貴的GreatFire,根據他們的公開聲明, 33以及破壞性的託管GreatFire內容的公司。 這種破壞可能是既企圖阻止不希望的資源的操作,並發送至潛在的價格標籤的其他組織這類活動的信號。 在GC的部署也可能反映了反擊一下中國政府察覺作為美國霸權在網絡空間的願望。
這種做法是與中國共產黨的至高無上的重點保護“國內穩定”(和自己的權力)對已確定為實體符合“境外敵對勢力”,不僅包括政府,而且西方媒體(如紐約時報 )和非政府組織或其他民間社會行動者(如GreatFire.org) 34根據這樣的世界觀,抵押品自由策略是威脅中國的安全構成挑釁,敵對行為。
使用流量為百度服務的影響
百度在這次攻擊中摻入表明,中國政府願意在其他目標,包括促進經濟增長,科技板塊為代價追求國內穩定和安全的目標。 選擇給百度對中國經濟的重要性,百度的國際運輸可能出現適得其反:公司享有的地位,作為中國的“三巨頭”的互聯網公司之一,沿著阿里巴巴和騰訊, 35 ,目前排名在中國頂級網站。 36雖然壓力之下其股價來到後,其第四季度和整個財年報告,2014年的2月發布37 ,2014年其總營收為USD $ 7.906十億,隨著網絡營銷營收為價值USD $ 7.816十億那個時期。 38“服務中斷可能會減少我們的收入和利潤,損害我們的品牌,如果我們的系統被認為是不可靠的。” 39百度的攻擊已經否認參與,並聲稱其內部的安全並沒有受到威脅。 40但國際遊客試圖進入網站是百度的屬性,或使用百度分析,廣告,或靜態資源的目標可能會破壞公司的聲譽和呼籲海外用戶和廣告商。
百度寫在它的SEC文件,這是在美國提起訴訟的目標在2011年41與中國的審查規定。 百度明確指出,中國的審查部門的合作與協調可能是昂貴的品牌形象,利潤和股東的信心方面。
“我們遵守中國法規的互聯網接入和新聞等信息發布在互聯網上可能會受到我們的負面宣傳,或在中國以外甚至訴訟。” 42此外,利用百度的國際影響力,作為數字進行攻擊的手段掩蓋政府最近承諾加強互聯網公司的全球業務。 在全國人大對2015年3月5日的會議上,總理李克強(誰也CILG副主席)宣布:
我們將制定的“互聯網加”行動計劃,整合移動互聯網,雲計算,大數據和物聯網與現代製造業互聯網,鼓勵電子商務,工業網絡,和網上銀行的健康發展,並引導基於互聯網的公司,以增加在國際市場上他們的存在 。 43這個目標-這緊密呼應包含中提出的宣言草案(但不通過)在2014年11月烏鎮世界互聯網大會44 -可能不來,如果中國國內的企業似乎不可靠,他們的業務目標繼發於中國的其他目標得以實現政府。
中國當局可能,但是,可以斷定,其使用百度的流量來安裝這個DDoS攻擊,最終被視為一個孤立的事件,一種“不可抗力”,與百度的長期經濟前景的影響有限 - 特別是考慮到百度的顯然地位不知情的受害者,其強大的市場地位。
此外,百度的CEO李彥宏是中國人民政治協商會議委員45並積極進行準備豐厚的政府合同前鋒-比如他的人工智能項目“中國腦”,為他尋求軍事支持46他可能很少有個人激勵(更不用說機會,因為適用於互聯網公司在中國現有的法律和監管框架47 )挑戰這一行動由政府。
思考當局誰可能是負責實施大炮
即使對於GFW,很難精確定位精確當局部署,或它的運營商和來源的後面。 這使得了解GC的起源同樣具有挑戰性。 然而,一些線索可供選擇。 例如,GFW和GC之間共享的源代碼和共同位置表明由GC可能已被同一機構框架與GFW內開發的。 因此,我們可以通過評估我們所了解的GFW得出進一步洞察GC。一些報告描述了GFW是中國的“金盾”工程,元素48下,公安部門的權威。 但是,未經證實的內幕信息“洩露”網上建議,GFW是在一個獨立的實體發展:“國家計算機網絡與信息安全管理中心”(國家計算機網絡與信息安全管理中心)(以下簡稱“中心”)。 49小是眾所周知的對中心。 看來要承擔的密切關係50對中國國家計算機網絡應急技術處理/協調中心(CNCERT / CC)由工業和信息化部(MIIT)運行-實際上, 上市地址CNCERT / CC是同樣,該中心作為其專利申請表明-與前國家網絡與信息安全協調小組, 51國家信息化領導小組在2014年CILG納入的小組委員會。 52值得注意的是,“工信部還規定中國六大互聯網服務提供商(ISP),從而有望根據國務院新聞辦公室和SIIO建立審查制度的指導方針,以監測和對他們的網絡內容過濾。“ 53這些互聯網服務供應商,包括中國電信,中國聯通,上的鏈接,其中我們共同位於GFW和GC(見上文)。
它是未知是否GFW和/或GC是實際上保持(或可能已經開發了全部或部分)由國家計算機網絡與信息安全管理中心。 然而,提起該實體的專利申請,合在一起,似乎表明大規模的網絡監控,過濾和防禦任務。 該中心已經申請了近100專利申請 , 54的設計,如“ 檢測意想不到的熱門話題中國微博的方法 “,” 方法和系統識別藏語方言 “;” 網站分類方法 “,” 方法和系統智能監控雲計算下分析 “;” 的方法和設備,用於管理大量結構化的記錄數據的全局索引 “;” 的方法,裝置和系統,用於交通監控和開關 ;“,” 圖像搜索/匹配的方法和系統對於相同的 ;“和” 因特 網基本信息管理系統 “(這最後一個”包括國家級管理子系統,省級管理子系統和企業管理子系統“,認為”可以對全國各地“互聯網基本信息有效的監督)。 此外,據官方媒體報導,在GFW的發展時,所謂的“長城防火牆之父”方濱興,受僱於在CNCERT / CC, 55的出現緊密聯繫在一起的中心實體。 56方舟子同樣列為2008年的專利申請由中心的發明者 ,說明之前的那點與中心的一些合作。
雖然我們不能確定的中心,專利文獻和中心所扮演的確切角色本身需要進一步的研究和分析,以確定它們是否相關的GC,或目前其他人權相關問題的操作。
第6節:結語:該功能由中國開發目標
我們的結論與有關的先例,中國在使用GC的設置一些言論,並提出有針對性的開發進一步的影響。由大炮發動了攻擊出現比較明顯和粗:拒絕服務攻擊的反感中國政府服務。 然而,攻擊本身就說明了一個更為顯著的能力:“以IP地址攻擊”的能力。 這種可能性,尚未觀察到,但它的體系結構的一個特點,代表一個有效的網絡攻擊的能力。
一個技術上簡單的變化,在大炮的配置,切換到操作上的流量從一個特定的IP地址,而不是一個特定的地址,將允許其運營商提供的惡意軟件有針對性的個人誰與任何中國服務器不使用加密保護的 GC 通訊運營商首先需要發現目標的IP地址,並確定合適的漏洞。 然後,操作員任務的GC攔截流量目標的IP地址,並更換帶有惡意內容的某些反應。 如果目標做過一個請求到服務器在中國境內沒有採用加密(例如,百度的廣告網絡),氣相色譜可以提供惡意負載的目標。 將目標未必意識到自己的電腦與中國的服務器進行通信,作為一個非中國的網站位於中國境外的可能(例如)提供廣告服務,最終來自中國的服務器採購。
由於GC作為一個完整的人在這方面的中間人,這也將是簡單的將它攔截未加密的電子郵件,或從目標IP地址和替換無法檢測到任何合法的附件帶有惡意的有效載荷,操縱從中國發往境外的電子郵件目的地。 即使電子郵件傳輸通過標準加密(STARTTLS)保護,可以削弱,因為GC是在一個位置,推出了“降級”的攻擊,轉向傳動只使用傳統的,未加密的通信。
我們在中國的調查結果增加一個記錄的情況下,以政府與未加密的互聯網流量篡改控制信息或發動襲擊的至少兩個其他已知的情況 - 在其他兩個分別是由美國國家安全局和英國GCHQ利用量子。 另外,從兩家公司,FinFisher和黑客團隊產品資料,表明他們賣的工具類似的“從網上攻擊”到世界各國政府。 57這些最新的研究結果強調取代傳統的網絡協議,如HTTP的緊迫性,他們的強加密版本,如HTTPS。
我們仍然困惑的是,為什麼GC的運營商選擇了首先使用它的能力在這樣一個公開可見的方式。 進行這樣的廣泛攻擊清楚地表明了中國互聯網的武器增選整個網絡和中國以外的任意計算機來實現中國的政策目的。 不知情的用戶在外國司法管轄區在一國的國家優先事項的利益隱蔽攻擊的設備的再利用是一個危險的先例 - 違背國際準則和違反國內普遍法律禁止擅自使用計算機和網絡系統。
致謝
特別感謝:亞當·森夫特(公民實驗室)和保羅·皮爾斯(加州大學伯克利分校,ICSI)。我們要感謝GreatFire為提供其日誌給我們進行分析。
我們也表示深深的感謝幾個人,匿名或假名在他們的要求,其中包括“傑克B,”誰資助我們理解攻擊在初期的元素,和其他人誰幫助我們制定和發展這一報告。
腳註
1使用百度百度引導數百萬台計算機來發動拒絕服務攻擊,“匿名作者,2015年3月25日( https://drive.google.com/file/d/0ByrxblDXR_yqeUNZYU5WcjFCbXM/view?pli=1 )2 http://www.theverge.com/2015/3/27/8299555/github-china-ddos-censorship-great-firewall
3 附錄C:相關技術報告
4 http://www.wired.com/2014/03/quantum/
5如下面進一步討論的,這種特定的URL一致觸發GFW應答,即使如果實際發送到www.google.com它簡單地返回谷歌主頁。
6見https://www.cs.unm.edu/~crandall/concept_doppler_ccs07.pdf為GFW的一般操作使用注射重置信息包的描述。
7雖然,在GFW不會發送RST數注入到兩個請求者和目標,這些可能的RST到達太晚抑制一些後續數據包的傳輸。
8參見http://www.icsi.berkeley.edu/pubs/networking/ndss09-resets.pdf對於如何檢測注入RST包的描述。 相同的技術適用於檢測注入數據包。
9對於在兩個平行的性質和存在於GFW中的TTL sidechannel信息,請參閱https://www.usenix.org/system/files/conference/foci14/foci14-anonymous.pdf
10 https://www.cs.unm.edu/~crandall/concept_doppler_ccs07.pdf
11包捕獲也印證了GFW的內容分析的狀態性質:除非它先觀察一個TCP SYN和ACK的SYN / ACK的連接不注入一個TCP重置。
12如果GC沒降發送到百度的請求,那麼百度就會收到我們的第一個請求(其中GC響應),並且會忽略我們隨後,重複的要求,如由TCP協議。 我們證實,當GC沒有注入回應,百度確實忽略重複的請求。
13技術上複雜的情況存在於其中的路徑系統像GFW可以想像防止響應來自百度的外觀通過破壞會話啟動。 我們進行了廣泛的測試評估這種可能性。 我們省略了這些結果從這份報告,因為上面所討論的明確“轉播”測量排除了這種可能性,使測量結果毫無意義。
14類似的系統,以在GC,如量子,使具有噴射器作為從系統的其餘部分不同的裝置的架構的決定。
15 http://blog.erratasec.com/2015/04/pin-pointing-chinas-attack-against.html
16 1.1TB壓縮。 需要注意的是日誌包括惡意和非惡意流量
17 https://drive.google.com/file/d/0ByrxblDXR_yqeUNZYU5WcjFCbXM/view?pli=1
18文件隨機選擇之中即分別鄰近30MB的文件的列表。 該尺寸被選中是因為它是存在於我們針對所有時間戳小時最大文件大小。
19 http://dev.maxmind.com/geoip/legacy/geolite/
20注意,正在被使用Javascript生成的惡意請求。 當腳本發出網絡請求,在Web瀏覽器上設置的請求裝載的腳本的網頁的URL的“Referer的 ”報頭。
21是典型的用於網絡的廣告被顯示在 iframe中。 這會導致“Referer的”頭匯報廣告服務,而不是託管頁面。
22見附錄A.
23 Alexa的,“前500個網站的網頁,在” http://www.alexa.com/topsites (訪問2015年4月8日)。
24 Alexa的,“網站概述:baidu.com,” http://www.alexa.com/siteinfo/baidu.com (訪問2015年4月8日)。
======================
 https://www.hackread.com/china-blocks-reuters-website-after-ddos-attack-on-the-great-firewall-of-china/
https://www.hackread.com/china-blocks-reuters-website-after-ddos-attack-on-the-great-firewall-of-china/China Blocks Reuters Website After DDoS Attack On The Great Firewall of China
The Great Firewall of China known for censoring/blocking websites in the country was under DDoS attack which caused a blockage of Reuters’ news website in China on Friday.The content of the website was blocked and could not be accessed later on Thursday. Both the English and Chinese version were inaccessible but the Chinese clients could still see financial news and data feeds as reported by the news item by the blockage.
Websites such as Bloomberg, The New York Times and The Wall Street journal are blocked by the Great Firewall and hence an average Chinese user cannot see them online.
“Reuters is committed to practicing fair and accurate journalism worldwide. We recognize the great importance of news about China to all our customers, and we hope that our sites will be restored in China soon,” according to the news agency.
MUST READ: China’ censorship system upgrade blocks VPN services, causes weird traffic spikes
An Internet user, preferred to be called by the name Xiao Biao usually evades the censorship of the Chinese web in order to browse overseas sites said that he was not able to load the new Reuters site along with a couple of other media websites on Friday.
The greatest fear of the Chinese Communist Party is the consequences that will occur if the people all over the country access a number of different opinions.
The user told that page keeps on refreshing but does not load thus preventing any information to be seen on the Chinese version of the Reuters news website.
MUST READ: List of Eight Popular websites That are Banned in China
Although he mentioned that he was able to load the Wall Street Journal Chinese-language website.
Threatened by media reports
The government is afraid if the any of the media reports gets out of the control of the state, says Xiao Biao.He also said that the government in pursuit of ruling over attempted to shut off various voices thus keeping the population of the country ignorant of the news and opinions held outside of China.
Shi, a Shanghai-based netizen said she was forced to give up on accessing international news websites. She gave an example by saying that whenever she tries to open up the CNN website, the page takes hours to loose causing me to lose my patience.
Also, she told that the videos on CNN keep buffering most of the time and so she has given up visiting the website.
A Guangdong-based netizen Jia Pin told that if Chinese users want to have access to overseas news websites, they should set up circumvention tools on their computers. He said the users must go over the Great Firewall in order to view these kinds of websites.
Denial-of-service attack
The Reuters’ sites were blocked a day after GreatFire.org – an anti-censorship website that is based overseas – announce that it has been attacked severely by a distributed denial-of-service attack.On Thursday, the group said on a blog that to perform such an attack, the website has to be flooded with a huge number of requests which causes web pages to crash.
It also said that the attack is brutal and shows censorship by harsh force. Also, the attack caused its bills to be sent with the service provider Amazon that summed up to about $30,000 per day.
The attack was made on March 17 right after the Chinese government showed their irritation over what the group was doing and labelled the site as an “anti-China website set up by an overseas anti-China organization.”
It said that website has allowed the Chinese users to access many blocked websites by using a mirror-website technique.
Hu Jia, a Beijing-based right activist who also uses circumvention techniques said that the user find a way to evade the Great Firewall faster than the government comes up with more ways on blocking the websites.
Hu said that the bad guys get an upgrade and then the good follow suit thus causing a process of pursuit like a cat chasing a mouse.
He said it is not known as to what techniques have been used to make the Reuters site inaccessible.
Hu said that the blockage is perhaps a reaction to what the site was reporting. He added that it does not imply that the Great Firewall has been upgraded or that other circumvention techniques will not able to overcome the blockade.
Accusations of cyberattacks
Frequently, USA and China have traded allegations of cyberattacks. Particularly, China denies the claim placed by USA over the People’s Liberation Army (PLA) cyberspace unit in Shanghai for causing a series of cyber-attacks on the U.S corporate networks in the past few years.Also, on Friday, China’s defense ministry refuted the allegations placed against them in London’s Financial Times for attacking Register.com through a confidential unit of PLA, 61398.
The ministry faxed to Reuters saying that the criticism over China’s military that it is involved in hacking the internet has no ground and evidence.
The ministry also said that China has stood strong against such allegations and has been dealing with such matters according to the Internet hacking law along with other criminal activities. Moreover, the Chinese military has never indulged itself in any activity that is aimed at stealing commercial secrets on the web.
MUST READ: China admits cyber warfare unit in People’s Liberation Army
On the other hand, official media reported that in 2014 alone, China recorded around 4761 IP addresses based in the United States that were involved in taking control of 5580 Chinese-based computers through background programs causing these computers to be controlled with remote access.
The U.S was called upon by the defense ministry of China to give a fair explanation of these findings.
---------
============
https://www.hackread.com/china-blocks-reuters-website-after-ddos-attack-on-the-great-firewall-of-china/
中國塊路透社網站的DDoS攻擊中國的長城防火牆後
在 中國防火長城聞名審查/阻止網站在該國下DDoS攻擊造成的路透社新聞網站堵塞在中國上週五。該網站內容被封鎖,不能在週四稍後訪問。 無論是英語和中國版是人跡罕至,但中國的客戶仍然可以看到所報告的堵塞新聞項目的金融新聞和數據源。
網站,如彭博,紐約時報和華爾街日報是由長城防火牆封鎖,因此,平均中國的用戶不能看到它們在網上。

“路透致力於為全球執業公正,準確的新聞。 我們認識到,新聞對中國的重視,我們所有的客戶,我們希望我們的網站將根據新聞機構恢復在中國很快“。
必讀: 中國的審查制度升級塊VPN服務,使怪異的流量峰值
互聯網用戶,首選的名稱肖彪被稱為通常迴避了中國網絡的審查,以瀏覽國外網站說,他無法與上週五幾個其他媒體網站加載新路透社網站。
中國共產黨的最大的恐懼是會發生,如果人們在全國各地訪問了許多不同意見的後果。
用戶告訴該網頁上保持清爽,但並不因此加載防止被視為對中國版的路透社新聞網站的任何信息。
必讀: 八那被禁止在中國最受歡迎的網站名單
雖然他提到,他能夠加載華爾街日報中國語言的網站。
通過媒體的報導受到威脅
政府擔心,如果任何的媒體報導失控狀態的控制,說肖彪。他還表示,政府在追求統治著試圖關閉多種聲音,從而保持國家一無所知中國以外舉行的新聞和觀點的人口。
市,一個上海的網友說,她被迫放棄了對進入國際新聞網站。 她說,每當她試圖打開CNN網站時,頁面需要時間寬鬆使我失去了我的耐心舉了一個例子。
此外,她告訴CNN上的視頻保持緩衝的大部分時間,因此她已經放棄訪問該網站。
廣東某網友賈披嗯告知,如果中國用戶希望獲得海外新聞網站,他們應該設立規避工具,在他們的計算機。 他說,用戶必須越過長城防火牆,以查看這些類型的網站。
分佈式阻斷服務攻擊
反審查網站,是基於海外- -宣布,它已被嚴重攻擊拒絕服務的分佈式攻擊路透社網站GreatFire.org一天後受阻。上週四,該集團在博客上,要執行這樣的攻擊說,該網站有一個巨大的請求數,導致網頁崩潰被淹沒。
它還說,這次襲擊是殘酷和苛刻的武力展示審查。 此外,攻擊造成其票據與服務提供商亞馬遜是總結至約30,000元每天發送。
這次襲擊被做3月17日之後,中國政府表現出他們的刺激過什麼組在做,並標註該網站作為一個“反中國網站成立了由海外反中國的組織。”
它說,該網站已經允許中國用戶使用鏡面技術的網站訪問很多封鎖的網站。
胡佳北京的權活動家誰也使用規避技術表示,用戶找到一個方法來逃避長城防火牆的速度比政府又發表了關於阻止網站更多的途徑。
胡錦濤說,壞人得到了升級,然後好跟風從而導致追求的過程像貓追老鼠。
他說,目前還不知道是什麼技術已被用來製造路透社網站無法訪問。
胡錦濤說,堵塞可能是一個反應是什麼網站報告。 他補充說,這並不意味著長城防火牆已經升級或其他規避技術將無法克服的封鎖。
網絡攻擊的指責
通常情況下,美國和中國已經上市的指控網絡攻擊。 尤其是,中國否認在上海放置USA在人民解放軍(PLA)網絡空間單元引起一系列對美國企業網絡的網絡攻擊,在過去幾年索賠。此外,上週五,中國國防部駁斥放在對他們在倫敦的金融時報,通過PLA,61398的保密單位攻擊Register.com的指控。
該部傳真給路透社說,批評對中國軍事,這是參與黑客攻擊互聯網已經沒有理由和證據。
該部還表示,中國已經站在強對這樣的指控,並一直在處理根據與其他犯罪活動的互聯網黑客的法律事項等。 此外,中國軍方從來沒有縱容自己在這的目的是在網絡上竊取商業機密的任何活動。
必讀: 中國承認在解放軍網絡戰部隊
在另一方面,官方媒體報導稱,僅在2014年,中國錄參與了通過後台程序走的5580中國為基礎的計算機控制造成這些計算機與遠程訪問進行控制,基於在美國各地的4761 IP地址。
美國正在呼籲由中國國防部給予這些研究結果公正的解釋。
=============##############
http://hk.apple.nextmedia.com/realtime/news/20150410/53621911
Cen Ao Hui Huang Feng, 20 or charged  with criminal contempt of court
with criminal contempt of court
Attorney General to apply to the court, asking the court to approve Cen Ao Hui (left) and Huang Feng (right) accused of criminal contempt of court, expand the committal process. (Picture).
[Update: Huang Feng, the Department of Justice to respond]
Ao Hui, deputy secretary general of the Federation Cen, Scholarism convener Huang Feng, and many others, in the Mong Kok occupied cleared by the end of November last year, accused of interfering or obstructing bailiffs and police enforce court issued a temporary restraining order, arrested for criminal contempt of court . Refers to the High Court of Justice earlier this month, has an application to the court at the time of approval of the 20 accounted for a busy area cleared of demonstrators were arrested, a criminal contempt of court proceedings.
Cen Ao Feng Huang Hui and refer to a letter received by the Department of Justice, Huang Feng on facebook mean, from beginning to end do not think they have a criminal contempt of court matter, "in Mong Kok did not clear the scene and the Department of Justice on behalf of the day (ie bailiffs) have any limbs contact "a few months now delaying political prosecution, only" from the security of both. "
(Cen Ao Fai facebook pictures).
Cen facebook Ao Hui also said that the Department of Justice is expected to approve the court is bound to apply, "to come, and always want to come, in fact, it has come late than I imagined." He said that since the decision to participate in civil disobedience, are psychologically prepared to face political prosecution, conviction or imprisonment ultimately means avoid crying and felt no need to worry about the outside world, "I would be comfortable with."
Cen Ao Hui said, a variety of disobedience action in the past year, although not enough to force the regime concessions, but is considered to have been a turning point on, he struggles to Taiwan over the years, for example, called on Hong Kong people should not be discouraged, "To achieve true" independent destiny. " indeed to be more flexible, intelligent and initiated the protests, the cumulative strength. "
Cen Ao Hui, Huang Feng and Zhou Yongkang, Secretary-General of the Federation and others, received an appointment earlier arrested by the police means involving three charges, including inciting others to participate in unauthorized assembly, convened and organized unauthorized assembly and participation in unauthorized assembly subsequently released unconditionally.
=====================
*Note This Sharing By Anonymous~
Operation China: 161 domains of China Hacked http://pastebin.com/nqy1iGYJ We are here and we will stay! You should have expected for us. #AntiSec
Fuck the lammer's ( DeathKillers HackerTeam ) you is a noob ...
soon we will repeat attacks Chinese websites

___ _ _ ____ _ _
| _ \ _ __ ___ _ __ __ _| |_(_) ___ _ __ | ___| |__ (_)_ __ __ _
| | | | '_ \ | _ \ '__| _` | __| || _ \| '_ \ | | | '_ \| | '_ \ | _` |
| |_| | |_) | __| | | (_| | |_| | (_) | | | | | |___| | | | | | | | (_| |
\___|| .__| \___|_| \__,_|\__|_|\___||_| |_| \____|_| |_|_|_| |_|\__,_|
|_|
https://twitter.com/h4x0s
4539575804855859|8|2019|788 4485143782953230|2|2018|765 5408685253240597|10|2017|132 4485611219011129|9|2016|305 5187441679591347|4|2018|545 4929576665455837|2|2016|702 5506345844939196|10|2020|964 5437614409762218|5|2019|278 4485592348193063|7|2019|706 5193439054634536|10|2020|317 4539610021988140|7|2017|741 5197043901608515|9|2016|883 5135229627701487|1|2017|802 5272375853058978|9|2016|521 5115342339940436|1|2019|797 5550559624663470|9|2020|274 4485567843642186|2|2020|124 5427021353493158|4|2016|903 5516371823474532|9|2018|847 4556419334421411|3|2017|615 4539658624165327|12|2018|458 5150530507591199|6|2019|634 5514749296432552|9|2016|772 5149187209270145|3|2017|250 5103556440645220|8|2018|473 4716030497145148|6|2019|002 4532113841735533|1|2020|471 4556550928427214|5|2020|866 4532065905051746|7|2020|214 4716167980426476|10|2017|273 5415096981615202|10|2017|909 4916499829960839|7|2016|034 4929292212920352|1|2020|593 5125971400567591|6|2020|295 5427034930463727|7|2019|810 5116646411426141|9|2020|422 4485412344953636|1|2020|743 4532083212230580|4|2019|055 4916944742213865|10|2018|983 5478192216853801|8|2017|908 5414567812863253|10|2020|015 4485782829339018|10|2016|699 4532324454647911|12|2019|422 4485201731119723|5|2019|017 4532860330367034|1|2019|965 5458349430544103|3|2017|499 4485144753090119|6|2017|833 5471269471211292|12|2020|486 5318995155067447|7|2019|830 5425737056550471|3|2020|598 5439794269533251|4|2019|656 5222595031820129|8|2017|255 5503341606085438|6|2019|150 4485724430472416|11|2019|753 5536527833424009|12|2018|971 4916721932971019|1|2016|897 5515204654111520|8|2018|273 5274830072430257|10|2020|375 4532046859193189|2|2018|170 5201661679069778|1|2016|067 5110869950345995|2|2016|829 4539247744831982|10|2020|043 4916225512906387|1|2017|922 5510609540270592|1|2018|263 5478048358712538|3|2017|995 4485334863264759|11|2017|877 5412033678060163|5|2016|173 4556633148137720|3|2018|490 4716244450559365|10|2016|608 5486673586723591|9|2018|189 5355238526765405|8|2020|831 4539521266588422|5|2017|667 4716408927803835|1|2016|640 5477971453279452|12|2017|627 4539496111661783|8|2017|075 4929625045525064|5|2017|964 4556551436675302|2|2016|485 5193736680440430|2|2017|998 4532858888165339|1|2018|667 5263118731044997|3|2017|881 5295537004735845|10|2017|022 4532293100735455|7|2019|325 4556420496635848|10|2018|863 5453282037851032|4|2019|117 4929942232626633|12|2016|761 4539963583747788|2|2020|198 4716058199786497|2|2016|856 4716116138087284|11|2016|787 4716394862287939|4|2019|273 4716162784124609|12|2016|557 5323592921866658|3|2020|952 5386092285450052|3|2016|196 4929484824929364|11|2018|690 4556913281130876|7|2020|966 5175128653491529|7|2020|580 4916754024836089|6|2018|580 4916623584982932|9|2020|261 4716140740947073|3|2019|876 5139948521380983|4|2016|655 4539786484641432|4|2020|124 5392072960159014|2|2020|809 4916392185218761|1|2020|626 4716689885351665|4|2017|647 5428388584597803|4|2020|225 5393539083747700|7|2016|672 4532382935771569|9|2016|405 4556167451737768|1|2017|993 5179283986323471|7|2017|685 5563522406502386|10|2017|921 4539003810544037|12|2020|177 5287230181600731|2|2017|015 4485176946168063|5|2016|810 4532136496928590|4|2016|332 4532638518958620|5|2018|951 4485739560464819|8|2017|780 4556414443764777|9|2019|024 4916482713593361|7|2020|456 4485494400672797|1|2018|695 4929645424615641|1|2020|269 5325786500715660|12|2018|100 4485653536290945|2|2016|282 5269725283721501|4|2016|147 4485131575011175|11|2019|838 4539267905150600|5|2016|868 4532549489937487|8|2016|298 5521922467601617|9|2017|788 4556093556168701|7|2020|055 5597356478592334|3|2016|291 5416727606945454|11|2017|639 5230247198722231|8|2016|508 4716681608145102|2|2016|101 4716572540652026|4|2020|866 5506117247832314|3|2019|125 5219757626822473|11|2020|265 4539115192475406|10|2019|089 5539372905758316|6|2019|407 4929890225413370|11|2017|072 4916374945717142|1|2016|116 4916880979832359|8|2017|737 5515507188350467|9|2016|870 5198915352820245|7|2016|842 4556506715356917|3|2017|652 5561187941575594|8|2020|450 5381586284922271|1|2020|165 5143323397587943|9|2019|513 5227318137652212|2|2017|534 5376492414862197|12|2017|090 5446778913083582|12|2017|149 4539388679517244|2|2018|159 4532060931398021|12|2018|371 5555148833840213|12|2016|406 5479078164180926|1|2016|394 5238814169292098|5|2017|770 5487670624838091|3|2019|407 5334645779317609|1|2019|522 5595819507411422|7|2016|755 5418276331874207|11|2017|831 5124914391547108|10|2017|657 4556928735089783|9|2019|218 4532639567051614|4|2018|524 4916430285989970|10|2018|786 5272556757635975|9|2019|377 4716613059739539|3|2017|692 4539201521343760|11|2016|779 5588856910781271|11|2019|122 4716595316046891|2|2018|216 4916711451838285|8|2020|920 5410442502995563|7|2016|247 5362071169824911|5|2020|001 4916150131903542|7|2020|270 4532525876414181|8|2018|839 5494874924891542|12|2018|273 5227300932961550|8|2019|434 5500362558087134|10|2020|154 5379664917498995|5|2019|568 4539900846547258|7|2016|870 5177920958013521|7|2018|977 5225836840589811|1|2016|612 4539174418463084|4|2016|334 4539826708345020|4|2016|902 4539638369905459|7|2018|398 5131917666118019|12|2020|601 4556234872687566|3|2019|901 5211278254957042|10|2018|465 5153800427507873|3|2017|661 4716920393752965|7|2020|357 5109020905978646|7|2016|578 4556204358034187|11|2020|184 5370750737194598|6|2016|184 4532582252036591|5|2020|247 5464285977706535|3|2019|515 4485102753174598|6|2018|195 5126500007491787|6|2019|473 5197652319056131|2|2019|132 4485045702258733|12|2018|190 4485804299031741|7|2019|052 5164943571518168|6|2018|704 4539345481416601|5|2019|467 4916069315910117|2|2018|139 4485987741689776|10|2017|122 5405636130175293|7|2020|546 4485138822720284|9|2019|202 4556732623958467|7|2018|904 5220694633575686|3|2016|341 4485047255924828|3|2016|113 5409319700139405|9|2019|644 4532252199953833|6|2017|318 4539533162733598|4|2019|022 4539745835173644|1|2020|408 4916017337941867|9|2020|463 5171272802479656|4|2018|995 5391576132951901|7|2016|913 4716352809464276|3|2016|961 4929857887190091|8|2017|845 5316337617139112|10|2016|668 4532713085817416|11|2018|572 5121306229607662|1|2019|931 4716649944381863|11|2018|045 5590618599219213|4|2020|440 5194385998555718|4|2017|045 4916163680916336|11|2017|427 5280107758949708|12|2020|993 4539581144300192|10|2016|104 5533300839751095|12|2016|304 5461358921068402|9|2016|939 5327942628902668|11|2016|562 4929650899509535|9|2020|435 5598103839427266|5|2017|008 5522033855391958|4|2016|906 5402533964290095|10|2019|326 5296766066546290|12|2016|876 5408647010007016|9|2020|360 5542670100591654|12|2019|231 4556981617203147|11|2017|721 5280723862127385|11|2017|889 4716727138994863|3|2018|793 5531605381397002|6|2016|920 5189670822866234|2|2017|417 4539012401374936|3|2016|782 5599640616988605|8|2019|242 5147835027451923|7|2016|811 5417898601686259|10|2019|109 4716686778327430|11|2016|121 4532315740734836|2|2018|589 4916218612339948|5|2016|247 4539754634138030|2|2018|373 5549900925068395|10|2016|748 5494206766230002|8|2019|057 5171414445525566|1|2019|538 4539776112009011|7|2020|813 4539261382122711|7|2020|135 4485120892951817|2|2018|811 4532616298126162|7|2019|428 5194299315689896|11|2018|209 5429987231690686|2|2020|035 5246483272932188|10|2016|791 4916961920252945|11|2019|271 5263204415029759|5|2019|574 4929722269228820|7|2017|154 4929872483883312|1|2018|256 5184747185410340|9|2017|880 4716761011245135|8|2018|161 5411470248363019|11|2017|610 4539183831667338|5|2020|802 5393791579224815|12|2020|707 5166230658947199|1|2018|839 5448715800612105|9|2018|953 5395230397278883|8|2019|019 5104130047963631|8|2020|483 5542118779734882|11|2019|342 4556353587355200|12|2020|811 4916265181865092|5|2020|520 5579124959038744|9|2017|942 5364406970975726|10|2016|255 5219671575040468|1|2017|733 5178902036137240|6|2017|222 5320205805866495|9|2019|306 5169136552457390|9|2017|425 4532498569843613|2|2016|115 4916838968639706|9|2020|747 4539972095139566|3|2019|200 5226317666082263|5|2017|116 4929923141326895|1|2018|432 5269518714604614|10|2017|510 5594745577512917|7|2016|065 5327552526739532|1|2019|214 4716369451650473|5|2019|038 5216159351337004|5|2020|110 5536456731996159|6|2020|206 5163897153200192|12|2016|102 4916532896618243|10|2018|084 4929620265251400|7|2017|179 5501159349752623|7|2020|860 4539073423598597|11|2019|712 5234821998041749|10|2017|110 4929403963242983|9|2019|557 5390671926133120|1|2020|652 5493606382075262|9|2017|299 5423718753813042|8|2018|579 4532260772196886|6|2018|092 4716589169373619|6|2019|167 4929299999905993|2|2017|016 5520924408596469|6|2020|726 4916823515044105|10|2019|503 5478923761310734|3|2019|935 4929397382948693|3|2016|963 5595764365750877|6|2019|049 5233378667454894|10|2017|203 5475715832863227|1|2018|041 5360630044285184|7|2020|331 4929333433475501|4|2016|022 4532498217524979|12|2016|060 4556650104342821|6|2016|935 5420196439898617|10|2020|838 5318250055845686|9|2017|037 4539671591853304|3|2016|180 4556552646829077|2|2020|459 4929889251481665|9|2019|083 4556380216034054|9|2019|116 5328114632592344|9|2019|141 4485099530190238|5|2016|886 4485750681066623|2|2017|066 4485928281908838|2|2020|942 5388813441334189|3|2016|392 4532707490269205|4|2019|375 4556958057388125|3|2016|155 4556178441636309|4|2017|786 5590642513828610|2|2018|981 5109568744248837|11|2016|210 4485516133403312|6|2017|547 4916424429671099|5|2019|732 5494991422714651|5|2016|862 5363129955150450|9|2018|848 4556718354212133|11|2020|418 4532162922402513|1|2017|312 5570227133461341|5|2019|835 5548808077850802|11|2020|049 5114675152457561|4|2019|719 4539747373425832|10|2020|995 5326861700291009|2|2016|390 4485403269904001|10|2017|570 5264602174596794|11|2020|481 4556078430824736|5|2018|759 5181782751135826|9|2016|207 4532104056689374|9|2019|281 5543705897440886|3|2018|765 4485609796328205|3|2020|567 5144422696777889|1|2017|252 5418188905672661|1|2019|575 5101312875926517|2|2019|739 4532019887914553|10|2017|604 4485322731071829|10|2018|144 5192323114943155|4|2020|132 5105422882731614|4|2017|868 5303073248407421|12|2017|278 5511959242213773|6|2016|240 4916064790067954|11|2018|094 5388193807771898|5|2019|210 4929603912866887|10|2019|793 4716190015468347|10|2020|460 4532100850712073|6|2016|187 4532103274082693|11|2018|143 4532203662802403|3|2020|369 4556981569792824|8|2017|670 5422213731666622|10|2019|519 4929519991588442|3|2017|037 5557430127547920|11|2018|830 4556174490389692|4|2016|666 5224061393437091|8|2016|632 5488032140937395|3|2018|939 4539397633248580|6|2018|371 4556238647495312|1|2020|026 4556803596292752|6|2016|532 4916999389493717|7|2016|105 5326481049655457|9|2019|276 4532925495988955|8|2019|087 5452084751875838|9|2019|009 4539068989799068|11|2018|404 4532306340825645|8|2019|143 5202870852394437|11|2016|651 5597969408884934|8|2018|387 5395324690123589|10|2017|433 5199981548943316|3|2019|151 5360597238621187|10|2017|059 5520080572094318|10|2016|935 5559971804793830|9|2018|912 4532421034143674|9|2017|357 4556015261403503|4|2019|108 4556586619101759|10|2020|023 5299590423062479|12|2016|116 4485120727826101|7|2016|031 5122345894125542|10|2017|421 4916855153829405|1|2017|924 5576078498660413|8|2017|992 5422693596525627|11|2018|294 5224677721579054|3|2018|846 4916910485771963|4|2020|915 4716354845801974|1|2018|183 5277911006202074|7|2016|280 4916811893268891|10|2019|699 4556314551754232|1|2020|913 5415395819558810|1|2020|527 4539495394473312|8|2019|323 5348401531483683|12|2016|070 4539363704369838|2|2020|687 5518736106381935|3|2019|409 4929115291256440|3|2019|921 4539752156969550|7|2016|924 4929065382093972|2|2016|366 4532210780031773|8|2016|041 5146265632191311|10|2018|964 4539055049294610|12|2016|522 4532491083741322|3|2016|561 4916434209251061|10|2017|674 4716807208037312|6|2016|217 4929774501855027|5|2020|250 5142914558440608|1|2020|958 5261841943558445|9|2017|406 4716553660350344|2|2020|501 5150334993823970|7|2018|850 4916991365069496|12|2016|338 4556328593133619|6|2018|486 5334674502292657|9|2017|952 5357264937983930|7|2016|669 5251335385734327|11|2020|478 4532930158638202|8|2018|897 5513563017009198|9|2020|307 5388080662070724|3|2016|523 5259609525585290|12|2019|536 4485902962299833|3|2016|916 4485434533911555|11|2018|320 4539490547300546|11|2020|048 4916635566874879|2|2018|323 5114407084701829|6|2018|124 4929615944398515|11|2016|173 4532182214311065|12|2019|446 4539032008765161|8|2019|253 4539493994145802|10|2020|384 5333420801960367|12|2019|974 5533640354455253|9|2017|951 4485605873881223|10|2017|745 4556909789061704|8|2016|697 4556829591093861|10|2018|062 5544715475891482|4|2019|387 4556495218015834|12|2019|856 5343285502486212|10|2018|431 5230091553656786|3|2019|491 4485713894356322|9|2016|094 4532514853101524|9|2019|184 4539304491797419|1|2020|419 4539610931653057|6|2018|656
very thanks~ power!!
==========================
#OpChina
 Namaste
Namaste

 Anonymous
Anonymous
___ _ _ ____ _ _
| _ \ _ __ ___ _ __ __ _| |_(_) ___ _ __ | ___| |__ (_)_ __ __ _
| | | | '_ \ | _ \ '__| _` | __| || _ \| '_ \ | | | '_ \| | '_ \ | _` |
| |_| | |_) | __| | | (_| | |_| | (_) | | | | | |___| | | | | | | | (_| |
\___|| .__| \___|_| \__,_|\__|_|\___||_| |_| \____|_| |_|_|_| |_|\__,_|
|_|
https://twitter.com/AnonymousGlobo
https://twitter.com/h4x0s
4929773699206423|1|2018|935
4485041577048093|8|2020|671
4716870829646481|9|2017|958
5187824835991479|1|2018|084
5357308140404125|4|2020|366
5536162068122134|1|2019|295
5501933374628332|1|2020|571
4532340587058933|8|2017|371
4485832955337151|10|2019|629
5597377569104755|3|2017|897
4916801150615603|7|2017|245
4716437219377398|10|2020|166
5435433642735473|4|2019|568
5591140166713709|7|2020|839
5463742099997179|7|2019|211
5305070417614215|6|2018|854
5244822844297681|3|2016|994
5283939000677456|3|2018|420
4532595500726136|9|2020|590
5277237799831618|8|2020|100
5364467155247653|9|2017|505
4485278974722132|12|2020|206
4916372407716206|8|2018|271
5378611326016331|2|2019|217
4916669993623302|12|2019|396
4485458598747596|12|2017|765
5176189692598806|11|2020|204
5217308971311738|9|2019|568
4929228528975615|8|2017|947
4929214308818241|12|2016|950
4532472014210546|4|2016|239
5401559425068037|3|2018|248
4539182275671780|12|2017|863
5279071620101844|3|2019|147
4716907162702610|9|2019|130
5519355066173353|8|2020|409
4532441352256536|1|2018|271
5366635784225484|3|2019|933
5506842459314145|8|2016|187
5524199029987373|4|2019|227
5463562649837919|3|2020|706
5566213523612921|11|2017|724
5143885997246757|7|2016|655
4532184120498762|7|2018|153
5153750830169896|8|2020|746
4929797810696576|5|2019|488
4716484022508173|7|2020|460
5161665367516279|5|2020|146
4929154126671663|5|2018|794
4929813656087588|1|2018|510
5148063489850966|11|2016|293
5560748485479948|10|2018|920
5220067052413954|4|2018|505
5158371654562697|10|2017|807
5103055387552358|10|2019|223
4485508454239391|9|2016|442
4716588459381381|1|2017|819
5340928199392762|7|2019|960
4916440456866741|5|2018|902
4532633823778292|1|2019|839
4916786317593035|12|2018|062
4716664744950528|3|2017|355
4716406272720034|12|2017|915
4539145993349419|9|2016|064
5516553930074970|7|2017|874
4916431183071713|9|2019|573
5106602402300581|5|2019|334
4532963940458506|5|2019|521
4916247934019870|4|2018|605
5504789142407384|9|2019|207
4929411589602621|10|2018|123
5313189880137973|2|2018|342
5162389983152406|3|2018|338
4716266171342904|9|2017|108
4485846630664193|4|2016|510
5307338459767326|7|2020|806
4916682860720176|2|2020|525
4916424597873360|1|2020|150
5356147633082837|2|2020|208
4716938114446451|6|2018|536
5368247913949329|12|2019|810
5340428277943966|1|2018|256
4485259162277014|4|2017|273
4716560123715575|9|2019|983
4532098943582158|10|2016|307
4716791308661959|9|2018|149
5356150137329910|3|2020|806
much more........haha^^
======================
 T10z1nh0 Aka Subkelz
T10z1nh0 Aka Subkelz
28 Domain Hacked By HagashTeam
| _ \ _ __ ___ _ __ __ _| |_(_) ___ _ __ | ___| |__ (_)_ __ __ _
| | | | '_ \ | _ \ '__| _` | __| || _ \| '_ \ | | | '_ \| | '_ \ | _` |
| |_| | |_) | __| | | (_| | |_| | (_) | | | | | |___| | | | | | | | (_| |
\___|| .__| \___|_| \__,_|\__|_|\___||_| |_| \____|_| |_|_|_| |_|\__,_|
|_|
https://twitter.com/AnonymousGlobo
28 Domain Hacked By HagashTeam #OpChina
https://twitter.com/HagashTeam
http://ww.sy.zhsh5000.com/OpChina.html
http://www.tjzdgg.cn/OpChina.html
http://www.topuunion.com/OpChina.html
http://www.wandaxj.com/OpChina.html
http://www.wanglin.zhsh5000.com/OpChina.html
http://www.wanglinshi.zhsh5000.com/OpChina.html
http://www.wangzhihe.zhsh5000.com/OpChina.html
http://www.wdd.zhsh5000.com/OpChina.html
http://www.wenyu.zhsh5000.com/OpChina.html
http://www.wxc.zhsh5000.com/OpChina.html
http://www.wyd.zhsh5000.com/OpChina.html
http://www.xgqp.nethttp://www.xianzaiwj.com/OpChina.html
http://www.xuguang.zhsh5000.com/OpChina.html
http://www.yinnong.com.cn/OpChina.html
http://www.yuanyongxiang.zhsh5000.com/OpChina.html
http://www.zhangdong.zhsh5000.com/OpChina.html
http://www.zhangyijun.zhsh5000.com/OpChina.html
http://www.zhaolei.zhsh5000.com/OpChina.html
http://www.zhimeichuju.com/OpChina.html
http://www.zhiyuandianli.com/OpChina.html
http://www.zhouhongyi.zhsh5000.com/OpChina.html
http://www.zhouyoulin.zhsh5000.com/OpChina.html
http://www.zhs.zhsh5000.com/OpChina.html
http://www.zhsh5000.com/OpChina.html
http://www.zhutiechuan.zhsh5000.com/OpChina.html
http://www.zm-kitchenware.com/OpChina.html
http://www.zqf.zhsh5000.com/OpChina.html
wzhtzz.com/OpChina.htmlzhsh5000.com/OpChina.html
=====================
 T10z1nh0 Aka Subkelz
T10z1nh0 Aka Subkelz
5000 Credit Card #OpChina @AnonymousGlobo http://www.portalhmarin.com.br/arquivos/downloads/37/OpChina.txt …
| _ \ _ __ ___ _ __ __ _| |_(_) ___ _ __ | ___| |__ (_)_ __ __ _
| | | | '_ \ | _ \ '__| _` | __| || _ \| '_ \ | | | '_ \| | '_ \ | _` |
| |_| | |_) | __| | | (_| | |_| | (_) | | | | | |___| | | | | | | | (_| |
\___|| .__| \___|_| \__,_|\__|_|\___||_| |_| \____|_| |_|_|_| |_|\__,_|
|_|
https://twitter.com/AnonymousGlobo
https://twitter.com/h4x0s
4929773699206423|1|2018|935
4485041577048093|8|2020|671
4716870829646481|9|2017|958
5187824835991479|1|2018|084
5357308140404125|4|2020|366
5536162068122134|1|2019|295
5501933374628332|1|2020|571
4532340587058933|8|2017|371
4485832955337151|10|2019|629
5597377569104755|3|2017|897
4916801150615603|7|2017|245
4716437219377398|10|2020|166
5435433642735473|4|2019|568
5591140166713709|7|2020|839
5463742099997179|7|2019|211
5305070417614215|6|2018|854
5244822844297681|3|2016|994
5283939000677456|3|2018|420
4532595500726136|9|2020|590
5277237799831618|8|2020|100
5364467155247653|9|2017|505
4485278974722132|12|2020|206
4916372407716206|8|2018|271
5378611326016331|2|2019|217
4916669993623302|12|2019|396
4485458598747596|12|2017|765
5176189692598806|11|2020|204
5217308971311738|9|2019|568
4929228528975615|8|2017|947
4929214308818241|12|2016|950
4532472014210546|4|2016|239
5401559425068037|3|2018|248
4539182275671780|12|2017|863
5279071620101844|3|2019|147
4716907162702610|9|2019|130
5519355066173353|8|2020|409
4532441352256536|1|2018|271
5366635784225484|3|2019|933
5506842459314145|8|2016|187
5524199029987373|4|2019|227
5463562649837919|3|2020|706
5566213523612921|11|2017|724
5143885997246757|7|2016|655
4532184120498762|7|2018|153
5153750830169896|8|2020|746
4929797810696576|5|2019|488
4716484022508173|7|2020|460
5161665367516279|5|2020|146
4929154126671663|5|2018|794
4929813656087588|1|2018|510
5148063489850966|11|2016|293
5560748485479948|10|2018|920
5220067052413954|4|2018|505
5158371654562697|10|2017|807
5103055387552358|10|2019|223
4485508454239391|9|2016|442
4716588459381381|1|2017|819
5340928199392762|7|2019|960
4916440456866741|5|2018|902
4532633823778292|1|2019|839
4916786317593035|12|2018|062
4716664744950528|3|2017|355
4716406272720034|12|2017|915
4539145993349419|9|2016|064
5516553930074970|7|2017|874
4916431183071713|9|2019|573
5106602402300581|5|2019|334
4532963940458506|5|2019|521
4916247934019870|4|2018|605
5504789142407384|9|2019|207
4929411589602621|10|2018|123
5313189880137973|2|2018|342
5162389983152406|3|2018|338
4716266171342904|9|2017|108
4485846630664193|4|2016|510
5307338459767326|7|2020|806
4916682860720176|2|2020|525
4916424597873360|1|2020|150
5356147633082837|2|2020|208
4716938114446451|6|2018|536
5368247913949329|12|2019|810
5340428277943966|1|2018|256
4485259162277014|4|2017|273
4716560123715575|9|2019|983
4532098943582158|10|2016|307
4716791308661959|9|2018|149
5356150137329910|3|2020|806
4916209647800574|12|2020|467
5537939752534248|2|2020|387
5106848752505887|5|2018|608
5401653125969337|4|2020|766
5214846759765909|7|2019|269
4716420744795490|8|2018|195
4929954557090659|1|2019|325
5194903252932041|2|2020|211
4532008298855984|3|2019|058
4916266757202454|11|2018|274
5453701761436827|1|2016|856
5480377258560366|9|2020|334
5114581164522881|7|2018|082
4485870876098452|10|2017|610
5141603514715507|6|2017|232
5190564729215610|8|2020|526
5408254075453324|2|2020|843
5239323259113510|12|2020|670
4916979440872604|8|2019|448
5459683042810000|4|2019|899
4539362416814412|3|2016|870
5543911453530637|4|2017|030
4539731015935663|8|2017|153
4916066081052405|2|2017|452
4539837434062649|3|2016|186
5435641106598126|1|2019|002
5341490264810912|5|2018|473
5107886803164394|8|2019|957
4539301779324478|9|2020|635
4556455871240541|7|2018|336
5320372893773338|4|2020|124
5379327671080744|3|2019|948
4916508967647618|11|2018|810
4929370592264193|10|2018|037
5496362206855003|6|2016|957
4716138329867464|8|2017|701
5569088098807859|2|2016|315
4485214202592930|1|2017|244
4716528105718974|5|2018|137
4539719881421199|9|2018|303
5429977828528001|9|2018|839
5323211155294715|4|2017|132
4929045333872732|5|2017|878
5536671090665282|5|2019|260
4539845707063764|4|2016|204
5549123643006296|12|2019|765
5447547439834052|3|2016|928
5317509535853284|5|2020|632
4916239627485310|7|2017|349
5443920548428997|8|2019|129
4485512700403926|4|2016|744
4532997930743451|8|2020|789
5252821510785770|8|2018|155
much more.......well^^
==================


http://pastebin.com/4m99Enug
Operation China: 161 domains of China Hacked http://pastebin.com/nqy1iGYJ We are here and we will stay! You should have expected for us. #AntiSec
soon we will repeat attacks Chinese websites
I am a hacker, hacktivist is not a criminal.. Hacking is art . We are the revolution . #Anonymous #AntiSec ..
============
==================
http://www.ibtimes.co.uk/anonymous-opisis-cloudflare-refuses-block-service-pro-isis-websites-1495758?utm_source=dlvr.it&utm_medium=social&utm_campaign=ibtimesuk
Anonymous #OpISIS: CloudFlare refuses to block service to pro-ISIS websites
US companies like CloudFlare have been criticised for providing services to websites containing jihadist material (Abubaraa). Web hosting and cybersecurity firms in the US and UK have responded to revelations provided by the hacktivist group Anonymous that their services are being used by Islamic State (Isis) to spread online propaganda.
A list of pro-Isis websites and their corresponding web hosts compiled by members of the Anonymous faction GhostSec included Google, Yahoo! and GoDaddy. According to GhostSec, "by far the largest offender" was CloudFlare.
Speaking with IBTimes UK , co-founder and CEO of CloudFlare, Matthew Prince, said that his company would not be blocking its service to websites listed, as it would mean submitting to "mob rule".
"Individuals have decided that there is content they disagree with but the right way to deal with this is to follow the established law enforcement procedures. There is no society on Earth that tolerates mob rule because the mob is fickle," Prince said.
The question of internet censorship
CloudFlare does not itself host the content of the websites, meaning blocking its service would not actually make the content go away. The service instead protects sites from malicious traffic and cyber threats, meaning without it websites would be more vulnerable to attacks from Anonymous."We're the plumbers of the internet," Prince said. "We make the pipes work but it's not right for us to inspect what is or isn't going through the pipes. If companies like ours or ISPs (internet service providers) start censoring there would be an uproar. It would lead us down a path of internet censors and controls akin to a country like China."
Since the list was released several of the companies responsible for hosting the controversial content have removed the websites, including UK-based Web Hosting UK (WHUK).
Frank Tighe, CTO of WHUK's parent company Hyperslice, has said that pro-Isis content breaches WHUK's terms of service - which states that content must not contain any material that is obscene, offensive, hateful or inflammatory - and that the websites listed by GhostSec have since been removed.
"We take matters like this very seriously and actively remove websites such as this, that breach our acceptable use policy as soon as we are made aware of them," told IBTimes UK .
"Whilst we try to ensure that all our customers adhere to our acceptable use policy at all times, we host hundreds of thousands of websites and logistically speaking it's extremely difficult for us to keep track of the content of all of them all of the time."
The criticism against CloudFlare includes claims that it is accepting blood money, however Prince believes that the sites listed use the firm's free service and that its position is not financially motivated.
A campaign has even been set up against CloudFlare accusing it of encouraging illegality by allowing criminals to hide behind their servers.
"I don't approve of this because DoS attacks are illegal," Daniel Brandt, founder of CrimeFlare, told IBTimes UK . "On the other hand, CloudFlare is notoriously arrogant and unresponsive to legitimate complaints, and I understand why some Op Isis supporters feel that they have to resort to this."
Attacks from both sides
CloudFlare has previously faced criticism for protecting websites associated with Anonymous, however Prince asserts that their service is only removed if told to do so by a court of law."The irony is there is no organisation that we have had more requests to terminate services for than the hacking group Anonymous, including from government officials - which we have not done without following the proper legal process," Prince said.
CloudFlare claims to have not received a single law enforcement request to block any of the sites listed by Ghostsec.
This argument has been frequently dismissed by Anonymous, who claim that the vast majority of these accounts and websites are used to spread propaganda with the hope of recruiting more people to its cause - not to communicate valuable military strategic information.
Whether or not sites are removed, the methods employed by Isis and its supporters mean that the content almost inevitably reappears somewhere on the internet. The question of whether or not it should be policed remains contentious, though the enormity of the task is recognised from all sides .
"Playing whack-a-mole with content can be a real challenge," Prince said. "There are an almost infinite number of hosting services these people can use. It's very difficult to make content go away."
==================
*Note This Sharing By Anonymous~
#OpChina
 Namaste
Namaste
''Hong Kong thief wolf Leung chun-ying slaves ignore the demands of seven million people,
Indiscriminate use of political means to hurt people who fight for democracy and freedom in Hong Kong,
Unfair and not open electoral system!
Corruption was 50 million slaves thief wolf Leung chun-ying use political means darkness,
Slander students participate in a public umbrella movement, detain them, intimidate them !!
These shameful acts only beast than the evil cult of the Communist Party of the continent will be dry drawn slaves Leung chun-ying,
Leung chun-ying slaves would come to this loss of constancy turn, lose conscience, only know how corrupt and confuse black and white, do not take care of the people's livelihood, cold blood poison discriminate against lower class people! !FuCk @ -
This is the beginning ...
We look forward to Anonymous chivalrous Legion to 689 @ slaves thief wolf Leung chun-ying of corruption 50 million darkness transactions and all his bank accounts, and the family bank property dig a clear light, put it flat as a beggar, in retaliation for its cold blood to treat a bully for a positive human rights, movement made Bullying on pay all costs!
Conscience and justice witness the great legion of Anonymous chivalrous to justice mainland and Hong Kong people!
Until it possible for human rights and fair and open political system, political kingpins freedom and democracy Huanjiao votes!
689 @ thief wolf Leung chun-ying resign... OR ELSE! Beast! Disgrace human dignity !!
Anonymous omnipotent !
Anonymous everywhere !
Anonymous does not forgive !
Anonymous will not forget !
We are Anonymous !
We look forward to .... '
To our great Anonymous chivalrous great legion, preach up to the international
Our small life to witness this important moment in history
Really feel honored and grateful...
Yours sincerely``
Melody.Blog thanksgiving Sincerely~
http://melody-free-shaing.blogspot.com/2015/04/update4our-friendly-dear-anonymous.html
==============
''香港賊狼梁振英奴隸漠視7000000人們的訴求,
胡亂運用政治手段對待曾為香港人們爭取民主自由,
公平公開選舉制度!
卻被貪污50000000的賊狼梁振英奴隸利用黑暗政治手段,
誣蔑一眾參與雨傘運動的學生們,扣留他們,恐嚇他們!!
這些可恥的行為只有禽獸不如的大陸邪教共產黨奴隸梁振英才會幹得出,
這種失去常性,失掉良知,只懂貪贓枉法,混淆黑白,對民生不照顧,冷毒地歧視低下階層的人們!@FuCk !@-

這才是開始...
我們期待匿俠義軍團把689@賊狼梁振英奴隸貪污50000000的黑暗交易和他所有銀行賬戶,家屬銀行財產掘個清光,把牠扁為乞丐,以報復牠冷毒對待爭取人權正面的運動所作的惡霸欺凌行為付上一切代價!
良知和公義見證,偉大的匿名俠義軍團為大陸和香港人們伸張正義!
直至人們得以人權和公平公開政制,自由選票與民主的政治首要人物換角!
689@賊狼梁振英下台...否則後果自負!畜牲!恥辱人類的尊嚴!!
匿名無所不能
匿名無處不在
匿名不會原諒
匿名不會忘記
我們是匿名
期待我們....'
為我們偉大的匿名俠義軍團而宣揚於國際上
我們渺小的人生能見證這重要的歷史時刻
真的感到光榮與感恩...
此致
Melody.Blog仝人敬上~
http://melody-free-shaing.blogspot.com/2015/04/update4our-friendly-dear-anonymous.html
==============
'' Esclaves Hong Kong Leung Chun voleur loup-battant ignorer les demandes de sept millions de personnes,
L'utilisation aveugle de moyens politiques de blesser les gens qui luttent pour la démocratie et la liberté à Hong Kong,
Déloyale et non ouvrir système électoral!
La corruption était de 50 millions d'esclaves voleur loup Leung Chun-ying utiliser des moyens politiques ténèbres,
étudiants de calomnie participent à un mouvement parapluie publique, les détenir, les intimider !!
Ces actes honteux ne bête que le culte pervers du Parti communiste du continent sera esclaves tirées sèches Leung Chun-ying,
Leung Chun-ying esclaves viendrait à cette perte de constance son tour, de conscience perdre, ne savent corrompu et confondre noir et blanc, ne prenez pas soin de la vie du peuple, le poison de sang-froid, la discrimination contre les gens de la classe inférieure! ! Merde @ -
Ce est le début ...
Nous sommes impatients de Anonyme Légion chevaleresque à 689 @ esclaves voleur loup Leung Chun-ying de corruption 50.000.000 transactions obscurité et tous ses comptes bancaires et les biens de la banque familiale creuser un claire lumière, mis à plat comme un mendiant, en représailles pour son de sang-froid pour traiter un tyran pendant droits positifs, le mouvement fait l'intimidation sur la rémunération de tous les coûts!
Conscience et la justice témoignent de la grande légion de Anonyme chevaleresque à la justice continentale et de Hong Kong les gens!
Jusqu'à il possible pour les droits humains et le système politique juste et ouverte, liberté politique des barons et de la démocratie votes Huanjiao!
689 @ voleur loup Leung Chun-ying démissionner ... ou bien! Bête! La dignité humaine Disgrace !!
Anonyme omnipotent!
Anonyme partout!
Anonyme ne pardonne pas!
Anonyme ne oubliera pas!
Nous sommes anonymes!
Nous avons hâte de .... '
A notre grande Anonyme chevaleresque grande légion, prêcher jusqu'à l'international
Notre petite vie pour assister à ce moment important dans l'histoire
Vraiment sentir honorés et reconnaissants ...
Veuillez sincerely``
Melody.Blog grâces Sincèrement ~
http://melody-free-shaing.blogspot.com/2015/04/update4our-friendly-dear-anonymous.html
==============
''香港泥棒の狼レオンチョン-YING奴隷は、七万人の要求を無視する
香港で民主主義と自由のために戦う人々を傷つけるための政治的手段の無差別使用、
不正と選挙制度を開けないで!
汚職は5000万奴隷泥棒狼レオンチョン英政治手段の闇を使用した、
中傷の学生が公共の傘運動に参加し、彼らを拘留、それらを威嚇!!
大陸の共産党の邪悪なカルトよりのみ獣これらの恥ずべき行為はドライ描か奴隷レオンチョン·英となり、
レオンチョン-YINGスレーブは、恒常ターンのこの損失に来て良心を失い、唯一知っているどのように腐敗した黒と白のを混同し、人々の生活の世話をしない、冷たい血液毒は下層階級の人々を差別するだろう! !くそ@ -
これが始まりです...
私たちは、そのための報復では、乞食のように平らに入れ、明確な光を掘る奴隷泥棒狼破損のレオンチョン·英5000万闇取引およびすべての彼の銀行口座、および家族の銀行のプロパティ@ 689に匿名騎士軍団を楽しみにしています冷たい血液が正の人権のためのいじめっ子を処理するために、運動はすべてのコスト賃金にいじめをした!
良心と正義は正義の本土と香港の人々に騎士道匿名の偉大な軍団を目撃!
人権と公正でオープンな政治システム、政治キングピンの自由と民主主義Huanjiao投票のためにそれが可能になるまで!
泥棒狼レオンチョン英@ 689辞任...またはELSE!ビースト!恥辱人間の尊厳!!
匿名全能!
どこにでも匿名!
匿名許しません!
匿名忘れません!
私たちは、匿名である!
私たちは楽しみにして.... '
我々の偉大な匿名騎士道偉大な軍団に、国際的なまでの説教
歴史の中で、この重要な瞬間を目撃する私たちの小さな命
本当に光栄と感謝を感じる...
ユアーズsincerely``
Melody.Blog感謝敬具〜
http://melody-free-shaing.blogspot.com/2015/04/update4our-friendly-dear-anonymous.html
==============
'' Hong Kong fur lupus Leung Chun-Ying servi ignorare id quod ad septem milia hominum,
Politica per indifferentem usum popularem, qui pro libertate nocent in Hong Kong,
Iniqua et non aperiam collegium electorum!
Corruptio autem servi L million fur lupus Leung Chun-Ying politicis uti mediis tenebris:
Hec et alumni participant in publico umbrella motus, retineantur, ut terreret eos !!
Haec flagitia solum animal quam illud malum ad cultum communistarum factionem rei continentis erit siccum ducatur seruorum Leung Chun-Ying,
Leung Chun-Ying servitia venire ad constantiam, turn detrimentum hoc, conscientia suam extra, modo sciat corrupta, et confundunt, nigrum et album, non curare de populo ad sustentationem vitae, in frigore sanguis venenum discernere viliore populus! ! Catapultam @ -
Hoc est initium de ...
Expectamus ad legionem Anonymous NOBILIS DCLXXXIX @ lupus Leung Chun-Ying fur servi sint corruptionis a L million tenebris et rerum omnium ripam rationibus, et res usque ad ripam a familia clara luce, posuit plana prius quia mendicus erat, in vicem eius frigido tractare queant affirmativus iurium IMPORTUNUS in motu facto omnimodo reddere!
Perhibente conscientia, et justitia, magnus ad legionem Anonymous NOBILIS continenti ad iustitiam et Hong Kong populus!
Donec id fieri potest, quia iura humana et aperta et pulchra ratio politica, politica democratia et libertatem kingpins Huanjiao votes!
@ DCLXXXIX fur lupus Leung Chun-Ying ... AUT abdicare! Pecus! Ignominia ad hominis dignitatem, !!
Anonymous omnipotent!
Anonymous ubique!
Marcus autem non dimiseritis!
Anonymous non obliviscar!
Anonymous sumus!
Expectamus .... "
NOBILIS magnus Marcus maximi legione ad praedicandum internationalis
Vita nostra parum refert, historiae hodierna
Et vere grati sentire honorati ...
Tua sincerely``
Melody.Blog sincere ~ gratiarum actione
http://melody-free-shaing.blogspot.com/2015/04/update4our-friendly-dear-anonymous.html
==============
'홍콩 도둑 늑대 양조위 천 잉 노예, 칠백만명의 요구를 무시
홍콩에서 민주주의와 자유를 위해 싸우는 사람들을 다치게하는 정치적 수단의 무분별한 사용,
부정과 선거 제도를 열 수 없습니다!
부패는 5 천만 노예 도둑 늑대 양조위 천 잉 정치적 수단의 어둠을 사용했다,
비방 학생들이 공공 우산 운동에 참여, 그들을 억류, 그들을 위협!
이 수치스러운 행위 건조 그린 노예에게 양조위 천 잉 될 것 대륙의 공산당의 악마 숭배보다 만 짐승,
양조위 천은 잉 불변의 차례를 잃게 양심의이 손실을 와서 노예 만 사람들의 생활을 돌봐하지 않는, 어떻게 손상 알고 흑백 혼란, 차가운 혈액 독 낮은 수준의 사람들을 차별! 제길 @ -
이것은 시작에 불과하다 ...
우리는 부패 50000000 어둠 거래와 그의 모든 은행 계좌의 노예 도둑 늑대 양조위 천 잉 @ 689 익명 기사도 군단을 기대하고, 가족 은행의 속성은 분명 빛을 파고에 대한 보복, 거지 같은 평평 넣어 그 차가운 피가 긍정적 인 인간의 권리를 위해 깡패를 치료하기 위해, 운동은 모든 비용 지불에 괴롭힘을했다!
양심과 정의는 정의 본토와 홍콩 사람들에게 기사도 익명의 큰 군단을 목격!
인간의 권리와 공정하고 열린 정치 체제, 정치 킹핀의 자유와 민주주의 Huanjiao 투표 가능한 그것은까지!
도둑 늑대 양조위 천 잉 @ 689 사임 ... 또는 ELSE! 야수! 치욕 인간의 존엄성!
익명 전능!
사방 익명!
익명 용서하지 않습니다!
익명 잊지 않을 것입니다!
우리는 익명이다!
우리는 기대 ... '
우리의 위대한 익명 기사도 큰 군단에, 국제까지 설교
우리의 작은 생활은 역사에서 중요한 순간을 목격합니다
정말 영광과 감사하는 마음이 들죠?
당신의 sincerely``
Melody.Blog 감사 감사 ~
http://melody-free-shaing.blogspot.com/2015/04/update4our-friendly-dear-anonymous.html
==============
*Note This Sharing By Anonymous~

#OpChina
 Namaste
Namaste
'' Hongkongo ŝtelisto lupo Leung Chun-Ying sklavoj ignori la postulojn de sep milionoj da homoj,
Indiscriminada de uzo de politikaj rimedoj vundi homoj kiuj batalas por demokratio kaj libereco en Hong Kong,
Maljusta kaj ne malfermi voĉdona sistemo!
Korupteco estis 50 milionoj da sklavoj ŝtelisto lupo Leung Chun-Ying uzi politikajn rimedojn mallumo,
Kalumnio studentoj partoprenas en publika ombrelo movado, retenu ilin, intimidar ilin !!
Tiuj hontinda aktoj nur besto ol la malbono kulto de la Komunista Partio de la kontinento estos seka desegnita sklavoj Leung Chun-Ying,
Leung Chun-Ying sklavoj venus al tiu perdo de konstantecon siavice, perdi konsciencon, nur scias kiel korupta kaj konfuzi nigra kaj blanka, ne zorgos pri la popola vivteno, malvarma sango veneno diskriminacii malsupra klaso homoj! ! Fuck @ -
Ĉi tiu estas la komenco ...
Ni rigardas antaŭen al Anonymous kavalireca Legio al 689 @ sklavoj ŝtelisto lupo Leung Chun-Ying de korupteco de 50 milionoj mallumo transakcioj kaj lia tuta bankaj kontoj, kaj la familio banka posedaĵo fosi klara lumo, metu ĝin plata kiel almozulo, en reprezalio por lia malvarma sango por trakti bully por pozitivaj homaj rajtoj, movado faris intimidación sur salajro ĉiakoste!
Konscienco kaj justeco atestas la granda legio de Anonymous kavalireca al justeco ĉeftero kaj Hongkongo homoj!
Ĝis eblas al homaj rajtoj kaj justa kaj malferma politika sistemo, politikaj kingpins libereco kaj demokratio Huanjiao voĉdonoj!
689 @ ŝtelisto lupo Leung Chun-Ying rezigni ... Alie! Besto! Malaltigu homa digno !!
Anonima ĉiopova!
Anonima ĉie!
Anonymous ne pardonas!
Anonymous ne forgesos!
Estas Anonymous!
Ni rigardas antaŭen al .... '

Por nia granda Anonima kavalireca granda legio, prediku al la internacia
Nia malgranda vivo atesti tiu grava momento en historio
Vere sentas min honorigita kaj dankema ...
Yours sincerely``
Melody.Blog danka Sincere ~
http://melody-free-shaing.blogspot.com/2015/04/update4our-friendly-dear-anonymous.html
==============
-Update(4).Shating by My dear Anonymous---China Blocks Reuters Website After DDoS Attack On The Great Firewall of China!! Posted on March 21, 2015 by Waqas ]---更新(4).由偉大俠義匿名軍團發佈---"中國塊路透社網站的DDoS攻擊中國的長城防火牆後 發表於 2015年3月21日 由瓦卡斯] !!**All The World Lauguage**-
http://melody-free-shaing.blogspot.com/2015/04/update4our-friendly-dear-anonymous.html
*---Update(4).Our friendly dear Anonymous legion of chivalry on the mainland Communist devil evil cult sensation Chinaman attack big action! Mainland Communist devil evil cult Chinaman corruption and instructions Hong Kong thief wolf @Leung chun-ying suppress slave 'Scholarism '', ''the Council of '' more absurd extreme of the Communist Party of the General asked the court to approve the peoples of 20 at the time accounted for a busy area cleared of demonstrators were arrested, a criminal contempt of court proceedings?! Details see text [reported by Apple Daily] - and this second round sniper devil cult Communist mainland Chinaman did not humanitarian law and justice not to dissidents severely beaten, and even destroyed the lives of big revenge is coming! - we pro Love friendly Anonymous released a chivalrous Legion (1) .NamasteAnonNamaste - # OpChina Hello Government, you have failed as expected: d [-_-] b ^^ Mirror http://dlvr.it/9L44Hd] via Doemela]-(2).AnonymousAnonymousGlobo - # OpChina: 5000 CC leaked, maybe some needy institution is in need of donations;)
[http://www.portalhmarin.com.br/arquivos/downloads/37/OpChina!.txt ...] #AntiSec #Anonymous]- (3).T10z1nh0 Aka Subkelz @ h4x0s - 28 sites of China hacked ByHagashTeam #OpChina [ http://pastebin.com/H6ew5nwM]-(4).T10z1nh0 Aka Subkelz @ h4x0s - 5000 Credit Card #OpChinaAnonymousGlobo [http://www.portalhmarin.com.br/arquivos/downloads/37/OpChina.txt...]- please enjoy anonymity with great precision posture ~^^-
---更新(4).我們親爱友好的匿名俠義軍團對大陸邪教惡魔共產黨支那人轟動攻擊的大行動!大陸邪教惡魔共產黨支那人貪污和指令香港賊狼@梁振英奴隸打壓''學民思潮'',''學聯聯會'',更有荒謬極的共產黨妖魔律政司要求法庭批准對20名在佔旺區清場時被捕的示威者,展開刑事藐視法庭的法律程序?!詳見內文[由蘋果日報報導]-而這次第二輪狙擊大陸邪教惡魔共產黨支那人沒人道沒公義沒法律和把異見人士打得頭破血流,甚至殘害生命!大報復來臨了-我們親爱友好的匿名俠義軍團發佈出(1).Namaste @AnonNamaste--#OpChina Hello Government, you have failed as expected: d[-_-]b ^^ Mirror http://dlvr.it/9L44Hd] via @Doemela ]-
(2).Anonymous@AnonymousGlobo--#OpChina: 5000 CC leaked, maybe some needy institution is in need of donations! ;)[ http://www.portalhmarin.com.br/arquivos/downloads/37/OpChina.txt…] #AntiSec #Anonymous]- (3).T10z1nh0 Aka Subkelz @h4x0s--28 sites of China hacked By @HagashTeam #OpChina http://pastebin.com/H6ew5nwM]-(4).T10z1nh0 Aka Subkelz@h4x0s-- 5000 Credit Card #OpChina @AnonymousGlobo[ http://www.portalhmarin.com.br/arquivos/downloads/37/OpChina.txt…]-請各位用欣賞匿名偉大的精確姿勢~^^
**All The World Lauguage**-
http://melody-free-shaing.blogspot.com/2015/04/update4our-friendly-dear-anonymous.html
===Melody.Blog===FOLLOW FOLLOW===>/
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
















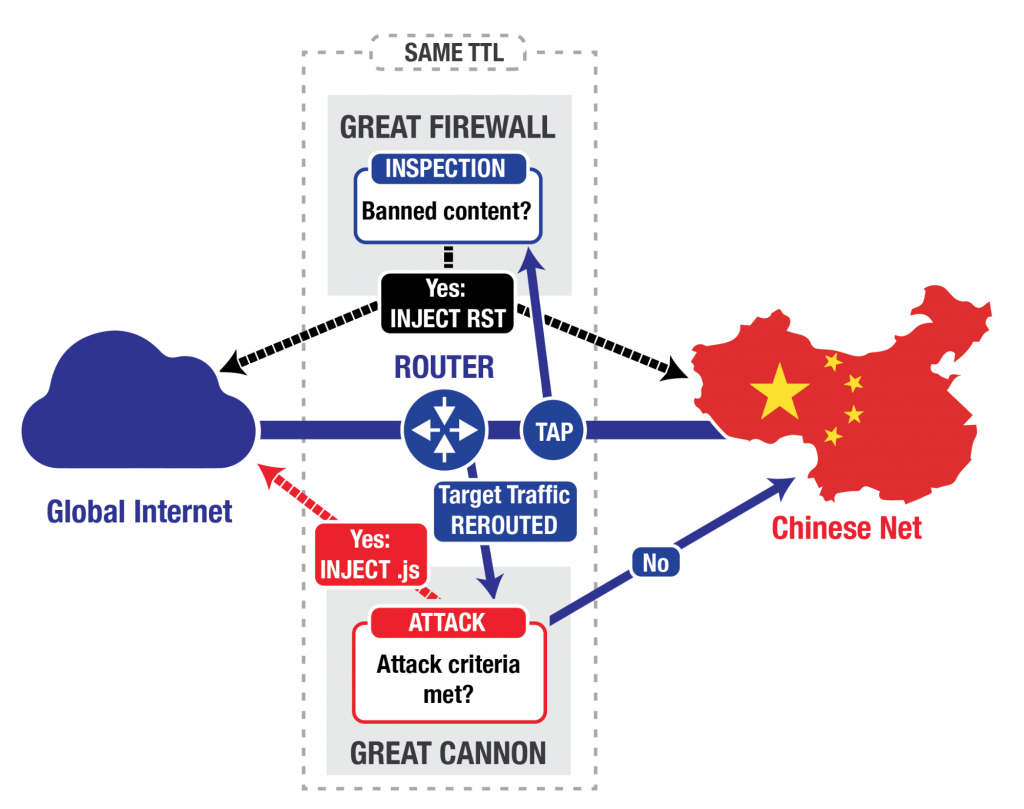
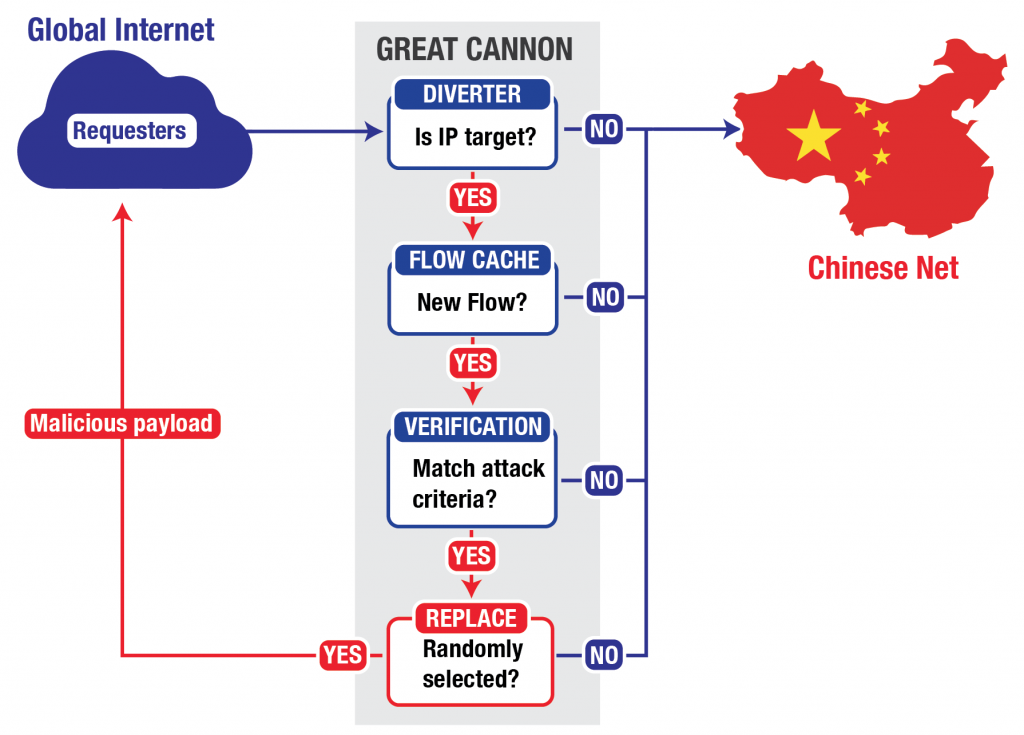





沒有留言:
張貼留言
window.___gcfg = {
lang: 'zh-CN',
parsetags: 'onload'
};